
Trying to stay ahead in cybersecurity can feel a bit like juggling gas-powered chainsaws while riding a unicycle across a tightrope—dangerous, noisy, and not for the faint of heart. Thankfully, security information and event management (SIEM) tools are your safety harness—keeping you steady, secure, and just far enough from the edge that you’re not plunging headfirst into the abyss of breached data, regulatory fines, and sleepless nights.
Two major acts in this three-ring adrenaline circus are Sumo Logic Cloud SIEM and Splunk Enterprise Security. While Splunk is known for its deep analytics and flexible search, a closer look reveals that Sumo Logic brings the agility, automation, and real-time awareness needed to thrive, not just survive, under pressure.
Sumo Logic SIEM vs. Splunk Enterprise Security
| Feature | Splunk Enterprise Security | Sumo Logic Cloud SIEM |
| First-seen rules | Manual set-up, requires complex maintenance | Native, automated detection |
| Rule tuning and updates | Manual cloning, fragmented updates | Integrated tuning with persistent updates |
| Real-time streaming | Scheduled searches, latency risk | True real-time streaming |
| Signal correlation | Basic signal-level correlation | Advanced, automated entity correlation |
| Automation and playbooks | Requires additional purchase (Splunk Phantom) | Built-in automation and enrichment |
| Search performance | Performance issues during usage spikes | Consistent high-performance scaling |
| Real-time alerts | Scheduled, delayed alerts | Instant, real-time alerts |
| Identification of anomalies and critical log events | Manual complex queries | Built-in, intuitive tools such as LogReduce & Log Compare |
| App catalog | Extensive but largely community-supported | Officially supported, vetted apps |
Behind the curtain: Why these differences matter
First-seen rules
Early anomaly detection is critical to preventing threats from escalating. Quickly identifying previously unseen threats allows security teams to address issues proactively before significant damage occurs.
- Splunk Enterprise Security lacks out-of-the-box “first-seen” detection, forcing analysts to manually build detection rules, manage multiple lookup tables, and rely on scheduled searches.
- Sumo Logic Cloud SIEM provides these capabilities natively, automatically alerting on new entities and behaviors without tedious manual intervention, dramatically streamlining early threat detection.
Dedicated rule tuning and updates
Properly tuned detection rules significantly improve accuracy and efficiency, reducing false positives and enabling security analysts to focus on genuinely critical threats.
- With Splunk, rules must be cloned, modified separately, and manually updated, resulting in fragmented and challenging maintenance, which can introduce blind spots and operational inefficiencies.
- Sumo Logic offers integrated tuning expressions directly atop its provided content, ensuring customizations persist across automatic updates. This greatly simplifies maintenance and keeps detection capabilities current and effective.
Real-time streaming
Immediate processing of security events ensures timely threat detection and response, significantly reducing an organization’s vulnerability to rapidly evolving cyber threats.
- Splunk Enterprise Security depends on scheduled searches, which can introduce latency and potentially result in missed alerts, increasing risk exposure.
- Sumo Logic SIEM employs a true real-time streaming engine that immediately analyzes events, significantly reducing latency risks and enhancing overall response effectiveness.
Cross-correlation of disparate signals
Accurate correlation of multiple signals ensures better threat detection and fewer false positives, enabling quicker and more precise responses to complex threats.
- Splunk Enterprise Security offers correlation capabilities, but its primary focus is on basic signal-level correlation, requiring manual configuration for notable events and risk-based alerting. Cross-correlating multiple disparate signals to a single entity is challenging and typically necessitates dashboard interaction or cumbersome ‘event sequencing’ procedures.
- Sumo Logic automatically correlates multiple signals into coherent insights, simplifying and accelerating threat analysis, and enhancing the accuracy and speed of incident resolution.
Automation, playbooks, and enrichment
Automating response procedures minimizes human error and improves response efficiency, allowing teams to swiftly contain and remediate security incidents.
- Splunk requires an additional purchase (Splunk Phantom) for automation and enrichment capabilities, resulting in higher operational complexity and cost.
- Sumo Logic integrates automation, enrichment, and structured playbooks directly into the platform, significantly reducing operational costs, complexity, and response time.
Search performance
Efficient search performance is crucial for rapid threat investigation and resolution, ensuring that critical incidents are promptly addressed.
- Splunk can struggle under improperly scoped environments or unexpected spikes in usage, causing delays in threat investigation, potentially leaving security teams blind at critical moments. This is largely due to its legacy architecture, which is not cloud-native and lacks the elasticity needed to dynamically scale resources on demand. As a result, organizations often face performance bottlenecks during peak times unless they over-provision ahead of time—a costly and inefficient workaround.
- Sumo Logic consistently scales search capabilities with usage demands, ensuring reliable and rapid threat investigation even during high data-volume incidents.
Real-time alerts and searches
Timely threat detection relies heavily on immediate alerting to enable rapid response, crucial for minimizing potential damage from active threats.
- Splunk relies on scheduled alerts and searches, creating potential visibility gaps and delays in addressing emerging threats. This limitation stems from Splunk’s non-cloud-native architecture, which restricts its ability to process data streams in real time. Because it cannot dynamically scale compute and processing resources like true cloud-native platforms, Splunk is forced to rely on scheduled searches to maintain system performance. This introduces inherent delays and reduces visibility during fast-moving security events, which can be detrimental in environments where every second counts.
- Sumo Logic supports immediate, continuous real-time alerts and searches, eliminating potential response delays and significantly enhancing overall threat management.
Identification of anomalies and critical log events
Rapid identification of log anomalies significantly enhances threat investigation, allowing security teams to quickly identify the root cause of incidents.
- Splunk lacks native capabilities to easily identify anomalies, requiring users to craft complex queries manually, which can be time-consuming and prone to error.
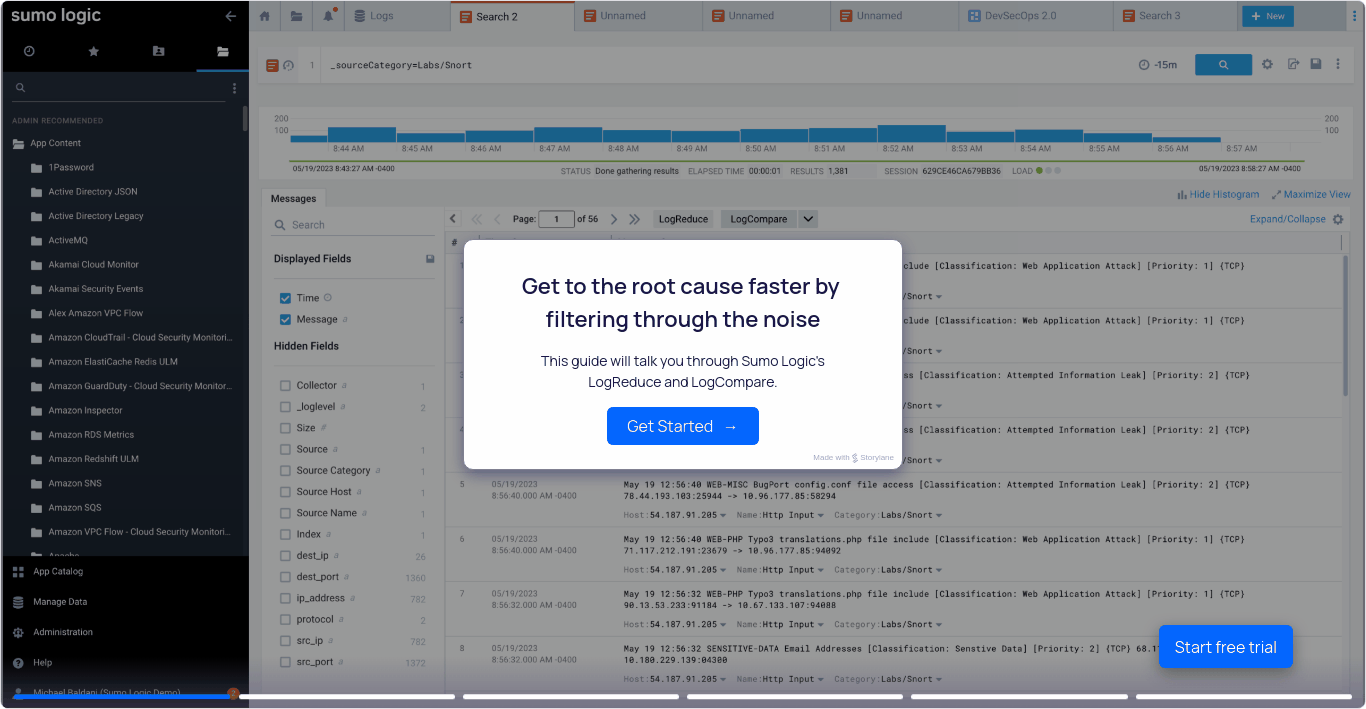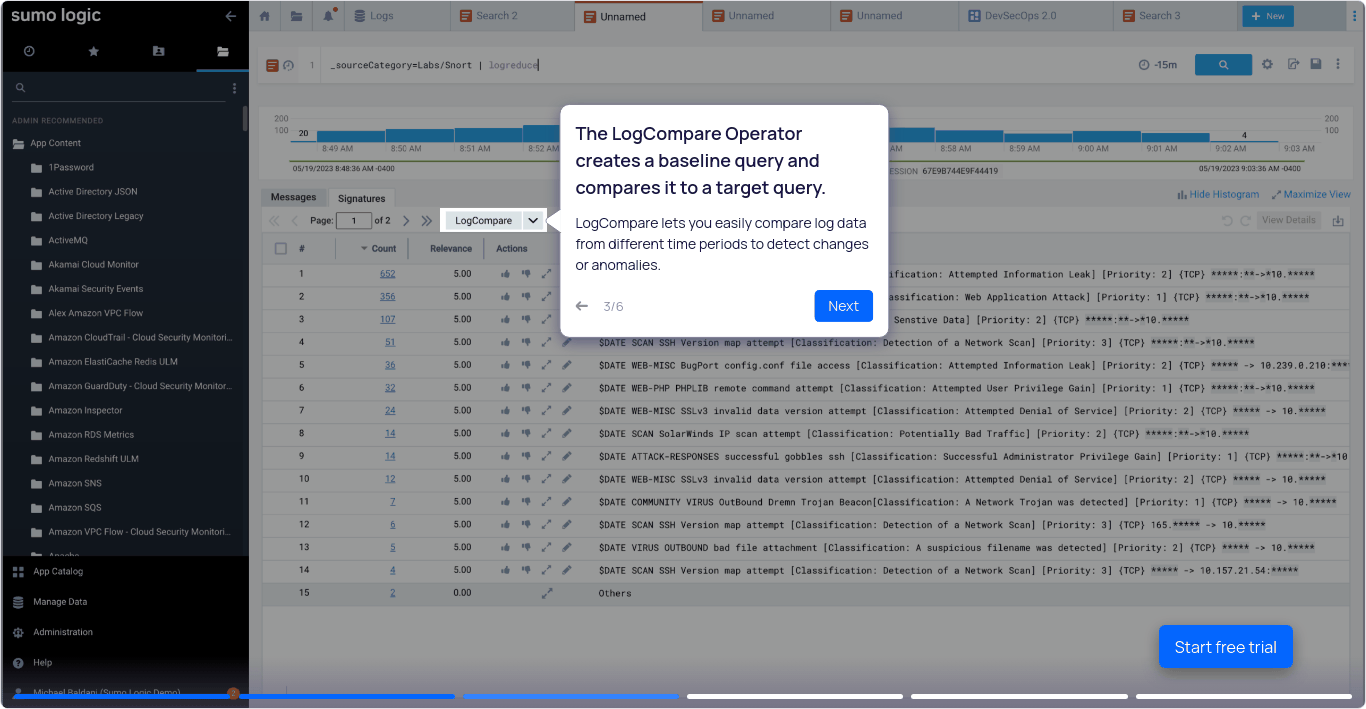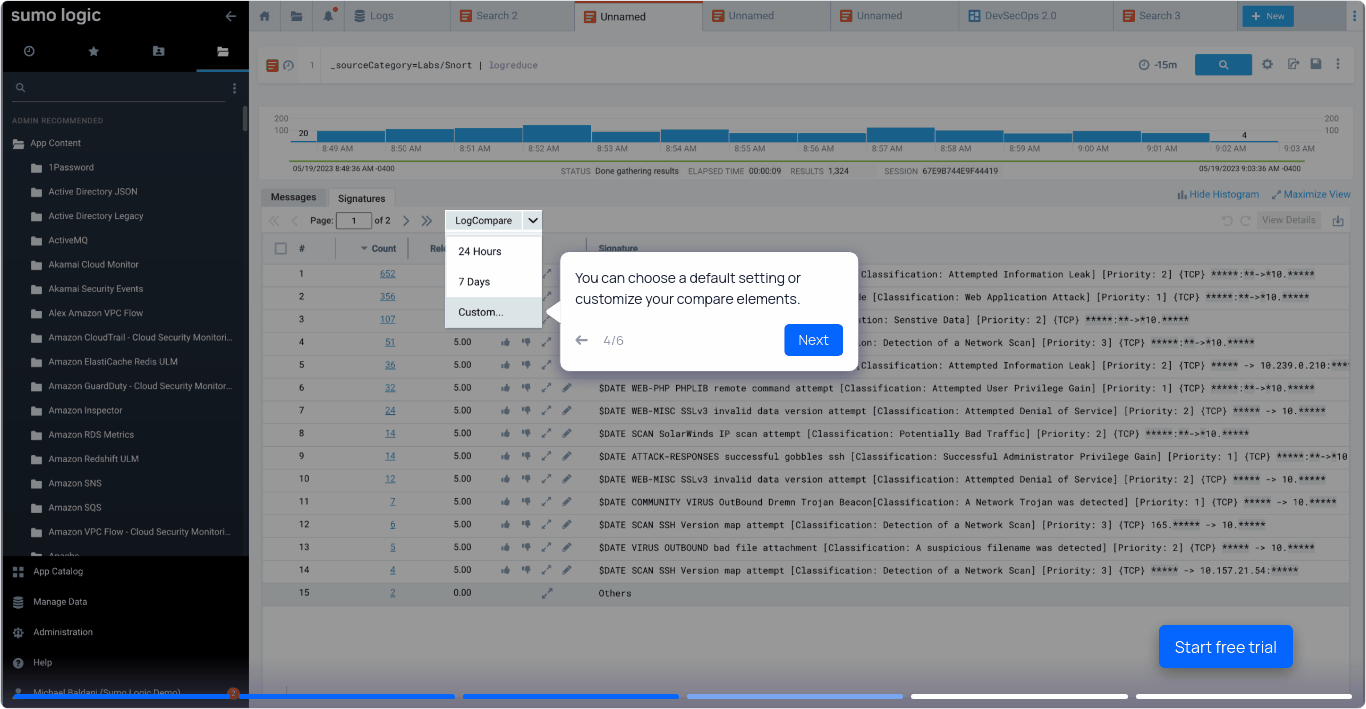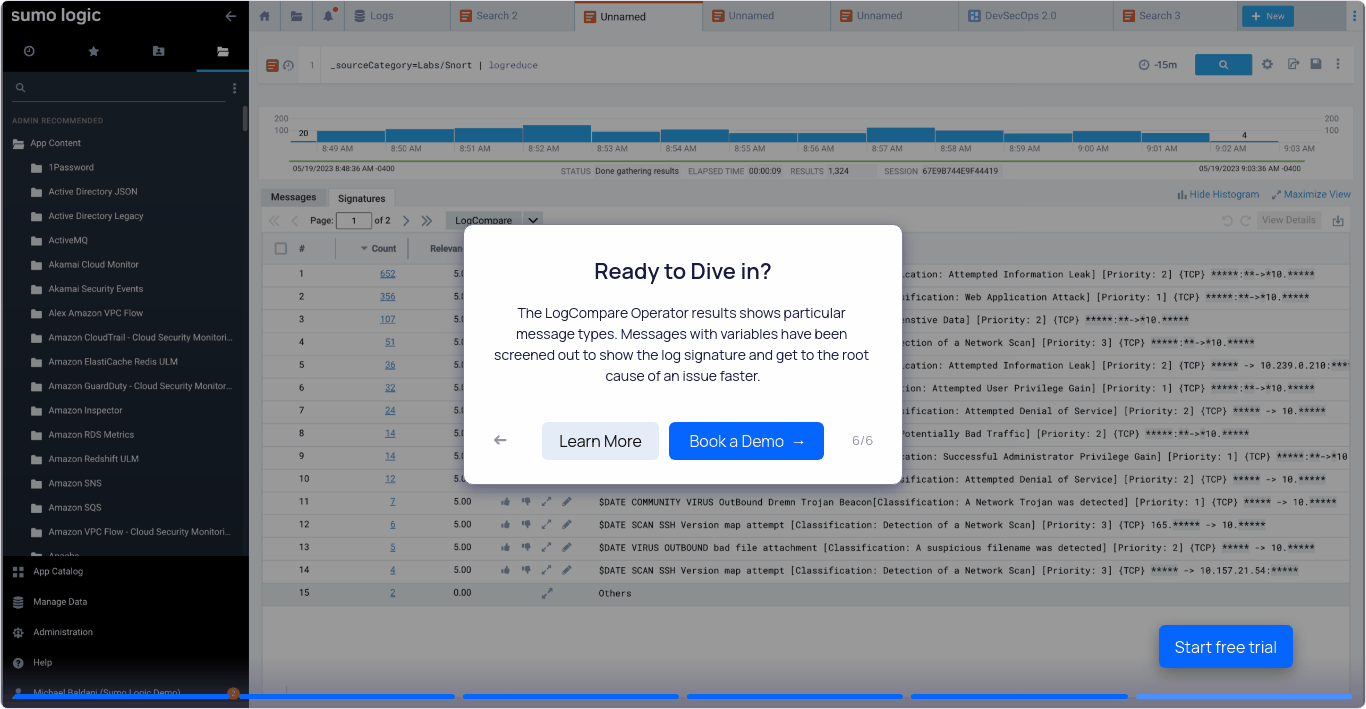
- Sumo Logic provides intuitive LogReduce and LogCompare tools, which simplify and accelerate investigations by instantly highlighting significant events and anomalies.
App Catalog
Reliable and vetted apps ensure secure and seamless platform integrations, enhancing both security and operational efficiency.
- Splunk’s app catalog (SplunkBase) is extensive but dominated by community-developed, unsupported apps. These apps pose security and performance risks that could compromise an organization’s overall cybersecurity posture.
- Sumo Logic maintains a robust catalog of officially supported and vetted apps, providing secure and reliable integration options that minimize risk, streamline operations, and improve users’ time-to-value.
Final act: Choose your safety net wisely in the adrenaline circus of cybersecurity
When deciding between Sumo Logic Cloud SIEM and Splunk Enterprise Security, the differences aren’t just technical; they’re survival tactics in a nonstop, high-speed security performance. Cloud SIEM stands out with native detection rules, streamlined rule tuning, real-time detection, automated correlation, and built-in automation tools. These aren’t just features. They’re your safety net when your juggling/unicycle/tightrope act gets real.
If your goal is long-term agility in the high-energy environment that is cybersecurity, Sumo Logic SIEM is built for the spotlight. It scales, automates, and reacts in real-time, keeping your team confidently balanced through the chaos. Splunk, by comparison, struggles to keep pace from behind the curtain.
See Sumo Logic in action. Request a demo.




