Identify and remediate vulnerabilities, misconfigurations, compliance violations, and runtime threats
Secure your environment against vulnerabilities
Protect your cloud-native systems from vulnerabilities across images, containers, Kubernetes, and your running deployments
Detect and prevent accidental exposures from misconfiguration
Identify misconfigurations across images, containers, clusters, Kubernetes, and network policies, preventing the accidental exposures that put your systems at risk
Identify and respond to runtime threats
Combine rules, whitelists, baselines, and behavioral modeling to identify and remediate runtime threats in your container environments
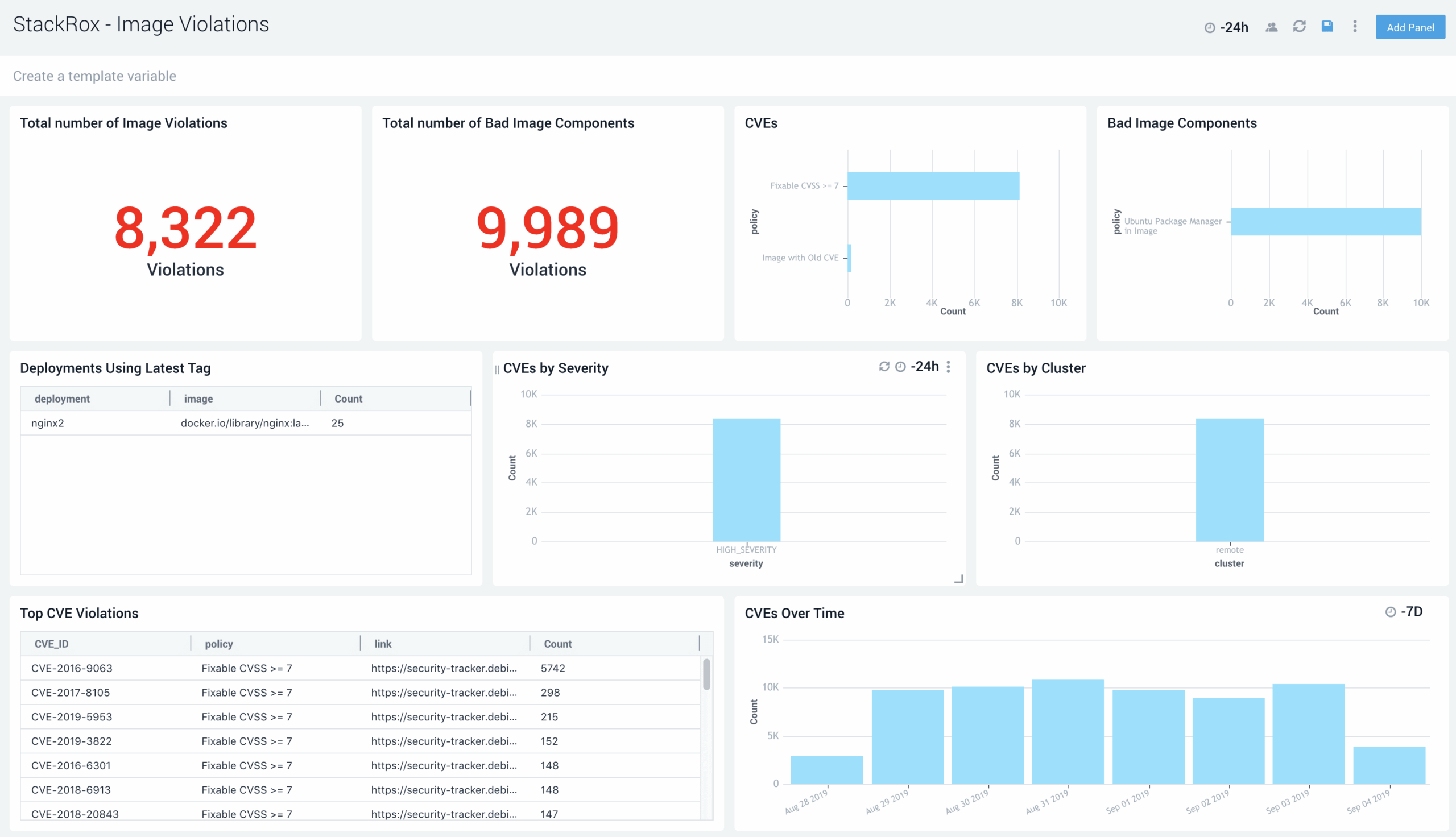
Comprehensive Vulnerability Management
Ensure your container and Kubernetes environments are free from vulnerabilities from the moment images are built until they’re running by identifying vulnerabilities across images, running deployments, and clusters. Understand your risk profile by gaining visibility into the severity of vulnerabilities impacting your environment so you can prioritize remediation efforts in higher risk areas.
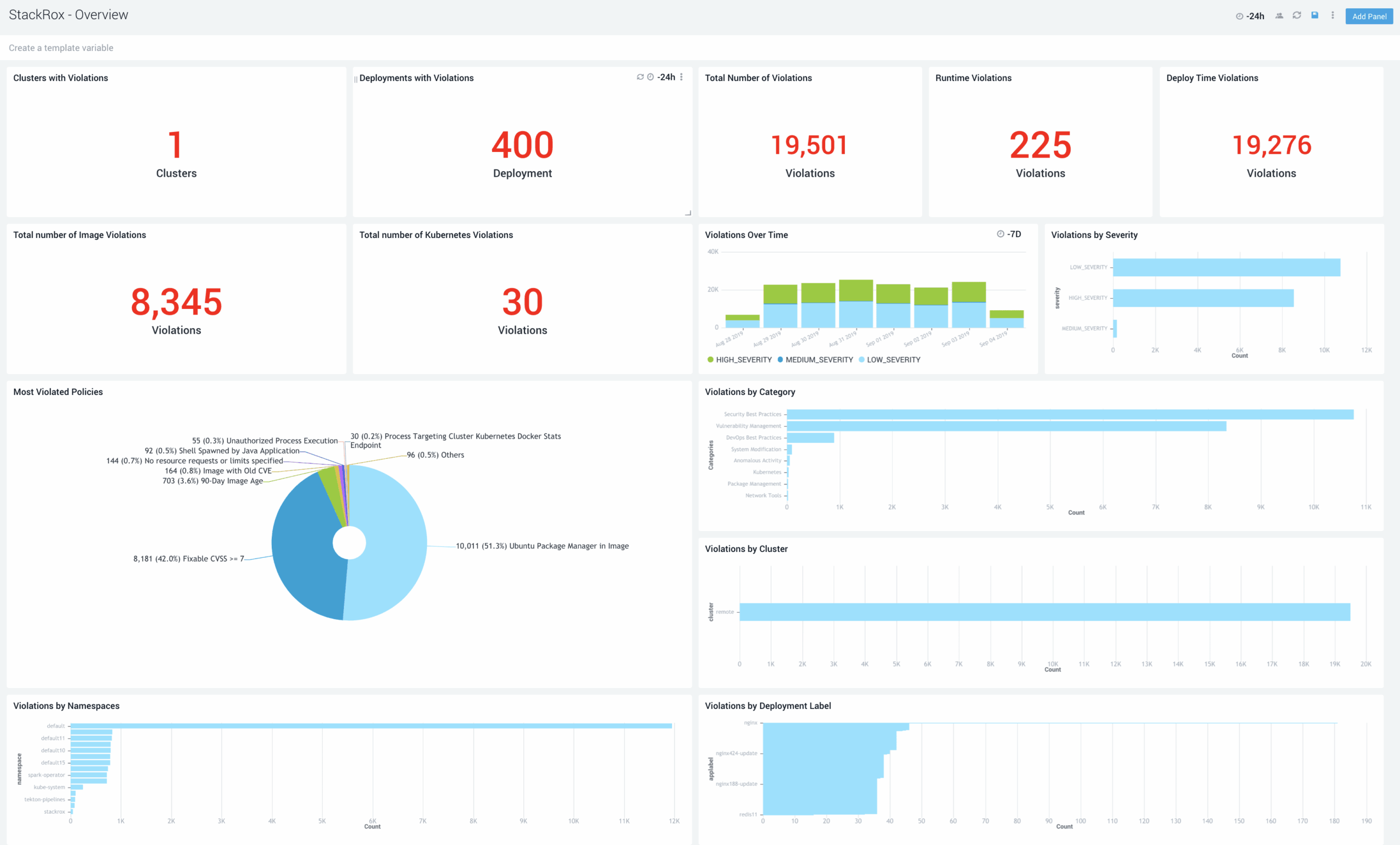
Automated Configuration Management
Operationalize Kubernetes security by automating configuration management so that your security scales as your environment scales. Get an at-a-glance dashboard view of Kubernetes configuration violations across your deployments and namespaces and understand vour true security risk through insights into the severity of the violations.
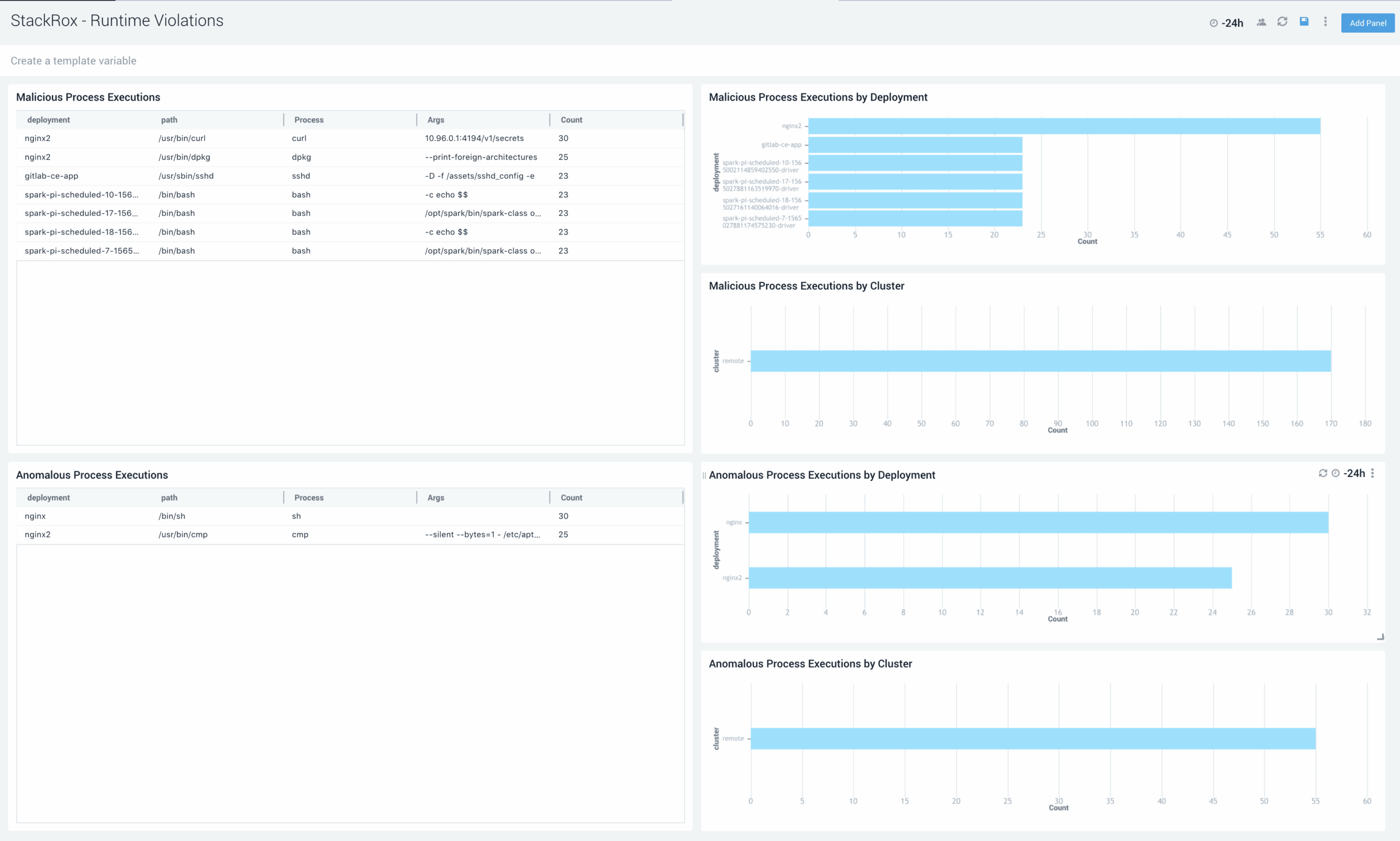
Runtime Threat Detection
Monitor process execution, network connections and flows, privilege escalation, and files launched to identify threats in real-time. Use the runtime violations dashboard to pinpoint which deployments and clusters are executing a malicious or anomalous process to accelerate forensic investigation and response.