This blog focuses on security event management within the AWS cloud and presents some options for implementing a security analytics solution. Security Analytics in the AWS Cloud
The basic role of security analytics remains the same in the cloud, but there are a few significant differences. Arguably the biggest, is the effective blast radius of an incident can be far greater in the cloud.
“I built my datacenter in 5 minutes” is a great marketing slogan and bumper sticker that AWS have. However, if someone compromises an IAM role with admin privileges, or worse, your root account, they can completely destroy that datacenter in well under 2 minutes. Having an effective strategy to identify, isolate and contain a security incident is paramount in the cloud.
Amazon Web Services prides itself on its security and compliance stature and often states that security is Job Zero. Nonetheless, customers need to be mindful that this is a shared responsibility model. Whilst AWS agrees to provide physically secure hosting facilities, data storage and destruction processes and a vast array of tools and services to protect your applications and infrastructure, it is still ultimately the customer’s responsibility to protect and manage the services they run inside AWS. To name just a few of these :
- Managing your own firewall rules including ACLs and Security Groups.
- Encrypting your data both in transit and at rest ( inc. managing keys )
- Configuring and managing IPS and WAF devices
- Virus/Malware detection
- IAM events ( logins, roles etc )
The list goes on… and with the speed that AWS releases new products and features, it is important to be able to keep on top of it all. We know AWS and a number of their technology and managed services partners are well aware of this and provide some really useful tools to help manage this problem.
We will focus on the following AWS services and then discuss how we can incorporate them into a strategic Security Analytics solution:
IAM ( Identity & Access Management ) is an absolute must for anyone who is serious about securing their environment. It provides authenticated and auditable access to all of your resources. Through the use of users, group, roles and policies you can create fine grained permissions and rules. It also allows you to federate credentials with an external user repository.
CloudTrail can log all events from IAM and is one of the most important services from a SIEM perspective. CloudTrail is a web service that records all kinds of API calls made within IAM, and most other AWS services. It is essential from an auditing perspective and in the event you need to manage a security event. See this link for a full list of supported services that also links back to the relevant API reference guide. Additionally, this link provides detailed information about logging IAM events to CloudTrail.
VPC Flow Logs is a fairly recent addition to the AWS inventory but has long been a feature request from the security community. Whilst Security Groups and ACLs have long provided customers with the ability to control access to their VPC, they weren’t previously able to see the logs generated. A key part of a SIEM solution is the ability to process “firewall” logs. It’s all well and good knowing that an authorized user can access a particular service but it can also be very useful to know what requests are getting rejected and who is trying to access protected resources. In this respect, Flow Logs now gives customers a much clearer view of the traffic within their VPC. Rather conveniently, Flow Logs data is processed by CloudWatch Logs
CloudWatch Logs is an extension of the CloudWatch monitoring facility and provides the ability to parse system, service and application logs in near real time. There is a filtering syntax that can be used to trigger SNS alerts in the event of certain conditions. In the case of applications running on EC2 instances, this requires a log agent to be installed and configured. See this link for how to configure CloudTrail to send events to CloudWatch Logs. This service does somewhat impinge upon the functionality of existing log management products such as SumoLogic and Splunk, however, as we’ll explain in a separate post, there is still a good argument for keeping your third party tools.
Config is a service that allows you to track and compare infrastructure changes in your environment over time and restore them if necessary. It provides a full inventory of your AWS resources and the facility to snapshot it into CloudFormation templates in S3. It also integrates with CloudTrail, which in turn integrates with CloudWatch Logs to provide a very useful SIEM function. For example, if a new Security Group gets created with an open access rule from the internet an alert can be raised. There is quite a bit of functional overlap with CloudTrail itself but Config can also be very useful from a change management and troubleshooting perspective.
Here are a couple of real world examples that make use of these services.
Example 1
This scenario has a rogue administrator adding another unauthorized user to the admin role inside the IAM section of the AWS Console.
If we have configured CloudTrail then this event will automatically get logged to an S3 bucket. The logs will be in JSON format and this particular entry would look something like this. An IAM role can be assigned to CloudWatch Logs to allow it to ingest the CloudTrail events and a filter can be applied to raise an alarm for this condition. You can use SNS to initiate a number of possible actions from this.

Some other possible events ( there are many ) that we may want to consider monitoring are:
- AuthorizeSecurityGroupIngress – someone adding a rule to a security group
- AssociateRouteTable – someone making a routing change
- StopLogging – someone stops CloudTrail from recording events
- Unauthorized* – any event that returns a permission error
- “type”:”Root” – any activity at all performed under the root account
Example 2
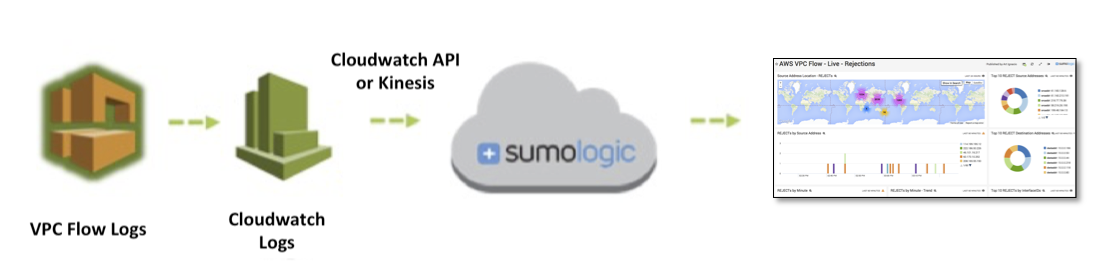
This is a very high level overview of how VPC Flow Logs, and essentially all the services we’ve outlined in this post, can be integrated with a third party log management tool.
In my opinion, whilst CloudWatch Logs does provide some very useful and low cost monitoring capabilities, there are quite a few dedicated tools provided by AWS technology partners that offer a number of advantages in terms of configurability, functionality and usability. SumoLogic appears to be one of the first vendors to integrate with VPC Flow Logs and is very easy to get up and running with.
As always, thank you for taking the time to read this post. I’d also like to thank David Kaplan, Security and Compliance Principal at AWS Australia, for his valuable input to this piece.
This blog was contributed by our partner friends at Cloudten. It was written by Richard Tomkinson, Principle Infrastructure Architect. Cloudten Industries © is an Australian cloud practice and a recognized consulting partner of AWS. They specialize in the design, delivery and support of secure cloud based solutions.
For more information on Sumo Logic’s cloud-native AWS solutions please visit AWS Integrations for Rapid Time-to-Value.






