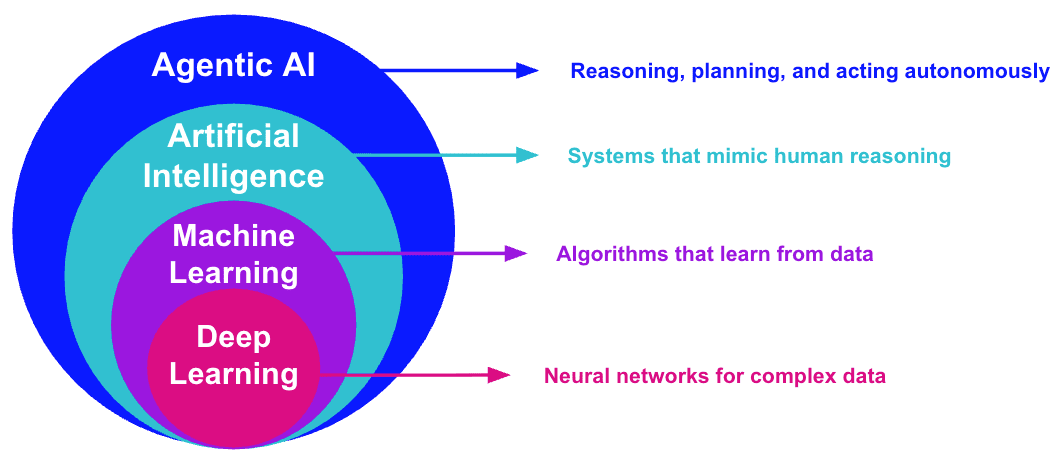
Artificial intelligence (AI), machine intelligence, machine learning, and deep learning are often used interchangeably, but each represents a stage in the evolution of computational intelligence. AI is the broadest concept, describing machines that can perform tasks associated with human reasoning. Machine learning (ML) lives under that umbrella, enabling systems to improve from data rather than explicit programming. Within ML, deep learning applies layered neural networks to vast datasets, powering advances like image recognition and self-driving cars.
In log analytics, these foundational technologies have traditionally been used to detect anomalies, surface patterns, and automate repetitive work. But the industry is moving toward agentic AI — systems that not only learn from data but also reason, plan, and act on behalf of human teams. Where deep learning automated feature extraction, agentic AI introduces autonomy and collaboration. It does not just find signals in noise, it interprets those signals in context and recommends, or even initiates, the next step.
From AIOps to agentic operations
For years, AIOps applied AI to IT operations, using algorithms to spot anomalies, predict failures, and optimize resources. This was a leap forward, but the responsibility for interpreting and acting on insights remained squarely with humans. Tools like Mobot with Query agent made progress by enabling natural language queries over machine data, making it easier to ask questions and uncover root causes.
Sumo Logic’s Dojo AI pushes this further by embedding reasoning into the loop. Instead of merely responding to prompts or producing visualizations, now agents can generate hypotheses, plan investigations, and propose actions. For security and reliability teams, this represents a shift from “assistive automation” to collaborative agents that work alongside analysts and engineers.
Sumo Logic’s first two agents illustrate this shift. The Summary Agent applies machine learning to condense the complexity of SIEM Insights into actionable storylines, turning a stream of fragmented alerts into a coherent incident narrative. The Query Agent allows analysts and engineers to describe investigative intent in natural language, automatically producing the complex query syntax required to search across endless troves of log data. Together, these agents show how AIOps evolves into agentic operations: less time wrestling with data, more time validating and executing decisions.
Machine intelligence for log analytics
Traditionally, machine intelligence in log analytics focused on drawing insights from access, usage, and performance data. Security teams used it to identify anomalies and trigger alerts, while infrastructure teams used it to understand system load and performance. These applications remain valuable, but in an agentic context, they are stepping stones toward systems that can not only detect but also explain and act.
For example, instead of simply flagging unusual login attempts, an agentic system can summarize the sequence of events into a clear narrative… where the access came from, why it is suspicious, what risk it poses, and then recommend an appropriate response. Similarly, when performance degrades, the system can propose hypotheses for root cause and generate the exact queries needed to validate them. In this way, Summary Agents and Query Agents become extensions of SOC analysts and SREs, helping them move from vast telemetry to resolution more quickly.
Why is machine data important?
The ability to harness machine data for intelligence and speed is no longer optional. Historically, teams relied on data to answer questions like: How are our systems performing? Are there bottlenecks? Who is accessing them? Are there anomalies? But these questions placed the burden of interpretation entirely on humans.
With agentic AI, machine data becomes the substrate for autonomous reasoning. A SOC analyst no longer has to manually correlate dozens of alerts or independently correlate threat intelligence; the Summary Agent presents a consolidated narrative of what’s happening. An SRE no longer has to construct intricate queries under pressure; the Query Agent does it on their behalf. Machine data remains vital, but its value is amplified when paired with agents that can transform raw signals into actionable context.
What is machine learning in a big data context?
Machine learning was once the ceiling of automation for log analytics: algorithms that could parse large volumes of unstructured data, surface patterns, and detect anomalies. It was a powerful enabler, especially in environments with overwhelming data streams.
In the agentic era, machine learning is a component of something larger. It powers the detection and summarization capabilities of agents but is embedded in workflows that extend beyond classification or anomaly detection. The Summary Agent uses ML to condense hundreds of alerts into a single, meaningful storyline. The Query Agent uses ML-based language understanding to map human intent to query syntax. In both cases, the technology goes beyond analytics, it collaborates with practitioners, bridging the gap between insight and action.
Practical uses of log analytics and agentic AI
Within a single organization, different teams will continue to rely on machine data, but their relationship to that data is being transformed.
For SOC analysts, agentic systems distill security signals into narratives that can be investigated immediately. Instead of drowning in false positives, they spend time assessing risk and executing response. For SREs, agentic systems simplify the debugging of distributed applications by generating queries that cut through the complexity of massive log sets. Both groups benefit from reduced cognitive load, accelerated investigations, and greater confidence in decision-making.
Mobot, now a part of Dojo AI and infused with agentic behaviors, exemplifies this shift. It no longer simply enables natural language queries; it actively assists in the investigation process, generating queries, correlating findings, and summarizing results. In practice, this means fewer bottlenecks, faster resolution, and greater operational resilience.
Challenges with agentic log analytics
The promise of agentic AI is matched by new challenges. Machine data continues to grow at exponential scale, and agents must be designed to operate across structured, unstructured, and semi-structured inputs. More importantly, autonomy introduces questions of trust and governance.
SOC analysts and SREs cannot delegate critical decisions to black-box systems. Transparency is essential and agents must be able to explain how conclusions were reached and why particular actions are recommended. Guardrails such as role-based access controls (RBAC) ensure that agents only act within defined boundaries, while human-in-the-loop controls keep accountability where it belongs. In regulated industries, compliance remains paramount; agentic systems must handle sensitive data responsibly, obfuscating or anonymizing where necessary.
By addressing these challenges head-on, organizations can embrace agentic AI while maintaining control, compliance, and confidence.
The future of agentic intelligence: predictive and generative
Generative AI brought the ability to create new insights, forecasts, and simulations. Predictive analytics extended this, helping teams anticipate system demands and emerging threats. The next step is agentic AI, where those forecasts are not left as static insights but are transformed into contextual plans and, where appropriate, into actions.
In security, this means agents that can not only detect a zero-day exploit but simulate the likely attack paths, prioritize the most urgent exposures, and recommend tailored defenses. For reliability engineering, it means anticipating a capacity shortfall and generating validated remediation strategies before customers ever feel an impact. These are no longer speculative use cases, they represent the trajectory already unfolding.
Agentic systems such as Sumo’s Summary and Query agents illustrate how investigations are changing: compressing fragmented alerts into coherent stories and turning natural language into precise, executable queries. The result is faster threat triage for SOC analysts, streamlined root-cause analysis for SREs, and a shift from reactive response toward proactive resilience.
The convergence of predictive analytics, generative AI, and agentic autonomy marks a turning point in modern operations. Instead of drowning in noise or waiting for the next alert storm, teams will work alongside intelligent agents that reason, recommend, and act within well-defined guardrails. For security and reliability teams alike, this signals a future where human expertise is amplified, sharpened by AI that doesn’t just observe, but collaborates.