Think Sumo Logic is only for query language pros? Think again. Whether you’re deep into JSON logs or just trying to make sense of a Linux error message, these five time-saving hacks turn anyone into a log-searching ninja, no regex, no complexity, just clicks. From instantly parsing values to filtering down with a tap, these tips will help you troubleshoot faster, work smarter, and feel more confident in your observability game. You’ve got logs, now it’s time to put them to work.
Hack #1: Parse selected key (JSON)
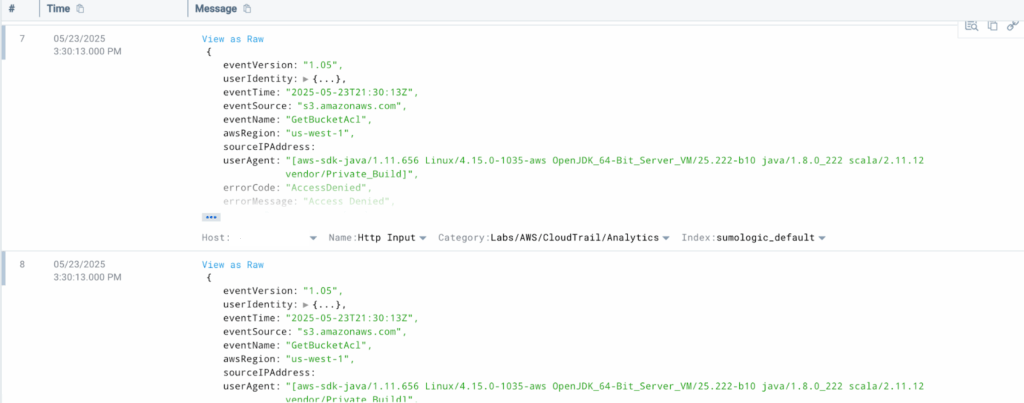
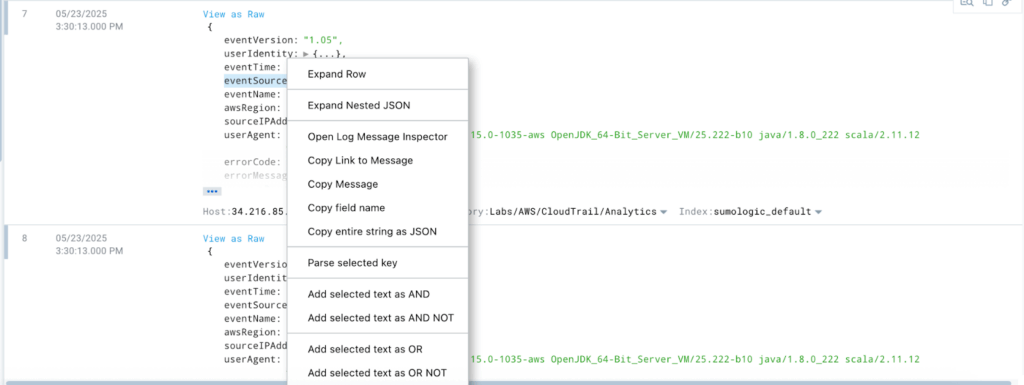
Got JSON logs staring back at you? For example, CloudTrail logs, and you want to parse a key without writing any code. Don’t stress, just right-click and select ‘Parse Selected Key’ to add a new line. With this handy trick, you can instantly parse the key you need, no code required. It’s like having a built-in cheat code for structured data.
And viola, this is how your query would look now!
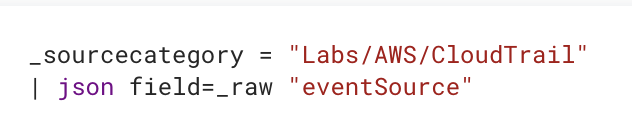
Hack #2: See percentage of values
Curious about what’s popping up most in your logs? No need to build a full query, just left-click the field on the left and boom: top ten values, ready to go. It’s like instant insights, with zero effort.
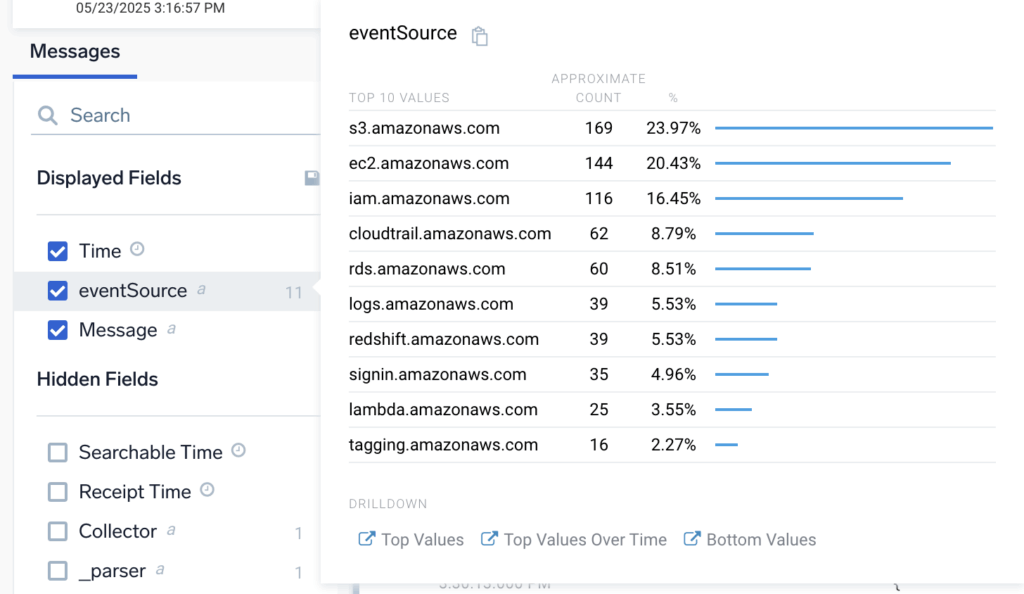
Really helpful to see top IP addresses, or event sources from the logs.
Hack #3: Filter down into a value with a click
Found an interesting value in your top ten Amazon services coming into Sumo Logic? Want to zoom in fast? Just click it, and Sumo Logic adds the filter for you. It’s like saying, “Just show me the good stuff”, and Sumo Logic listens.
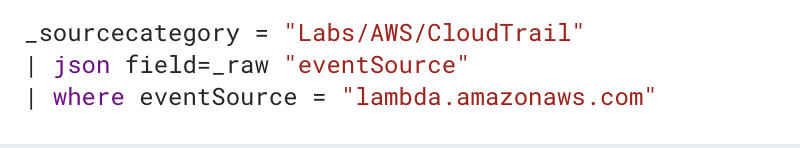
Need to laser into Lambda logs to debug latency issues? You can click the lambda.amazonaws.com value from the top ten list, and ta-da! A new line filtering to that value will be made.
This is the new query:
Hack #4: Expand nested JSON
Tired of clicking open every little arrow to see what’s hiding in your logs? Right-click and hit “Expand Nested JSON” to open it all up in one go. It’s the fastest way to turn a mystery blob into something readable.
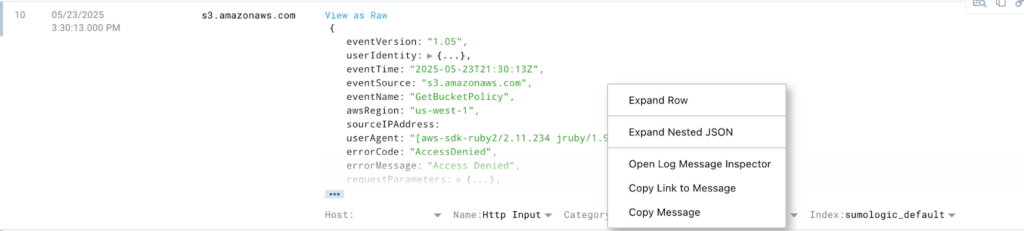
With a couple of clicks, you will now see the whole JSON structure from this log.
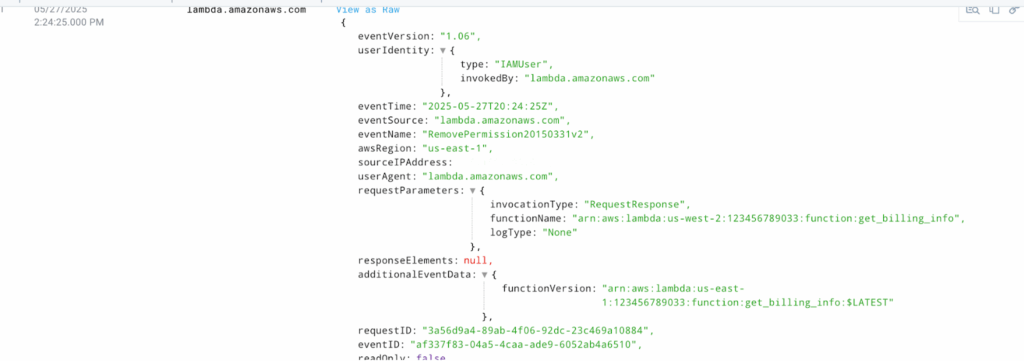
Hack #5: Parse unstructured logs with the UI
So far, we’ve been living in the land of JSON, but what if your logs are a bit more… wild? No problem. This hack helps you wrangle unstructured logs without knowing a lick of regex.
Got some messy error logs from a Linux server? You’re just a few clicks away from clean, structured fields, no wizardry required.
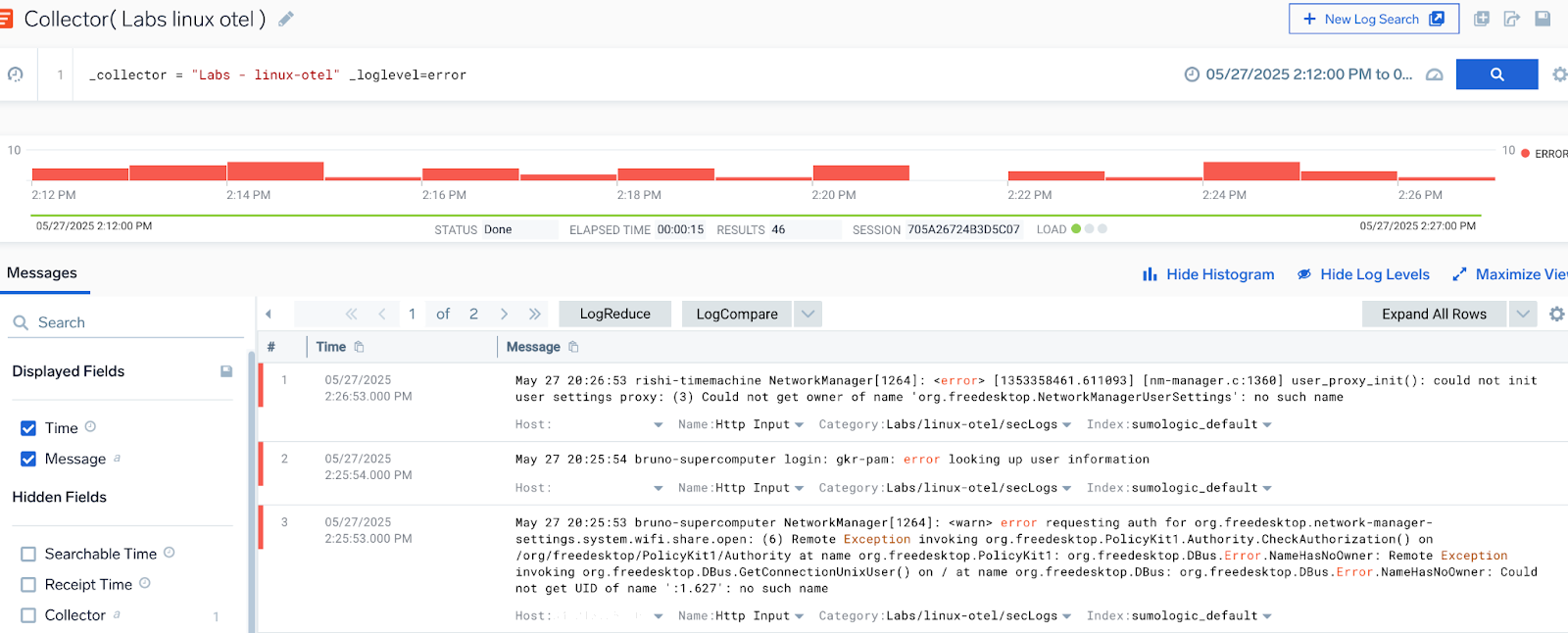
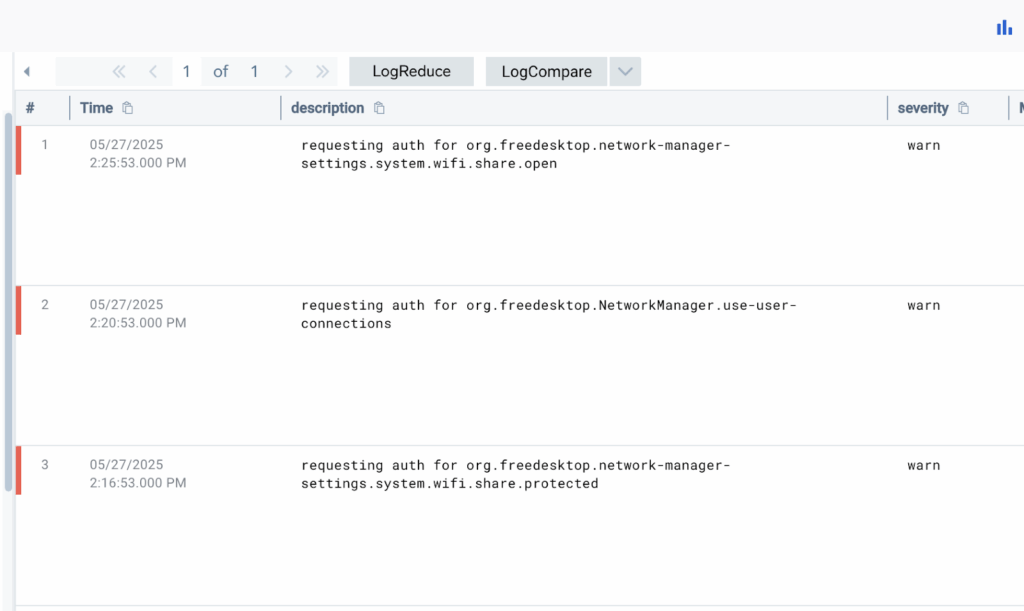
Select the text you want to divide into fields. For example, take the Network Manager logs and the error message.
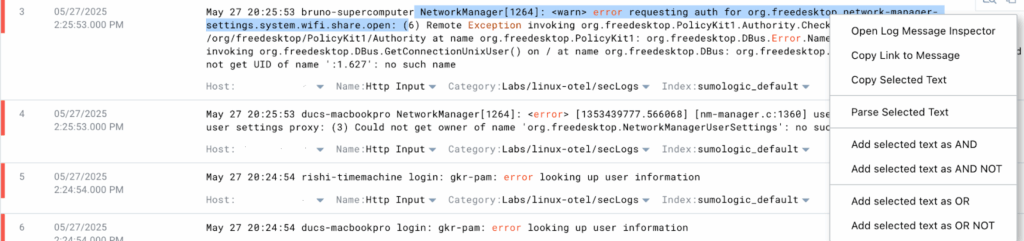
You will now see the Parse Text screen:
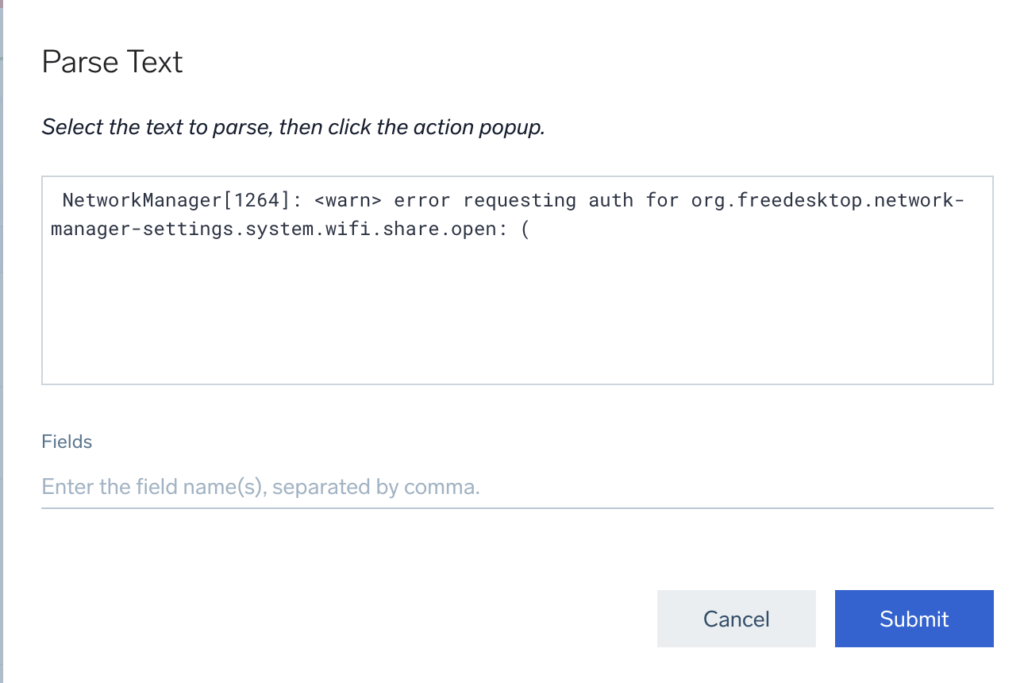
Select whatever value you want to extract from this string.
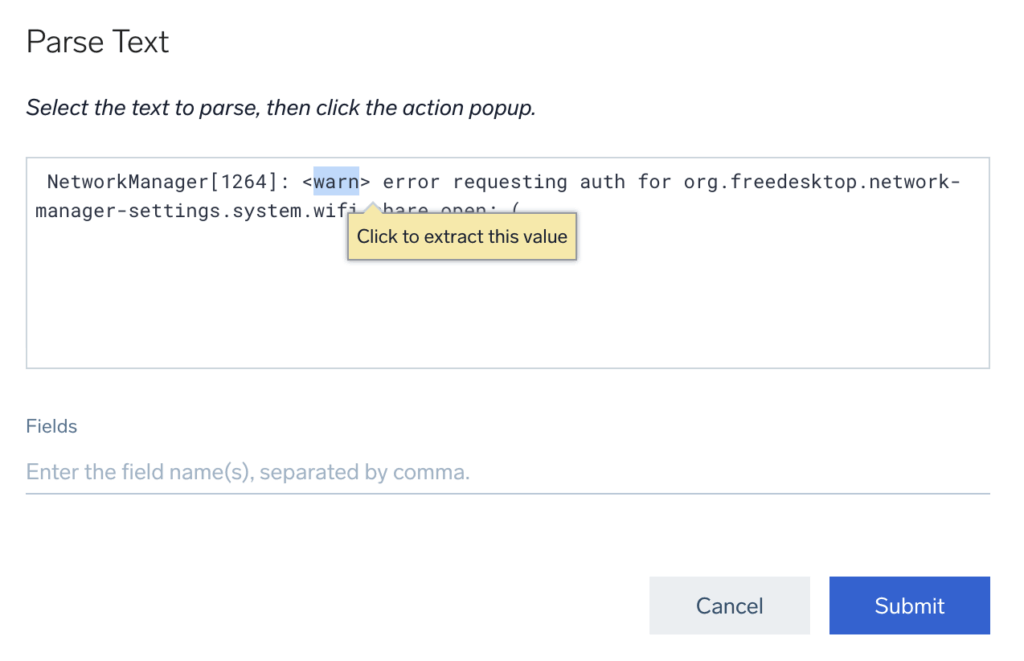
Now do the same exercise for the message after the error. The value will be replaced with a wildcard, and you will name the field. In this case, the field names are severity and description.
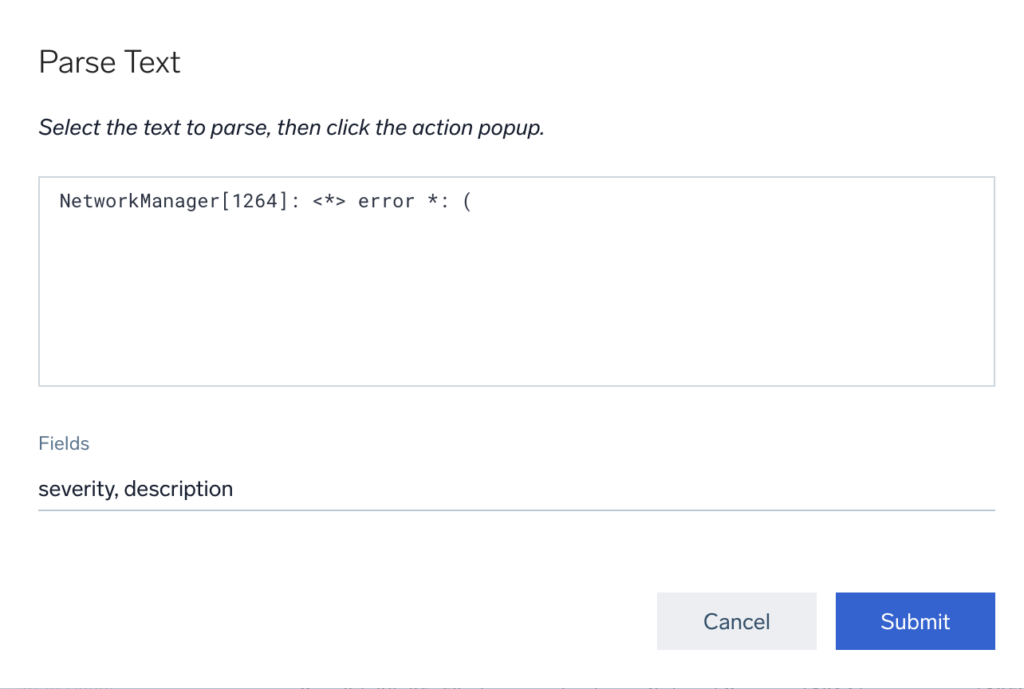
And now, click Submit. An easily made query line!
Query:
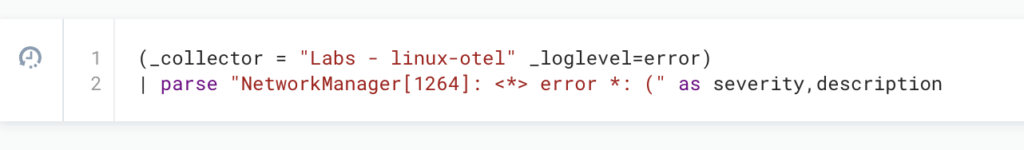
Results:
And just like that, we’ve unlocked five simple hacks to make your Sumo Logic experience faster, easier, and way more powerful. Whether you’re navigating structured JSON or decoding messy logs from a server, these tricks help you skip the heavy lifting and get straight to the insight. No complex queries, no stress, just clicks, filters, and a whole lot of “oh wow, that was easy.”
Now go forth and parse with confidence. And this is just the beginning. Sumo Logic’s full of clever little shortcuts waiting to be discovered.
Try it yourself today. Happy log hunting!