Providing Robust Security and Monitoring for Forensics Purposes
Detecting Kubernetes Abuse and Misuse of Non-compliant Activity
Automatic and proactive audit analysis, for detecting security-related issues on Kubernetes clusters with full exposure of users and suspicious activities.
Enhanced Visibility and Observability into Kubernetes Audit Logs
Providing deep visibility and real-time insights with the ability to focus on pre-customized rules, using advanced visualizations, rather than sifting through raw logs.
Investigation Dashboard for Runtime Protection
Get a summary of detected anomalies alongside important access, usage, and performance of Kubernetes cluster trends and statistics for investigation and auditing.
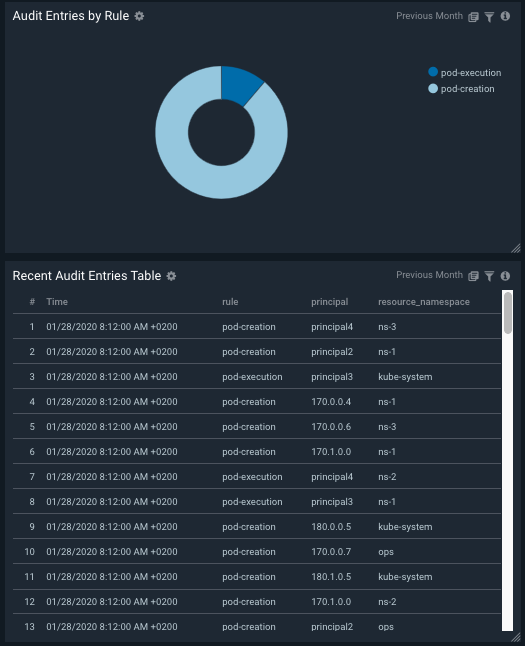
Audit Entries
Closely monitor and track all security-related audit entries, documenting relevant activities by users or service components, filtering events indicating policies violation
Anomalies and Incidents
Get a high-level view of tracked anomalies and incidents over time, proactively identifying non-compliant behavior with the ability to configure a set of rules representing the organization’s policies
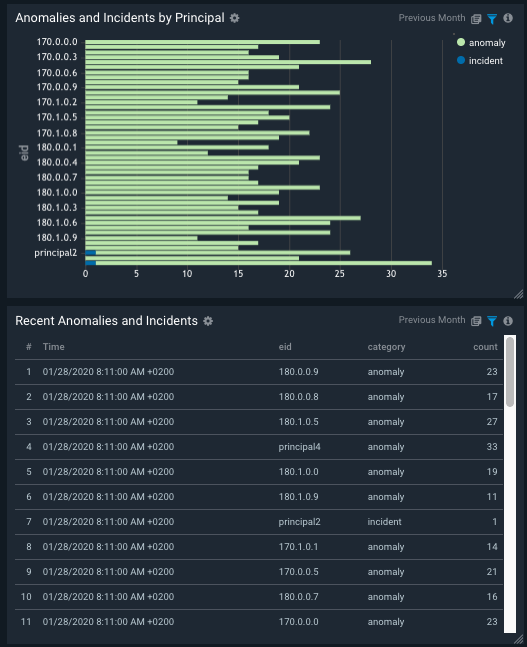
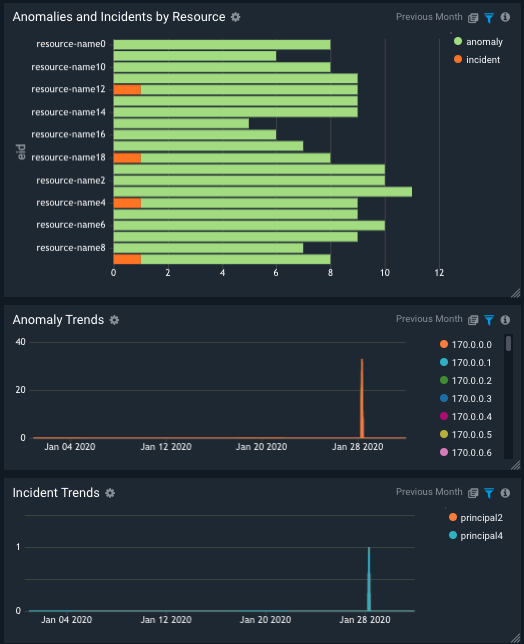
Identify Root Cause
Investigate specific operational and security issues, trace back to responsible parties, troubleshoot and identify root cause with ease


