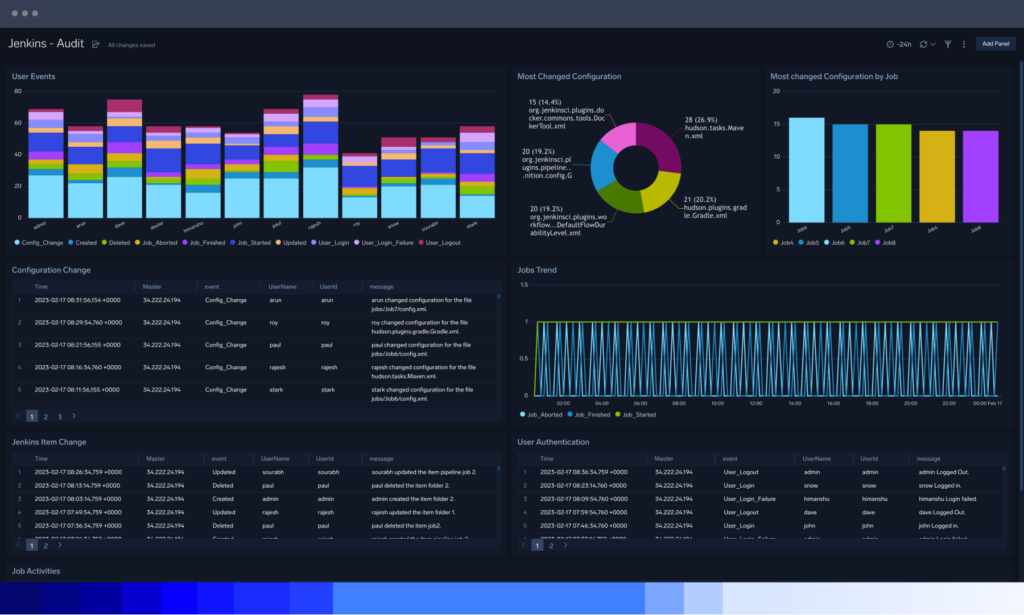
Monitor and secure your entire CI/CD lifecycle
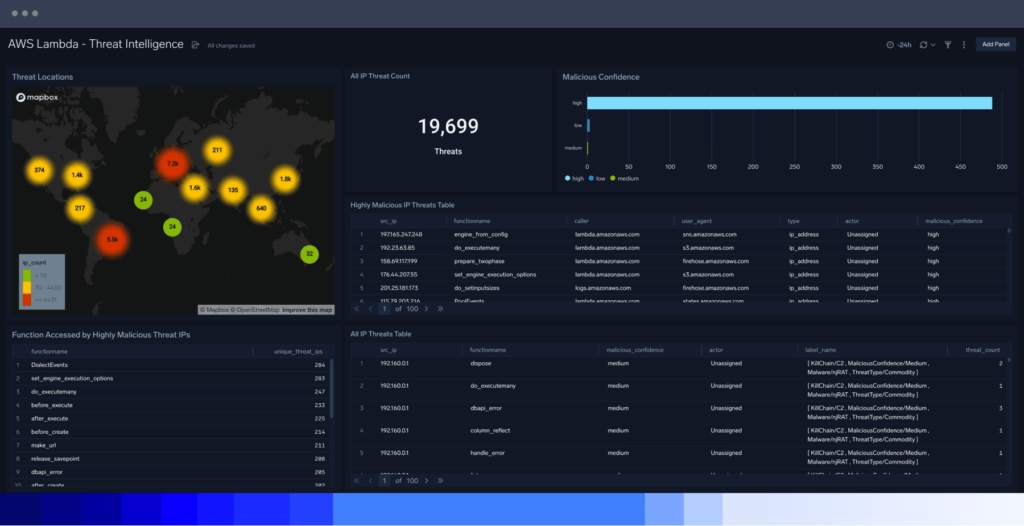
Sumo Logic centralizes event logs from all networks, infrastructure and applications to monitor, measure and examine security threats and app performance simultaneously.
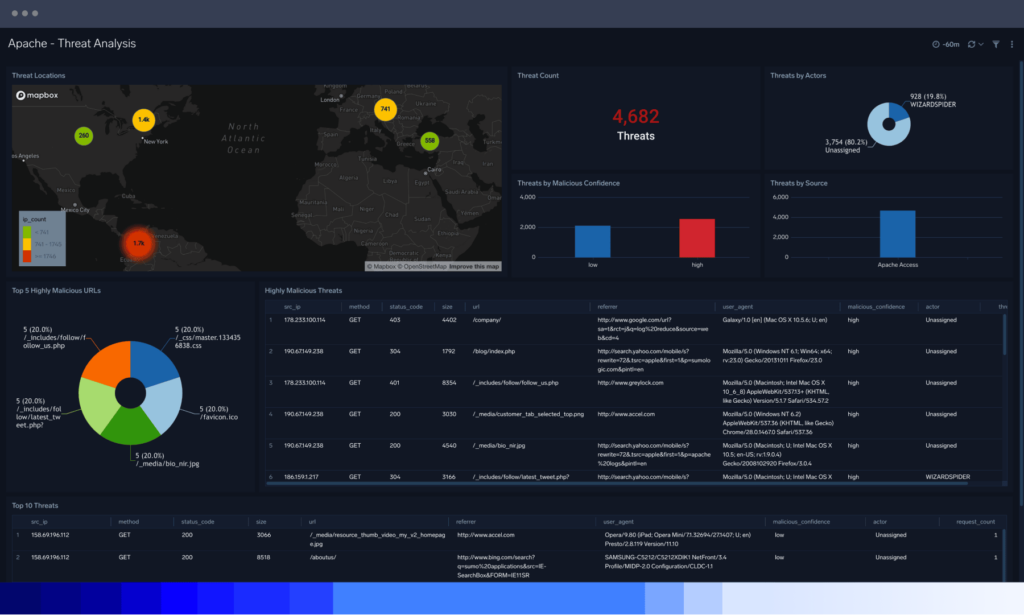
Avoid malicious app code
To protect code, teams can monitor access to code repositories and environments and enrich logs with threat intelligence to add context around usage by consolidating log data from static code.
QA test code
Ensure app reliability
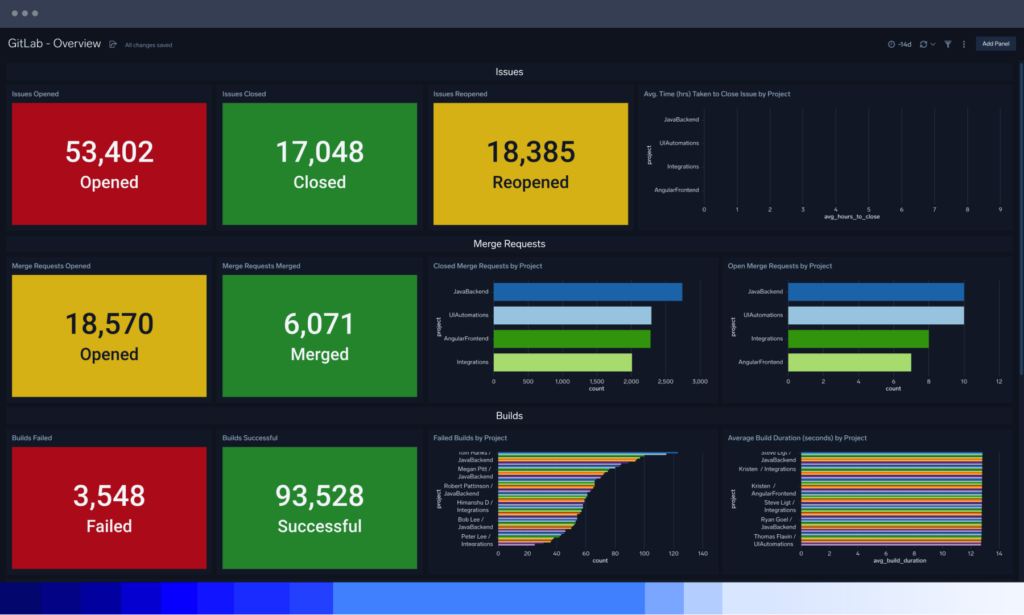
Secure CI/CD pipelines
FAQ
Still have questions?
Web application security is crucial for several reasons:
Protecting sensitive data: Applications often handle and store sensitive user information. Effective application security helps safeguard this information from unauthorized access, theft, or misuse.
Preventing unauthorized access: Applications can be a gateway for attackers to gain unauthorized access to systems or networks. This is known as a security vulnerability. By implementing robust security measures, such as application security solutions, only authorized users can access the application and its resources.
Mitigating vulnerabilities: Application security tools and practices, including secure coding techniques, regular vulnerability assessments, and penetration testing, help identify and address these vulnerabilities before they are exploited by malicious actors.
Maintaining business reputation and trust: By prioritizing application security, organizations demonstrate their commitment to protecting user data from cybersecurity breaches, fostering customer trust, and maintaining a positive brand image.
Compliance with regulations: Many industries have specific security regulations and standards that organizations must comply with. Implementing robust application security measures ensures compliance with security regulations and standards to help avoid penalties or legal liabilities.
Safeguarding against attacks: By addressing vulnerabilities and implementing security controls, organizations can minimize the risk of successful attacks and their potential impact.
Application security controls are measures or mechanisms put in place by a security engineer to protect applications from security threats and vulnerabilities. These controls aim to prevent, detect, and mitigate potential risks and ensure the confidentiality, integrity, and availability of the application and its associated data. Here are some common application security controls:
Authentication and authorization: Controls that verify the identity of users and determine their level of access to the application and its resources. This includes strong passwords, multi-factor authentication (MFA), role-based access control (RBAC), and session management.
Input validation and output encoding: Controls that validate and sanitize user input to ensure that user-supplied data is properly handled and doesn’t pose a security risk.
Secure coding practices: Controls that promote secure coding standards and guidelines during the application development process. This includes avoiding known vulnerabilities, using secure libraries and frameworks, and following secure coding practices to minimize the introduction of weaknesses.
Encryption and cryptography: Controls that protect sensitive data by encrypting it at rest and in transit. This involves using strong encryption algorithms, secure key management practices, and ensuring secure communication channels (e.g., TLS/SSL) for data transmission.
Security testing: Controls that involve conducting regular security assessments, such as vulnerability scanning, penetration testing, and code review, to identify and address application vulnerabilities. These tests help detect weaknesses and ensure that security measures are effective.
Logging and monitoring: Controls that capture and analyze application logs and events to detect and respond to security incidents. This includes monitoring unusual activities, implementing intrusion detection systems (IDS), and maintaining audit trails for accountability.
Error and exception handling: Controls that handle errors and exceptions gracefully, without exposing sensitive information. Proper error handling prevents information leakage and provides minimal feedback to attackers.
Patch management: Controls that ensure the timely application of security patches and updates for the underlying software, libraries, and dependencies. Regular patching helps address known vulnerabilities and minimize the risk of exploitation.
Secure configuration management: Controls that enforce secure configuration settings for the application, web server, database, and other components. This includes disabling unnecessary services, using secure default settings, and removing or securing default accounts.
Secure deployment and DevOps practices: Controls focusing on secure deployment processes, security integration into the software development lifecycle, and promoting a culture of security awareness among development and operations teams.
These are just a few examples of application security controls. The specific controls implemented may vary based on the application’s requirements, technology stack, and the risk profile of the organization. A comprehensive approach to application security involves a combination of these controls and others tailored to address the unique security challenges of the application.
To effectively address the numerous threats to application security, software development organizations can follow these key steps to ensure they have the necessary tools and processes in place:
Conduct a security assessment: Start by assessing the current state of application security within the organization. Perform a comprehensive security assessment to identify vulnerabilities, weaknesses, and gaps in the existing processes and tools. This assessment can include code reviews, security testing, vulnerability scanning, and penetration testing.
Define a security policy: Establish a clear and comprehensive security policy that outlines the organization’s approach to application security. The policy should define roles and responsibilities, acceptable use guidelines, incident response procedures, and the standards and best practices to be followed throughout the software development lifecycle.
Implement secure development practices: Promote secure coding practices within the development team. Train developers on secure coding guidelines, API usage, and common security vulnerabilities. Encourage code reviews and pair programming to identify and address security issues early in the development process.
Adopt security testing: Implement regular security testing as an integral part of the software development lifecycle. This can include techniques such as static code analysis, dynamic application security testing (DAST), and interactive application security testing (IAST). Use automated tools to assist with vulnerability scanning and ensure that security tests are performed regularly.
Implement secure configuration management: Ensure that applications and associated components are securely configured. Follow industry best practices and hardening guidelines for web servers, databases, operating systems, and other infrastructure components. Regularly review and update configurations as required.
Establish incident response procedures: Develop a robust incident response plan to handle security incidents effectively. Define roles and responsibilities, establish communication channels, and train the relevant personnel on incident response procedures. Conduct periodic drills and tabletop exercises to test the incident response capability.
Provide ongoing training and awareness: Security is a shared responsibility. Provide continuous security training and awareness programs for all personnel involved in the software development process. This includes developers, testers, project managers, and system administrators. Keep the team informed about emerging security threats, best practices, and updates.
Engage in secure third-party management: Evaluate the security posture of third-party vendors and partners that contribute to the software development process. Establish contract security requirements, conduct due diligence, and periodically assess their security practices to ensure they align with your organization’s standards.
Stay updated with security knowledge: Monitor security news, publications, and community resources to stay informed about the latest security threats and best practices. Engage with security communities, participate in conferences, and encourage knowledge sharing among team members. This helps ensure that the organization stays updated with evolving security challenges.
Perform regular audits and reviews: Conduct periodic security audits and reviews to assess the effectiveness of the implemented security measures. This includes reviewing security logs, access controls, and system configurations. Engage external security experts for independent assessments to gain additional insights and recommendations.
By following these steps, software development organizations can establish a strong foundation for addressing application security threats. It is an ongoing effort that requires a proactive and vigilant approach to ensure that tools, processes, and practices are continuously adapted to evolving security risks.