Get end-to-end visibility for your cloud native workloads with Aqua and Sumo Logic
Image Security in Your CI/CD Pipeline
Monitor the security posture of the images in your CI/CD pipeline to identify and quickly remediate known vulnerabilities, malware and embedded sensitive data found in your workloads.
Host Security and Compliance
Monitor the compliance posture of each of your cloud native hosts based on CIS benchmarks for Kubernetes, Docker and Linux, as well as your own customized compliance policies.
Security in Your Runtime Environment
Monitor unauthorized and suspicious activity in your production workloads, identifying anomalous executables like privilege escalations, unregistered or non-compliant images being pushed into production, or unauthorized network activity.
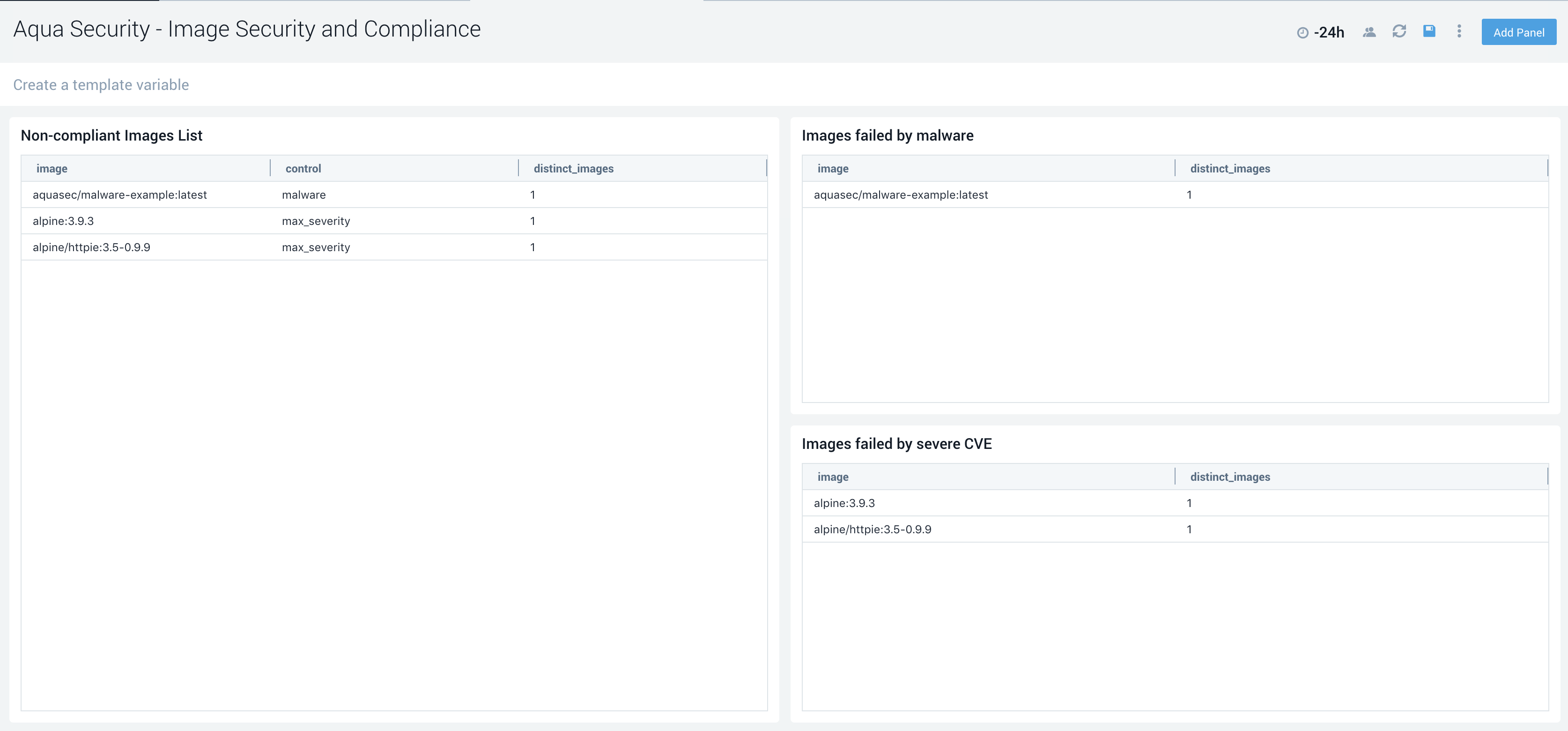
Image Security
Identify and monitor images in your CI pipeline that have failed your image assurance policies due to malware, exposed sensitive data or high-risk vulnerabilities. Aqua plugs into your preferred CI/CD pipeline to continuously scan your images for known vulnerabilities, malware and poor configurations, allowing you to fail fast and fix issues early when building your applications.
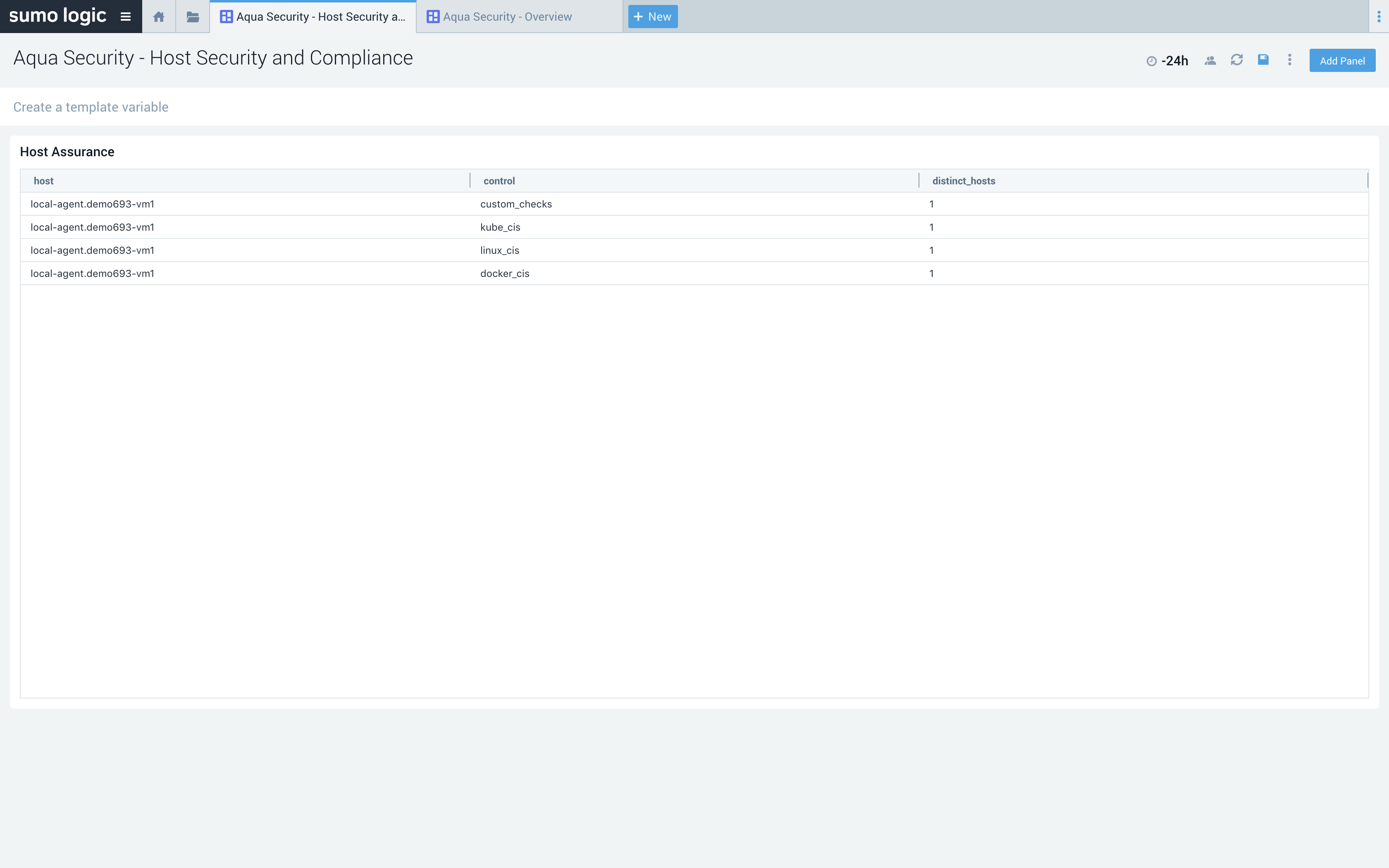
Host Security and Compliance
Identify and monitor the compliance posture of your cloud hosts, using Aqua to ensure that they meet CIS standards for Kubernetes, Docker and Linux.
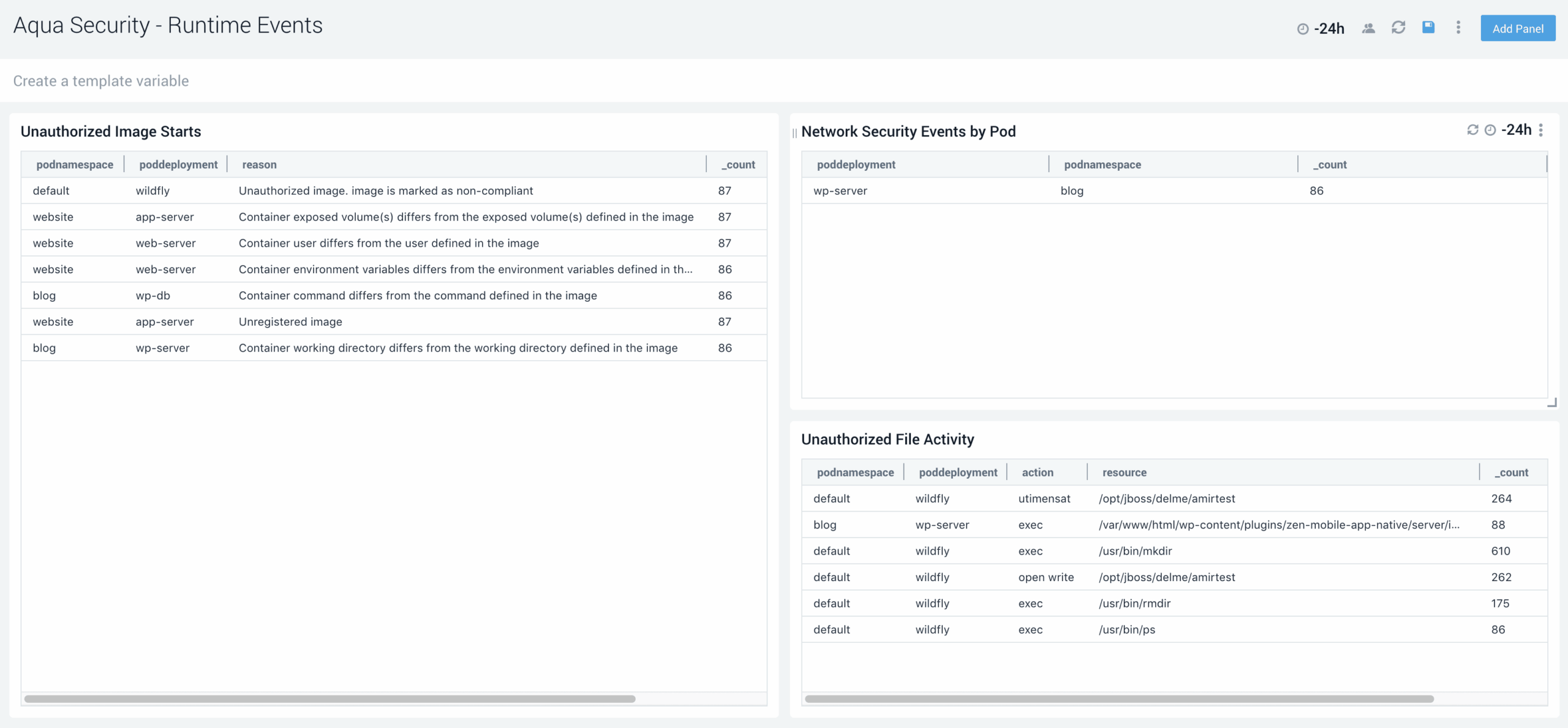
Runtime Security
Identify and monitor unauthorized or suspicious runtime behavior in your cloud native workloads. Aqua will detect and block any high-risk or unregistered images being pushed into runtime, and will block anomalous executables and files as well as suspicious network activity in production.

