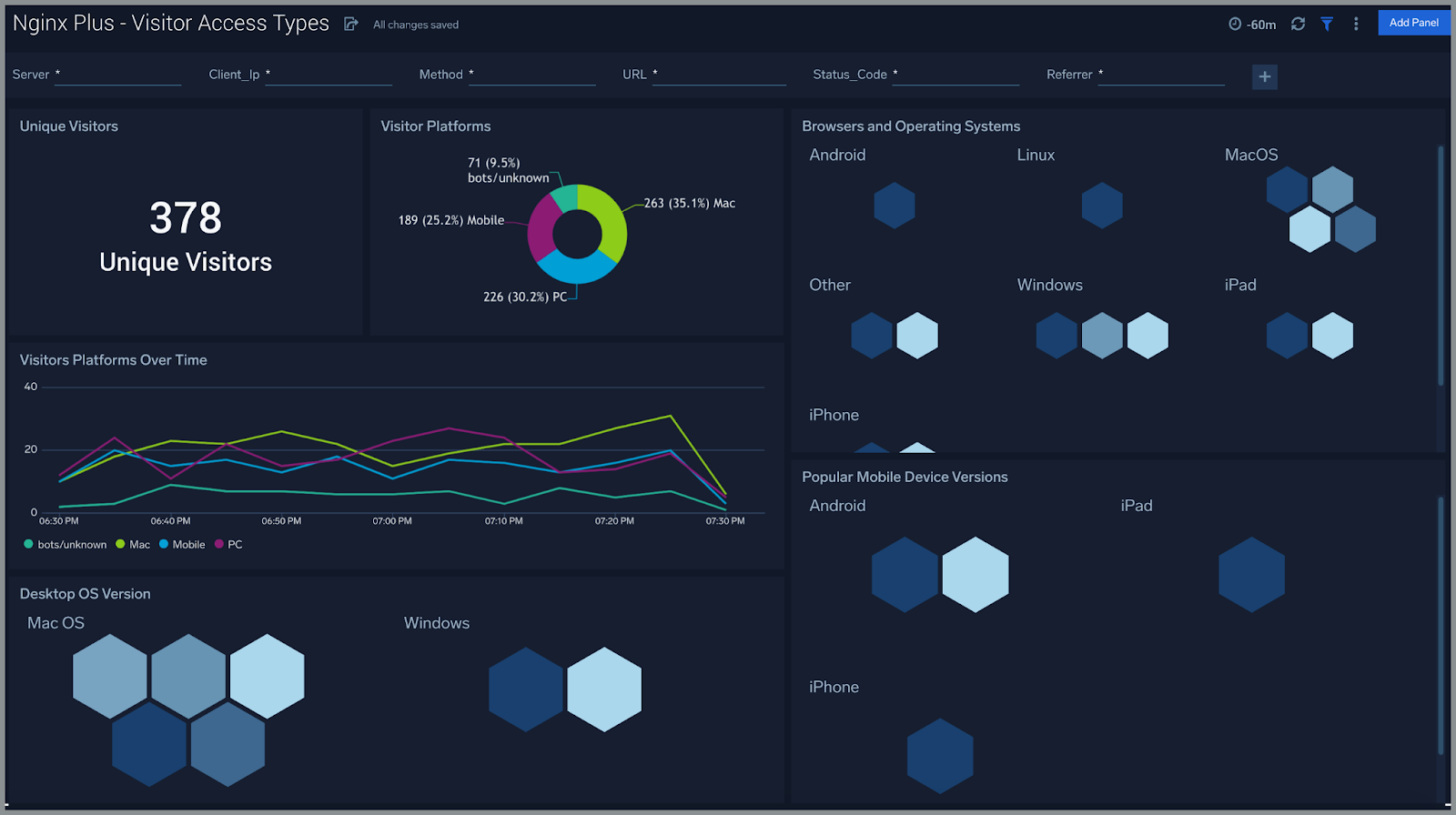
CLOUD SIEM AUTOMATION
Transform complexity into insights
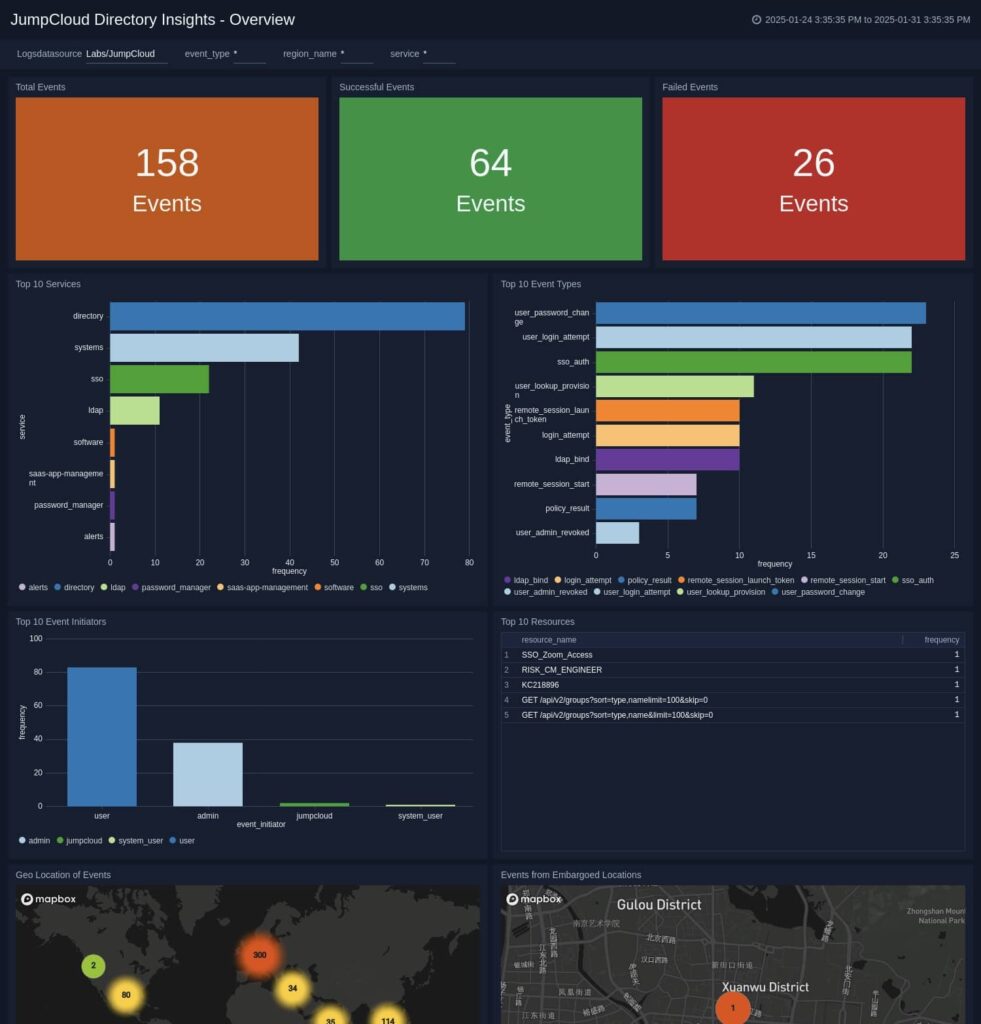
Cloud SIEM
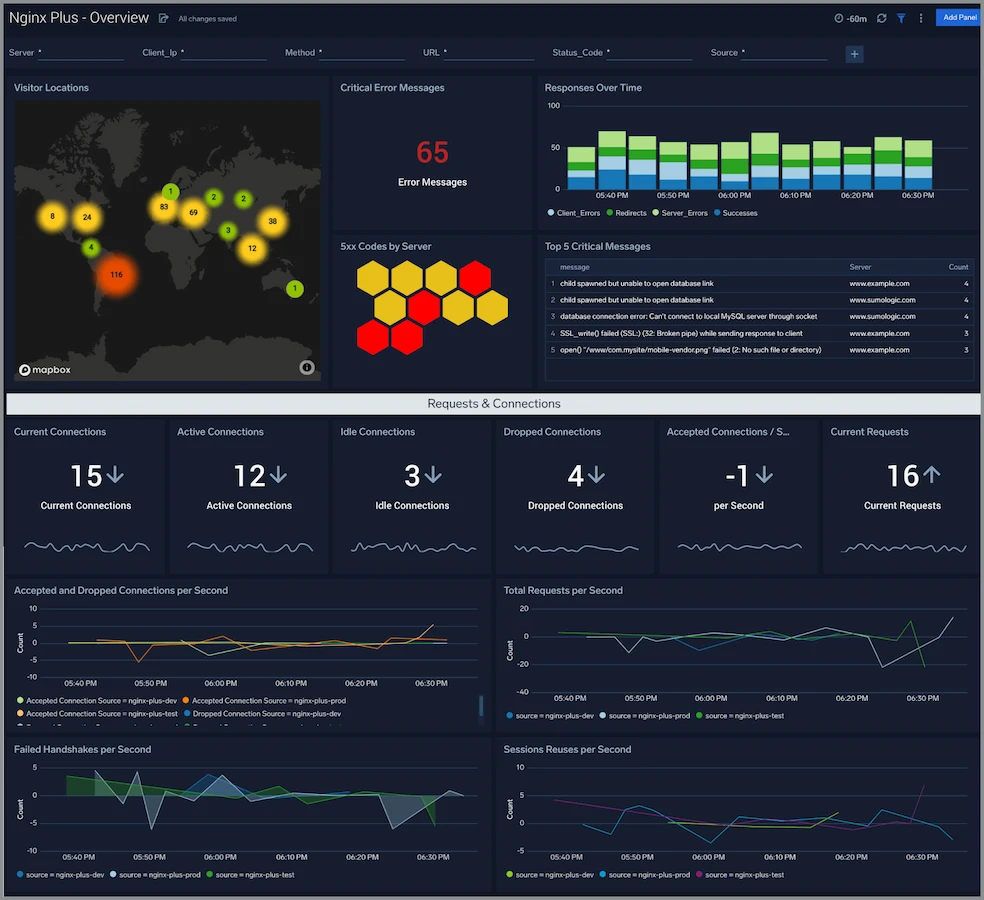
Speed up incident investigations by automatically triaging alerts and correlating threats through log analytics.
Logs for Security
Reduce the noise
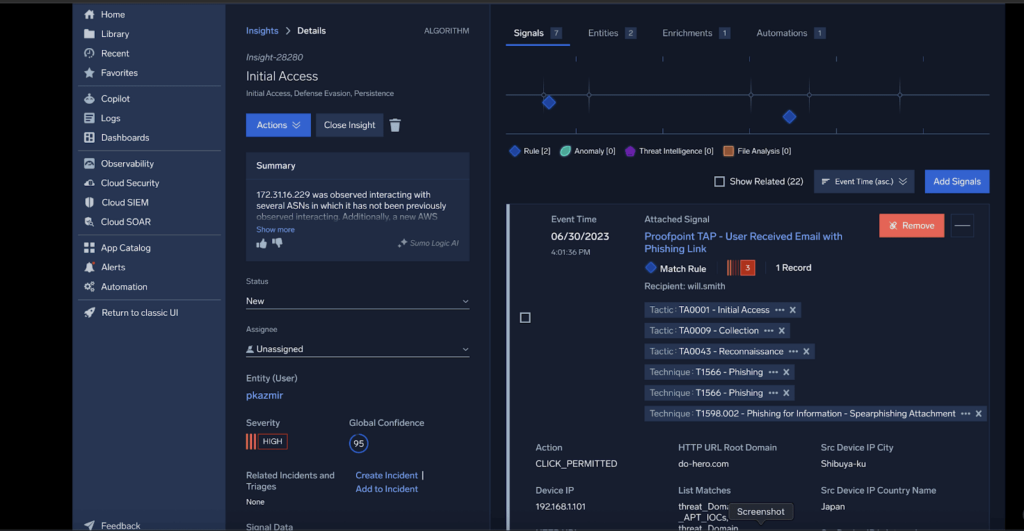
AI-powered Copilot
Signals and Insights
450+
Powerful
Integrations
Secure
by design
Additional resources

Splunk vs. Sumo Logic
Splunk’s siloed approach to log analytics and SIEM increases deployment cost and complexity. With Sumo Logic, you’ll eliminate bursting fees and scale seamlessly.

Datadog vs. Sumo Logic
Datadog can’t handle unstructured data. See why Sumo Logic’s unified approach across logs and a cloud-native SIEM set it apart.

2025 Security operations insights
Three-quarters of security leaders need something new in SIEM. Why are they rethinking their approach, and what are they looking for? Read our original research report to explore the current and future state of SIEM.

Why Mambu migrated to Sumo Logic
In this talk, Mambu shares how partnering with Sumo Logic helped them achieve better visibility, compliance, and security.
FAQ
Still have questions?
SIEM software combines the capabilities of security information management (SIM) and security event management (SEM) tools.
SIM technology collects information from a log consisting of various data types. In contrast, SEM looks more closely at specific types of events.
Together, you can collect, monitor and analyze security-related data from automatically generated computer logs while centralizing computer log data from multiple sources. This comprehensive security solution enables a formalized incident response process.
Typical functions of a SIEM software tool include:
- Collecting, analyzing and presenting security-related data
- Real-time analysis of security alerts
- Logging security data and generating reports
- Identity and access management
- Log auditing and review
- Incident response and security operations
SIEM delivers superior incident response and enterprise security outcomes through several key capabilities, including:
Data collection – SIEM tools aggregate event and system logs and security data from various sources and applications in one place.
Correlation – SIEM tools use various correlation techniques to link bits of data with common attributes and help turn that data into actionable information for SecOps teams.
Alerting – SIEM tools can be configured to automatically alert SecOps or IT teams when predefined signals or patterns are detected that might indicate a security event.
Data retention – SIEM tools are designed to store large volumes of log data, ensuring that security teams can correlate data over time and enabling forensic investigations into threats or cyber-attacks that may have initially gone undetected.
Parsing, log normalization and categorization – SIEM tools make it easier for organizations to parse through logs that might have been created weeks or even months ago. Parsing, log normalization and categorization are additional features of SIEM tools that make logs more searchable and help to enable forensic analysis, even with millions of log entries to sift through.
Popular SIEM use cases include:
Compliance – Streamline the compliance process to meet data security and privacy compliance regulations. For example, to comply with the PCI DSS, data security standards for merchants that collect credit card information from their customers, SIEM monitors network access and transaction logs within the database to verify that there has been no unauthorized access to customer data.
Incident response – Increase the efficiency and timeliness of incident response activities. When a breach is detected, SecOps teams can use SIEM software to quickly identify how the attack breached enterprise security systems and what hosts or applications were affected by the breach. SIEM tools can even respond to these attacks through automated mechanisms.
Vulnerability management – Proactively test your network and IT infrastructure to detect and address possible entry points for cyber attacks. SIEM software tools are an important data source for discovering new vulnerabilities, along with network vulnerability testing, staff reports and vendor announcements.
Threat intelligence – Collaborate closely to reduce your vulnerability to advanced persistent threats (APTs) and zero-day threats. SIEM software tools provide a framework for collecting and analyzing log data that is generated within your application stack. With UEBA, you can proactively discover insider threats.
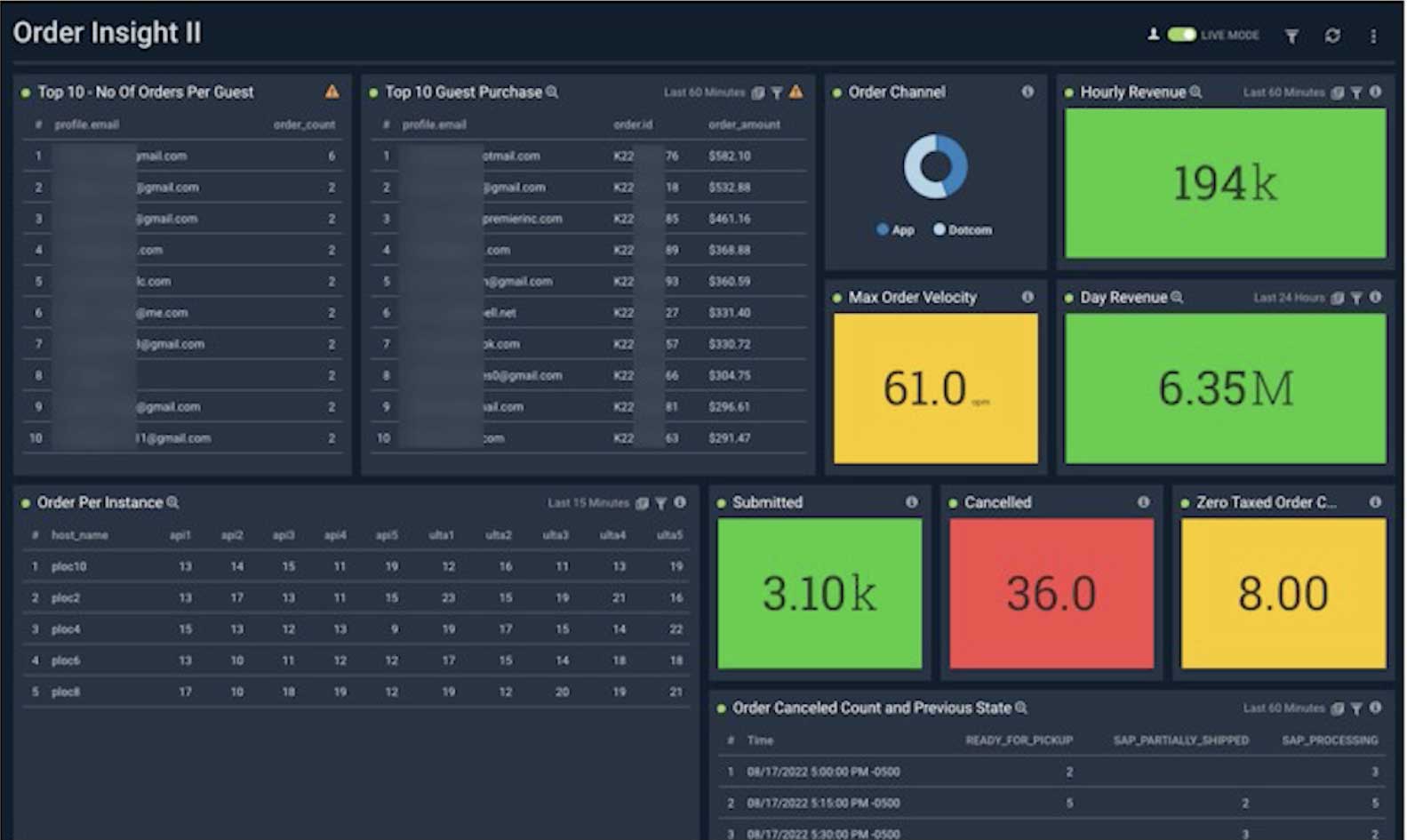
Sumo Logic Cloud SIEM is part of the Sumo Logic security platform, a cloud-native multi-use solution powered by logs. In addition to Cloud SIEM, Sumo Logic’s robust log analytics platform supports Infrastructure Monitoring, Application Observability and Logs for Security for monitoring, troubleshooting and securing your apps.
Customers choose Sumo Logic SIEM for these differentiated features:
One integrated log analytics platform – a single integrated solution for developers, security, operations and LOB teams.
Cloud-native, distributed architecture – scalable, multi-tenant platform powered by logs that never drop your data.
Tiered analytics and credit licensing – enjoy flexible subscriptions that scale as your data grows faster than your budget.
Machine learning and advanced analytics – identify, investigate and resolve issues faster with machine learning.
Out-of-the-box audit and compliance – you can easily demonstrate compliance with the broadest certifications and attestations.
Secure by design – We invest millions each year on certifications, attestations, pen testing, code review and paid bug bounty programs.