What is MTTI?
Mean time to identify (MTTI) is a key performance indicator, or metric, for incident response and cyber security. It represents the average time it takes for an organization to identify that a security incident or breach has occurred. MTTI is a crucial metric because the faster an organization can detect and identify a security incident, the quicker it can respond and mitigate the potential impact. It is critical in enhancing an organization’s overall cyber security posture and incident response capabilities.
Key takeaways
- MTTI directly correlates with an organization’s organization’s overall cybersecurity posture and incident response capabilities.
- MTTI is calculated by taking the sum of the time intervals between the occurrence of each security incident and its identification and then dividing that sum by the total number of incidents.
- Sumo Logic provides capabilities that contribute to faster incident detection and response, ultimately helping to reduce MTTI.
Why does MTTI matter?
MTTI matters because it directly impacts an organization’s ability to respond to security incidents promptly, mitigate their impact and maintain a resilient cyber security posture. It is a key indicator of how well an organization can detect and address threats in a timely manner.
MTTI is a critical metric in cybersecurity and incident response for the following reasons:
Reduces the impact of security incidents
A shorter MTTI is associated with reduced damage, data loss and disruption caused by security incidents.
Accelerates incident response
When security teams can quickly identify and confirm an incident, they can respond faster.
Limits unauthorized access
A shorter MTTI helps identify unauthorized access more quickly, allowing security teams to take immediate steps to contain and remediate a cyber attack before further harm is done.
Prevents data breaches
Rapid detection allows organizations to stop or mitigate data exfiltration attempts, protecting sensitive information.
Minimizes downtime and system outages
A shorter MTTI helps minimize the impact of security issues on business operations so incident response teams can restore systems to normal operation faster.
Meets compliance requirements
A shorter MTTI demonstrates that an organization can quickly detect and respond to security incidents, contributing to compliance with regulatory requirements.
Enhances cyber resilience
A shorter MTTI ensures a rapid and effective response to security incidents, reducing the overall impact on the organization.
Improves forensic analysis
Rapid identification of security incidents allows for more effective forensic analysis so security teams can investigate the incident, gather relevant information and understand the attack vectors and tactics.
Builds trust and reputation
Demonstrating a capability to identify and respond to security incidents quickly signals to customers, partners, and stakeholders that an organization has a trustworthy security posture.
Saves costs
The costs associated with a security incident can escalate rapidly. A shorter MTTI can lead to cost savings by limiting the extent of the damage, reducing the time and resources needed for incident response and minimizing the overall financial impact on the organization.
How do you calculate MTTI?
MTTI is calculated by taking the sum of the time intervals between the occurrence of each security incident and its identification and dividing that sum by the total number of incidents. The formula for calculating MTTI is:

Here’s a step-by-step breakdown of the calculation:
- Record each security incident’s start time (occurrence time).
- Record the time at which each incident is identified. This is when the organization becomes aware that a security incident has occurred.
- Calculate the time interval between occurrence and identification for each incident. This is the time to identify for each incident.
- Add up all the time to identify numbers for all incidents.
- Divide the sum of time intervals by the total number of incidents. The resulting number is the average time to identify a security incident.
For example, if you have three incidents with time to identify values of 2 hours, 4 hours and 1 hour, the calculation would be:
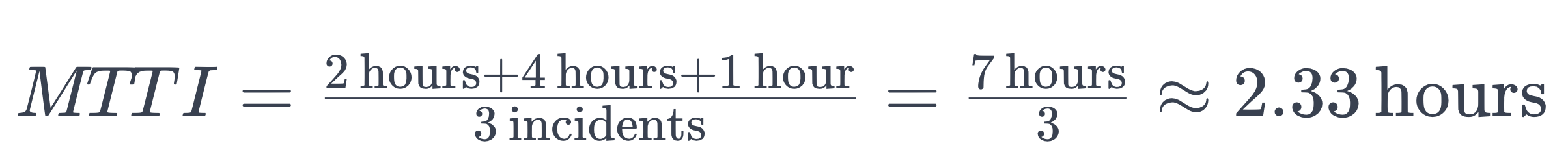
How can you reduce MTTI?
By now, it’s clear that the lower your MTTI, the better. The goal is to minimize the time it takes to identify a security incident and minimize its impact on IT systems and applications.
Here are strategies and best practices to help organizations reduce MTTI:
- Conduct incident response planning
Develop and regularly update an incident response plan with predefined processes for identifying and responding to security incidents. This ensures a structured and efficient approach when incidents occur.
Implement advanced threat detection
Utilize advanced threat detection tools and technologies, including intrusion detection systems (IDS), intrusion prevention systems (IPS) and security information and event management (SIEM) solutions. These technologies can help in quickly identifying abnormal or malicious activities. - Utilize behavioral analytics
Implement user and entity behavior analytics (UEBA) to establish a user and system behavior baseline. This can help in quickly identifying deviations that may indicate a security incident. - Automate security monitoring
Implement automation for continuous security monitoring. Automated systems can analyze large volumes of data in real time, allowing for faster detection of anomalies and potential security incidents. - Train and educate employees
Provide regular security awareness training so staff can serve as an additional defense layer, helping to identify and report security incidents quickly. - Integrate threat intelligence
Stay informed about the latest threats and tactics threat actors use by adding intelligence to security operations. This information can enhance how you identify and respond to emerging security threats. - Regularly update and patch systems
Ensure all systems and software are regularly updated with the latest security patches. Vulnerabilities in outdated software can be exploited, leading to security incidents.
Segment networks
Network segmentation isolates critical systems and sensitive data. Segmentation can help contain the impact and prevent lateral movement within the network if an incident occurs - Collaborate with threat hunting teams
Establish a threat hunting program or collaborate with threat hunting teams to actively search for signs of compromise within the network. Proactive threat hunting can uncover threats that may not be detected by automated tools alone. - Define clear incident classification criteria
Clearly define criteria for classifying incidents based on severity and impact. This helps prioritize responses and allocate resources effectively to address the most critical incidents. - Regularly test and simulate incidents
Conduct regular tabletop exercises, a security incident preparedness activity where participants handle a simulated incident scenario for hands-on training. This practice helps identify areas for improvement, ensures that response teams are well-prepared and enhances the overall effectiveness of incident response processes. - Continuous monitoring and evaluation
Continuously monitor and evaluate the performance of security operations. Regularly review incident response metrics, conduct post-incident analyses and use the insights gained to refine and improve security processes.
A practical example of immutable infrastructure and continuous deliveryWhat are the challenges when measuring MTTI?
Common challenges to measuring MTTI include:
- Different types of incidents may have varying levels of complexity, making it challenging to measure TTI across all incidents consistently. For example, advanced persistent threats (APTs) may not trigger immediate alarms. These attacks may be slow-burning and remain undetected for extended periods, making it difficult to pinpoint the exact occurrence and, consequently, the time to identify.
- Incorrect or imprecise time-stamping of events can lead to inaccurate measurements of TTI. If the logs or monitoring systems have incorrect time settings or if there are delays in recording events, the calculated TTI may not reflect the true time it took to identify an incident.
- Security systems may generate false positives or false negatives. Sorting through these false signals can complicate the measurement of TTI.
- There may be a lack of standardized criteria for defining when an incident is considered identified. Different organizations or security teams may have varying definitions, leading to inconsistent measuring.
- Limited visibility into certain parts of the network or IT infrastructure can impede the timely identification of incidents. Blind spots may delay the detection process.
- Incident identification can be influenced by human factors, such as the skill level of the security team, the availability of resources and the efficiency of communication within the organization.
- Some incidents may not be immediately reported or may be intentionally concealed. This can distort the measurement of TTI, especially if organizations rely on incident reports for their calculations.
To address these challenges, organizations should continually refine their incident detection and response processes, invest in advanced threat detection technologies and regularly review and update their metrics and methodologies for measuring time to identify.
Reducing MTTI with Sumo Logic
Sumo Logic is a cloud-based log management and log analytics platform designed to help organizations gain insights from their machine-generated data, including logs and metrics.
Customers use Sumo Logic to help reduce MTTI in the following ways:
- Real-time log analysis and alerts to investigate and perform forensics on security incidents faster.
- Advanced threat detection features that include custom alerts and correlations for faster root-cause analysis.
- UEBA for anomaly detection earlier in the attack lifecycle.
- Security Information and Event Management (SIEM) to aggregate and correlate data from various sources to provide a comprehensive view of the security landscape.
- Custom real-time dashboards and reporting to provide security teams with a single view of the threat landscape and a visual representation of key metrics and security events.
- Cloud-native architecture that scales with the organization’s needs, handling large volumes of log data efficiently.
- Continuous, automated monitoring of logs and metrics for faster detection, response and identification of security incidents.
Learn more about how Sumo Logic can help your organization reduce its MTTI.