Explore modern threat detection and investigation
Threat detection, investigation, and response (TDIR) in Cloud SIEM now includes the power of Dojo AI—bringing explainable intelligence to every stage of the workflow. Advanced analytics, automation, and integrated threat intelligence help identify risks early, streamline investigation, and drive decisive action.
Dojo AI: Accelerating security decisions
Sumo Logic Dojo AI is a multi-agent AI system built to power intelligent security operations and incident response. It is designed to act autonomously, keeping human analysts in the loop while continuously adapting to evolving threats.
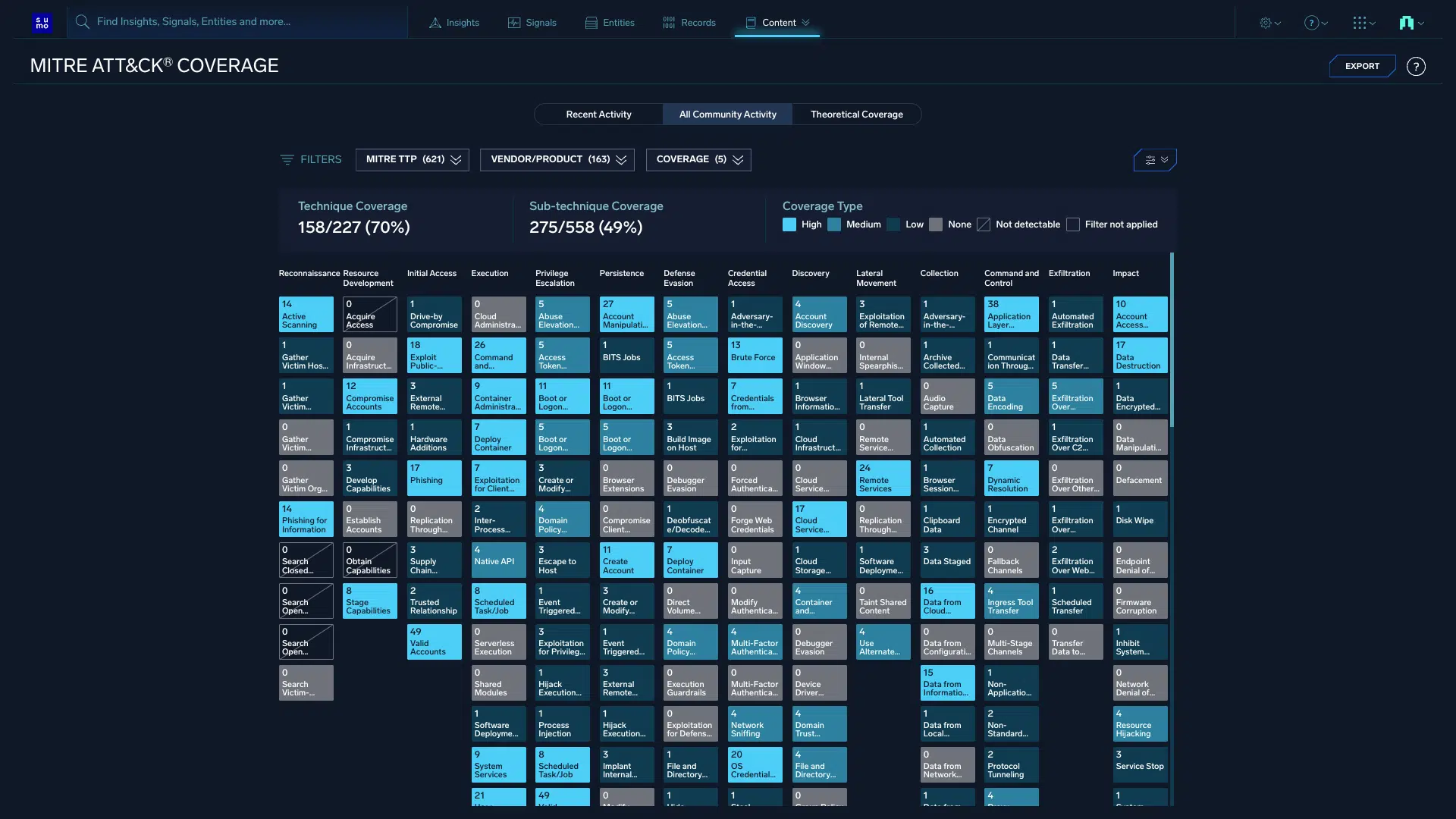
MITRE ATT&CK alignment
Instantly understand the scope of detection with industry-leading 80% TTP coverage from our MITRE ATT&CK Coverage Explorer, offering real-time insights on adversary tactics, empowering security teams to optimize rules and align defenses effectively.
Insider threat detection
Detect insider threats with confidence using UEBA baselining. Sumo Logic learns behavior patterns in minutes and uses historical baselines to flag anomalies like unusual access or data movement—reducing noise and improving accuracy.
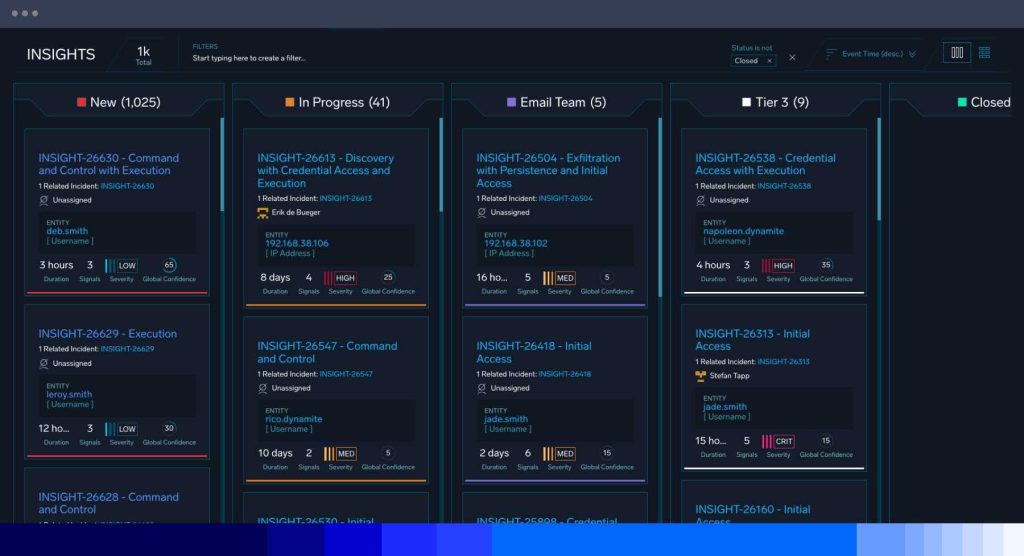
Real-time streaming and enrichment
Cloud SIEM, powered by over 900 customizable rules, streamlines threat detection and response with reduced mean time to detect (MTTD) and alert management effort. Use real-time global threat intelligence to enrich all your high-severity alerts, with built-in premium feeds and input to bring your own feed for full context during triage.
AI-driven triage
The SOC Analyst Agent, within Dojo AI uses agentic AI to streamline triage and investigation. It delivers verdicts on alert severity and collects related activity into a clear context, helping analysts quickly understand impact and scope. By filtering out noise and repetitive reviews, analysts stay focused on real threats and respond more effectively, with consistent outcomes across teams.
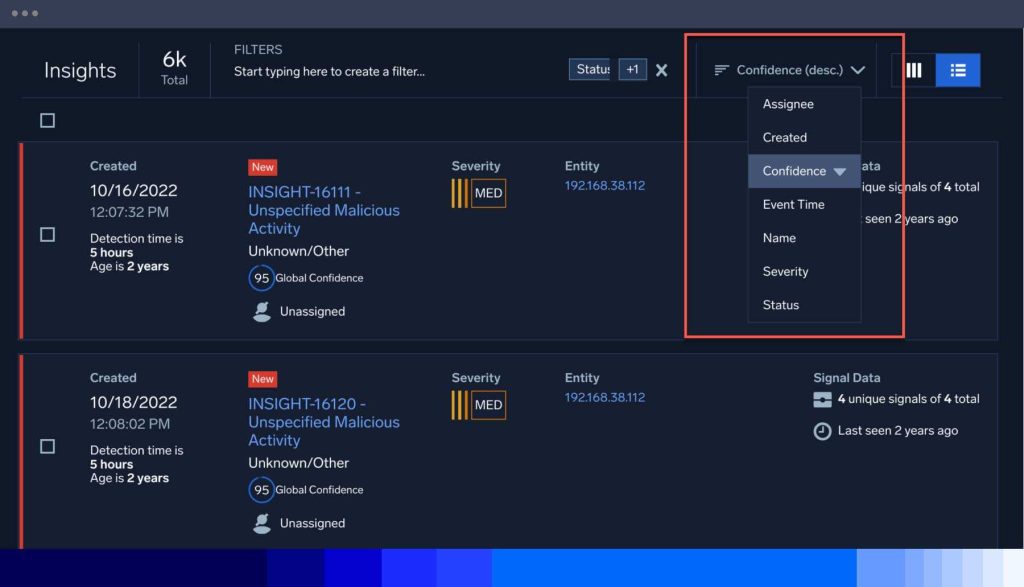

Entity Timelines and Entity Relationship Graphs
Focus on the central entity in a given Insight, along with any other entities that have had contact or communication within the designated period, to easily determine the blast radius at a glance. The Entity Timeline in Cloud SIEM provides a chronological view over a three-day period, helping track its actions before, during, and after incidents. The Entity Relationship Graph visualizes connections between the central entity and other entities within the same timeframe. Investigate cybersecurity incidents with a detailed, organized view of entity interactions and activities.
Instant remediation
Quickly prioritize, investigate, and better understand potential security threats with playbooks from our Automation Service that adds deeper context for investigations and automates notification workflows. You can easily execute response actions such as resetting an account or adding a domain to the firewall rules without leaving the Cloud SIEM user interface.
Additional resources

Gartner Critical Capabilities report

Brown Bag: Threat Hunting

Fine-tuning Cloud SIEM detections through machine learning

MSSP achieves 1,000% improvement in alert fidelity

Automating insider threat monitoring

Unified SIEM dashboard automates security investigations
FAQ
Still have questions?
Threat detection allows a security team to quickly and accurately identify potential threats to the network, applications, or other assets within the network. This capability is essential for IT security analysts to respond effectively to incidents and mitigate damage.
Identifying threats early allows IT teams to respond in real-time, which is essential for protecting network assets. Without timely threat detection, organizations risk data breaches and system compromises.
Threat detection focuses on:
- Identifying threats quickly and accurately
- Understanding potential threats in the cyber environment
- Employing effective security tools and response strategies to mitigate damage
Cybersecurity professionals face multiple challenges, including:
- Endpoint Protection: Managing security across diverse devices, especially with remote work and BYOD policies.
- Network Detection: Monitoring complex, encrypted networks to identify malicious activity.
- Unknown Threats: Handling advanced threats like AI-powered attacks that evade traditional detection.
- Tool Sprawl: Managing and integrating multiple security tools effectively.
- Staffing Challenges: Addressing a shortage of skilled cybersecurity professionals and leveraging third-party detection services if needed.
Sumo Logic helps organizations aggregate data, analyze patterns, and configure real-time alerts, allowing for automated response and faster recovery. Its platform leverages advanced machine learning and data protection to strengthen threat detection across cloud infrastructures
Here are some differentiating factors that set Sumo Logic apart from other solutions:
- Cloud-native architecture: Sumo Logic is built on a cloud-native architecture, which means it is purpose-built for the cloud and designed to handle large-scale, high-velocity data ingestion without infrastructure management.
- Log and machine data analytics: Sumo Logic specializes in analyzing and correlating log and machine data from various sources, including systems, applications, network devices, and cloud services.
- Real-time threat intelligence feeds and leverages machine learning algorithms, enriching security event data for more accurate and proactive threat detection.
- Anomaly detection and behavioral analytics: Sumo Logic applies advanced analytics techniques, including machine learning and behavioral analytics, to detect anomalies and identify suspicious patterns of activity. It establishes baselines for normal behavior and alerts security teams when deviations or unusual activities are detected, helping to identify potential threats or insider attacks.
- Comprehensive data correlation and investigation that allows security teams to connect security events across different data sources.
- Cloud security visibility into cloud environments, including public cloud platforms like AWS, Azure, and GCP, with pre-built dashboards and analytics tailored for cloud security monitoring.
- Automated threat detection and incident response that automate the detection of security events, generates real-time alerts and triggers predefined workflows for incident response, enabling faster and more efficient incident resolution.
- Collaboration and SOC integration: Sumo Logic supports collaboration among security teams by providing centralized dashboards, shared workspaces, and incident management features. It facilitates integration with Security Operations Centers (SOCs) and existing security toolsets, enabling seamless workflows and information sharing for effective threat detection and response.
- Compliance and audit support with pre-built compliance dashboards, reports, and log analysis capabilities that assist in demonstrating adherence to security standards and regulations.


