When it comes to cybersecurity, businesses have never faced as many challenges as they do today. Each year sets new records for the scope and frequency of cyberattacks.
Security information and event management, or SIEM, solutions help organizations stay ahead of the never-ending stream of security risks and vulnerabilities the typical business faces. By providing a centralized platform that businesses can use to collect, normalize and analyze data that could reveal security risks, SIEM pre-empts threats through early detection and post-mortem security policy management. Querying security information allows SIEM owners to know and measure the effectiveness of their posture management and security controls.
The never-ending stream of security risks and vulnerabilities requires interpreting data from various IT resources (IT, IoT, physical, app, etc.), then detecting and responding to threats in real-time. New threats, like software supply chain attacks, are constantly arising. And the scale and complexity of the systems that businesses have to defend are steadily growing as more and more workloads move to distributed, microservices-based architectures.
Faced with these challenges, organizations need an efficient and comprehensive means of collecting, normalizing, analyzing and reacting to information about cyber threats.

This guide breaks down how SIEMs work, why they’re critical to modern businesses and how they relate to other types of cybersecurity platforms, such as security orchestration, automation and response (SOAR) tools. It also offers guidance on how best to choose and configure a SIEM solution to maximize efficiency and collaboration while minimizing risk.
What is SIEM?
Security information and event management is a type of cybersecurity platform that allows businesses to collect, normalize and analyze security event data from multiple sources.
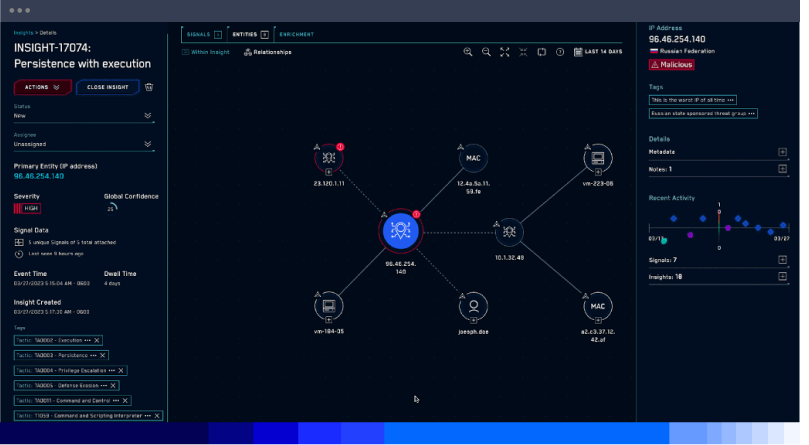
The core features of a SIEM system include:
- Centralized collection, analysis, aggregation and presentation of security-related data
- Log management, auditing and review
- Event correlation
- Case management with real-time creation of security alerts
- Threat detection
- Insider threat and anomaly detection
- Generation of compliance reports (PCI DSS, HIPAA, and more)
SIEM feature sets may extend further than these essential features. For example, modern SIEM technology often provides functionality to help teams coordinate the incident response process, not just detect threats. It may also include user and entity behavior analytics (UEBA) and integrate with third-party threat intelligence databases, allowing teams to contextualize threats detected by a SIEM tool and determine how much risk each poses.
Legacy vs. modern tools
SIEM is not new technology. Its origin dates back to the nineties, and so much has changed since that decade. At the time, probably no one could anticipate the enormous expansion of threat vectors we’ve experienced recently. Today, the consensus is that standard or traditional SIEMs are anachronistic, hence the title legacy SIEMs.
The main drawbacks of legacy SIEMs are that they:
- Are complex to deploy — they are often deployed on-premises vs. cloud-native — making them hard to scale and difficult to maintain
- Have limited ingestion capabilities, complex architecture, and are difficult to integrate with third-party tools (require in-house development)
- Suffer from weak and inflexible data correlation, performance issues, and management disruptions
- Require plenty of effort and expertise for analysts to do their job
All this can result in alert fatigue, missed threats — especially insider threats — and ineffective threat investigation.
In contrast, next-generation or modern SIEM solutions:
- Are simple, relatively easy-to-use, scalable and flexible
- Include real-time or near real-time investigation capabilities
- Work in any different environment: on-premises, cloud, multi-cloud, or hybrid
- Incorporate automated threat intelligence, data enrichment, threat detection, incident prioritization and possibly response capabilities
- Encompass ability to track user behaviors and activities
- Ingest various data — such as log, network, and cloud — from virtually any source and appliance, meaning they are data source-agnostic and vendor-agnostic
- Offer integration possibilities over and above a stack of out-of-the-box connectors
- Provide the possibility to create custom rules on top of the built-in correlation rules
- Enable basic automated incident response
Unlike legacy, modern SIEMs typically implement machine learning and big data analytics models, which results in highly adaptive behavior. Their machine learning (ML) engines continuously learn from massive volumes of data, helping security teams respond to previously unseen threat scenarios.
These advances enable you to reduce tons of data to a few meaningful insights, relieving the workload of already overstretched security analysts.
Why do enterprises need a SIEM?
The term “SIEM” was coined in 2005 by Gartner analysts. However, it remains as relevant today as it was two decades ago because the problems that SIEM software was designed to solve have not disappeared. On the contrary, they have grown more pronounced as the scope and complexity of cyber risks have steadily increased.
The main reason why organizations need a SIEM is that detecting threats requires the analysis of many sets of data, and a SIEM is the only means of performing that analysis in an efficient, centralized way. Without it, cybersecurity and IT teams would have to parse individual log files and event streams manually, looking for anomalies or patterns that could signal security issues.
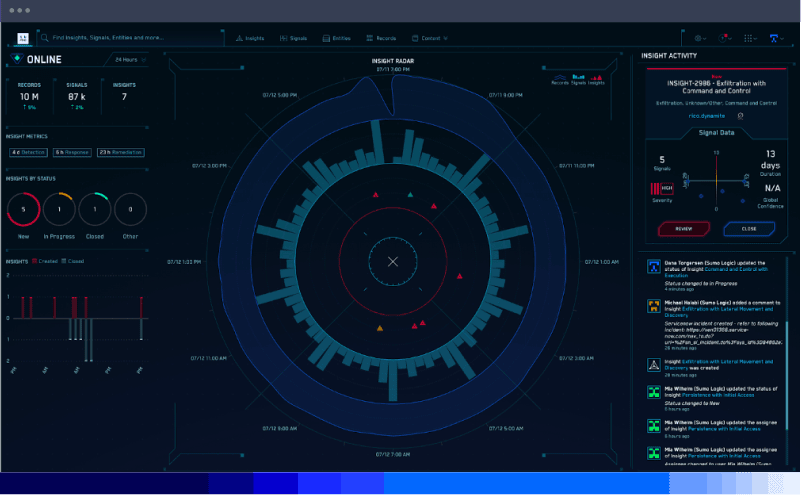
Not only would that security operation be time-consuming and tedious, but it would also make it difficult for teams to correlate multiple data sources to gain maximum context about potential risks.
For example, if engineers look just at an application event log, it would be hard to determine whether a sudden spike in requests to the application could be a sign of a DDoS attack, or if it resulted from a natural uptick in traffic. But if they could correlate the application log with network logs showing where the traffic originated, it would be easier to determine whether the requests came from legitimate endpoints or were associated with a botnet.
With a SIEM, then, organizations can detect and react to security threats more quickly and more accurately – a critical advantage in a world where cyber threats are ubiquitous. It may take only minutes for attackers to begin exfiltrating data or disrupting critical services once they’ve breached a business’s cyber defenses.
Other SIEM benefits
Beyond the core advantage of being able to detect and react to threats quickly, SIEMs deliver additional benefits, including:
- Centralized management of security-related data.
- Easy sharing of security data with multiple stakeholders, such as security teams, developers and IT engineers.
- The ability to track security events and risks over time to identify relevant trends.
- Efficient management of security alerts to minimize false positives and prevent alert fatigue (which 88 percent of security professionals identify as a challenge).
- The ability to automate complex security processes so that businesses can do more with limited cybersecurity teams – an important advantage given the difficulty of hiring skilled security professionals amid the ongoing cybersecurity “brain drain.”
Thus, in addition to enhancing cybersecurity operations, SIEMs help businesses to maximize collaboration and make the most efficient use of resources when managing security challenges.
SIEM vs. SOAR and other security tools
Although a SIEM typically serves as the foundational hub for managing cybersecurity data and threats, it’s usually not the only cybersecurity tool that enterprises rely upon.
SIEMs don’t address challenges like detecting vulnerabilities within software source code or finding risky container images. Teams need different, specific tools (namely, source composition analysis and container image scanners). Nor do SIEMs audit the configurations of software environments to detect risks like insecure identity and access management (IAM) settings for cloud resources. There again, different categories of tools, like cloud security posture management solutions, are necessary.
However, by collecting and analyzing the data produced by various other security tools, SIEMs provide a centralized, unified source of visibility into security threats and risks. Put another way, SIEMs serve as the glue that holds the rest of the cybersecurity toolchain together, enabling efficient and holistic management of risks.
In this task, SIEMs may be complemented by security orchestration, automation and response, or SOAR, platforms. SOAR platforms excel at helping businesses to manage their response to cyber threats after they have been detected in a SIEM. While some SIEM products also offer security incident management features, SOARs go further in this regard by making incident response management a core focus.
That said, SOAR is not a replacement for SIEM. Both types of tools excel in different areas. A SIEM is ideal for ingesting large amounts of data from disparate sources and detecting threats based on it, while a SOAR’s main purpose is to manage the response processes after the SIEM (or another source) has detected threats.
Learn more about SOAR vs SIEM.
Growing SIEM adoption
Although the SIEM category, as noted above, has existed since the mid-2000s, SIEM adoption continues to grow as more and more businesses recognize the importance of centralizing security information management and managed detection via a unified platform.
Gartner highlighted that the market grew from $3.41 billion in 2020 to $4.10 billion in 2021 – a 20% increase compared to a 3.9% decline the year before. They explain:
“The SIEM market is maturing at a rapid pace and continues to be extremely competitive. The reality of what SIEM was just five years ago is starting to detach from what SIEM is and provides today.”
This growth is partly driven by the fact that as of 2021, 90 percent of businesses still reported an inability to manage all of the security alerts they receive each day, according to 451 Research.
Furthermore, even businesses with a SIEM are often seeking newer, better security solutions. That’s true partly because the ability to unify security data with other types of data (such as logs and metrics about application performance) — something that conventional SIEM tools were not designed to do — has become critical for gaining maximum context about security risks.
In addition, organizations increasingly seek to leverage SIEM solutions that embrace open technologies and frameworks, such as OpenTelemetry, to ensure that they can collect and analyze as much data as possible with the help of a flexible, extensible framework.
The SIEM market will continue to expand as businesses embrace modern SIEM solutions that are more extensible, flexible and easier to use than conventional solutions.
Best practices for making the most of SIEM
Merely deploying a SIEM doesn’t guarantee that your business is reasonably safe against threats. Instead, deriving full value from a SIEM requires choosing a modern SIEM platform whose features extend beyond those of a conventional SIEM solution, then taking full advantage of those features.
Maximize data ingestion
The more data you ingest into your SIEM for analysis, the greater your ability to find and understand threats in time to contain them. Unfortunately, however, many businesses settle for limited data ingestion.
Avoid this shortcoming by choosing a SIEM solution that can support any type of data source or format and ensuring that it is configured to collect and analyze as much data as possible. Sometimes, a lone log file might be your only source for detecting a threat, or for gaining the essential context necessary to distinguish signals from noise when assessing risks. Modern SIEM solutions offer flexible pricing that supports the growth of data ingestion while keeping costs at a minimum.
Smart alert management
Analyzing more data means your SIEM will generate more alerts — and although the ability to detect all relevant threats is a good thing, having an endless stream of uncontextualized alerts to manage is not.
For that reason, it’s wise to take advantage of a SIEM product that allows you to triage alerts automatically so that your analysts know which ones to prioritize. The ability to root out false positives to reduce overall alert volume is important, too.
Gain threat context
The more information you have about each potential security threat, the better able you’ll be to know which alerts to prioritize and how to respond to each one.
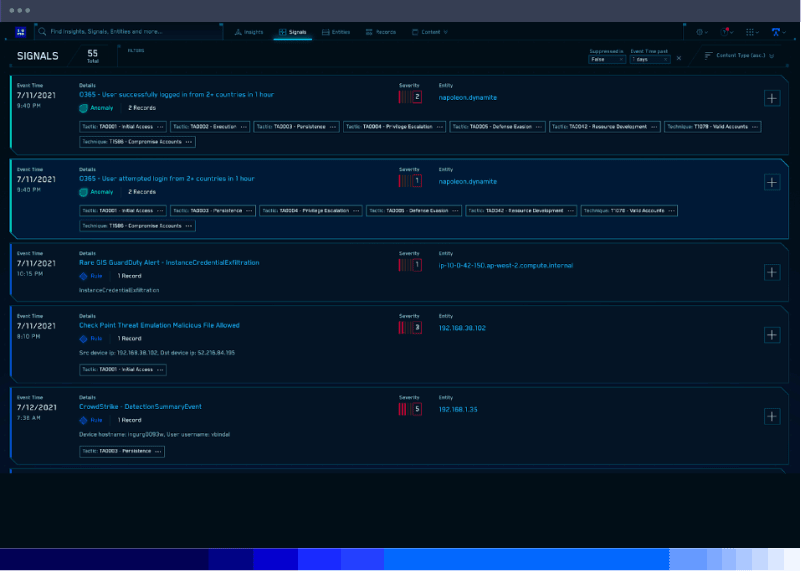
To gain this context, leverage SIEM features like pattern and threat intelligence matching in Sumo Logic Cloud SIEM, which help the security analyst to determine how likely it is that attackers will actually exploit each risk or vulnerability that their SIEM detects. Techniques like these allow SIEMs to function as much more than mere anomaly detection tools; instead, they provide actionable intelligence about what each anomaly potentially means and how best to react to it.
Collaborate across teams
In most businesses today, security can’t be the responsibility of the Security Operations Center (SOC) alone. It also requires participation by developers (who can fix vulnerabilities in software) and IT teams (who can mitigate risks by updating vulnerable applications or isolating compromised resources). Even non-technical users may need to be aware of security alerts and workflows to make informed decisions about threats that affect the systems they depend on.
These types of collaboration between the security team and other business units become possible when organizations utilize their SIEM as a common platform and tool for driving collaboration. Do this by using your SIEM to make security data available to all stakeholders (i.e., don’t keep it in a silo). Integrating this tool with other monitoring and observability tools to achieve unified data visibility across the organization takes collaboration even further.
Conclusion
As a centralized solution for detecting security risks and vulnerabilities, a SIEM serves as the foundation of security operations for modern businesses. It may be only one component of your cybersecurity toolchain, but it’s the most important component for translating the data that your IT resources generate into actionable insights about threats.
The role played by SIEMs will become only more important as cybersecurity challenges continue to grow in scale and complexity, forcing businesses to respond through the centralization, collaboration and enrichment functionality that SIEMs alone can provide.
Sumo Logic Cloud SIEM
Sumo Logic Cloud SIEM is delivered from a modern SaaS platform that enables unified visibility across any type of environment – from on-prem and public clouds to hybrid and multi-cloud architectures. With built-in alert triaging and management, threat hunting capabilities, automated threat intelligence and collaboration features designed to make security a collective responsibility shared across the business, Sumo Logic Cloud SIEM helps businesses stay ahead of threats, no matter which types of IT resources they operate or where they deploy them.