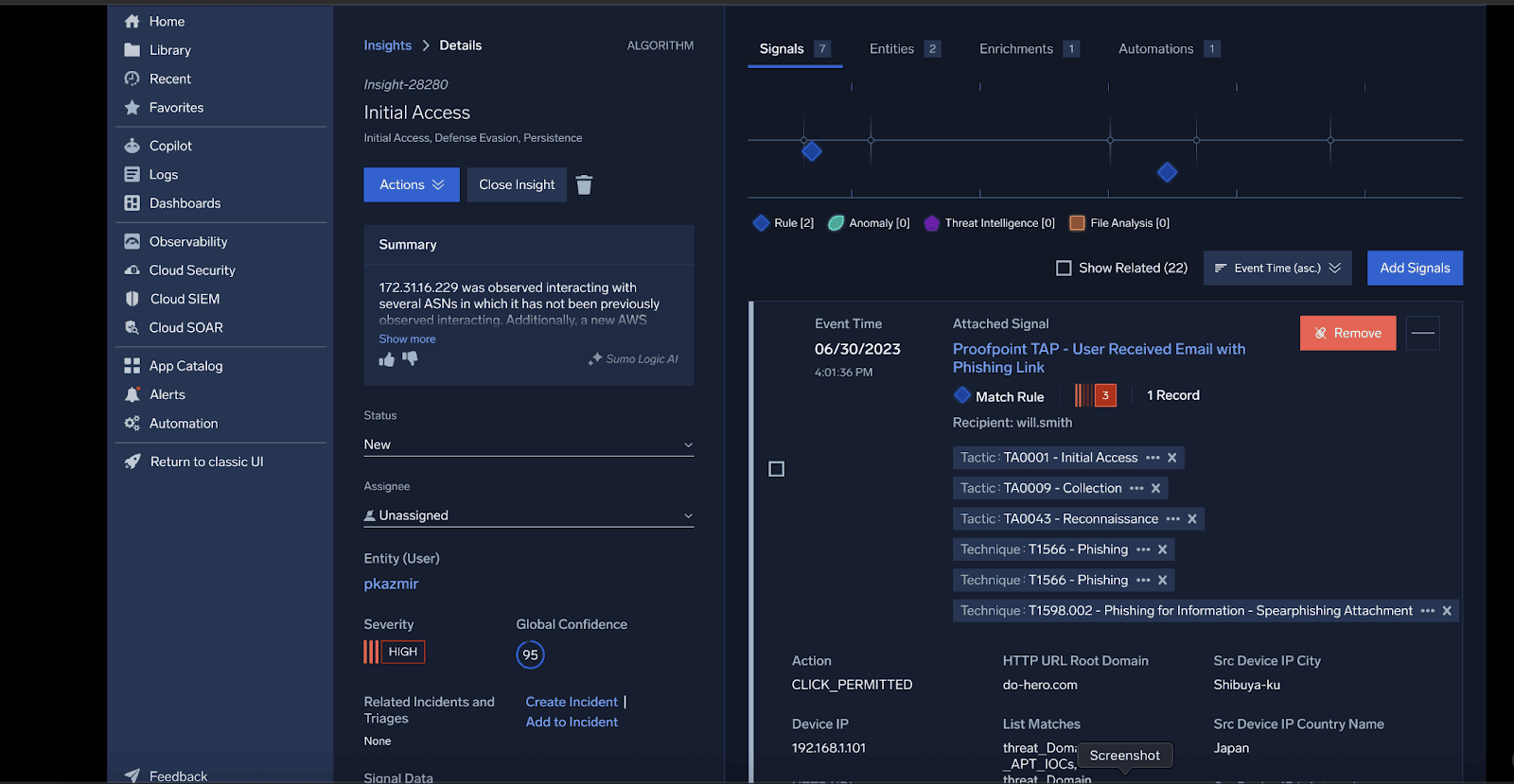
Know your cloud attack surface
Sumo Logic stores and provides full visibility and security analytics for your primary security data lakes and log data in one location, enabling more effective threat detection and hunting.
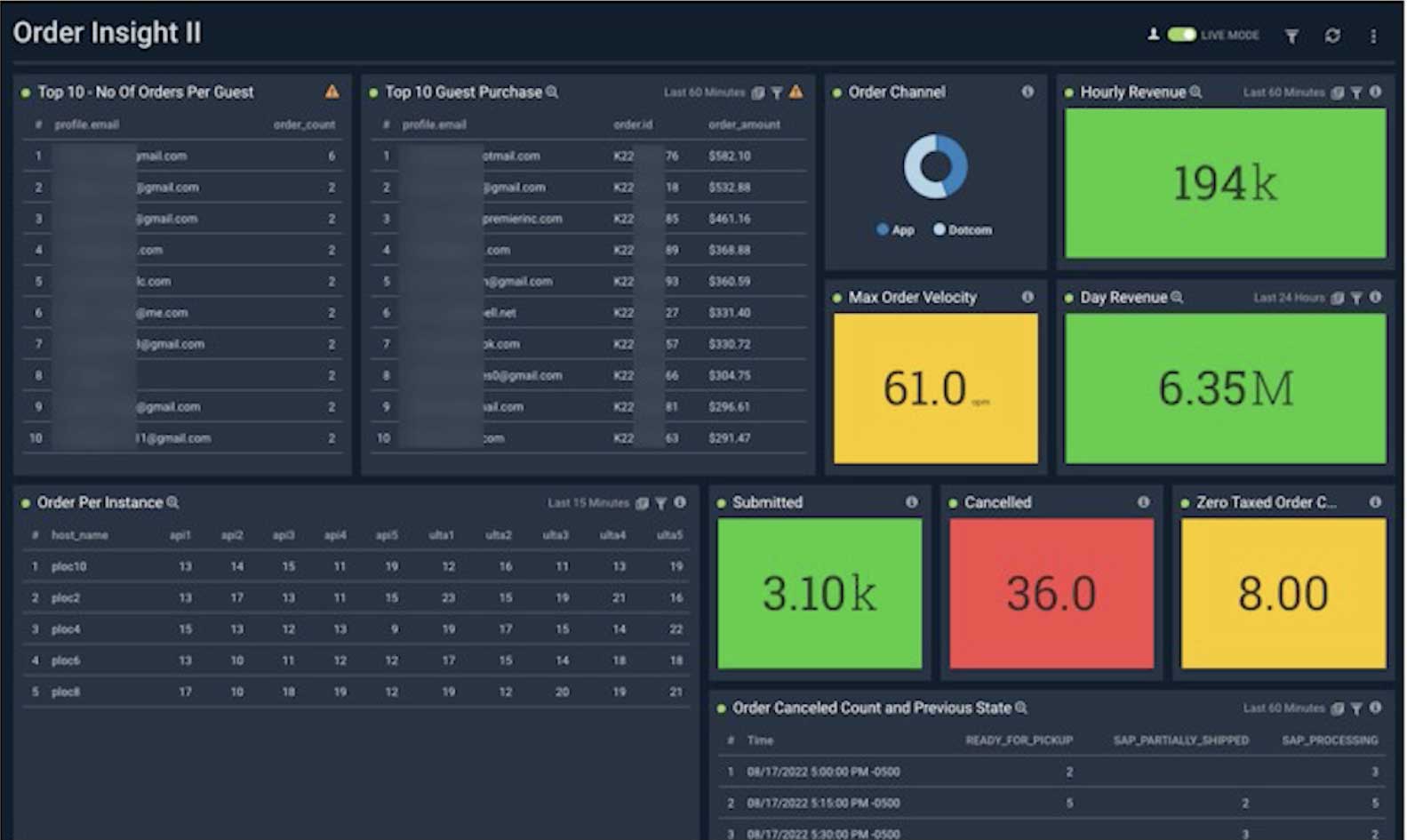
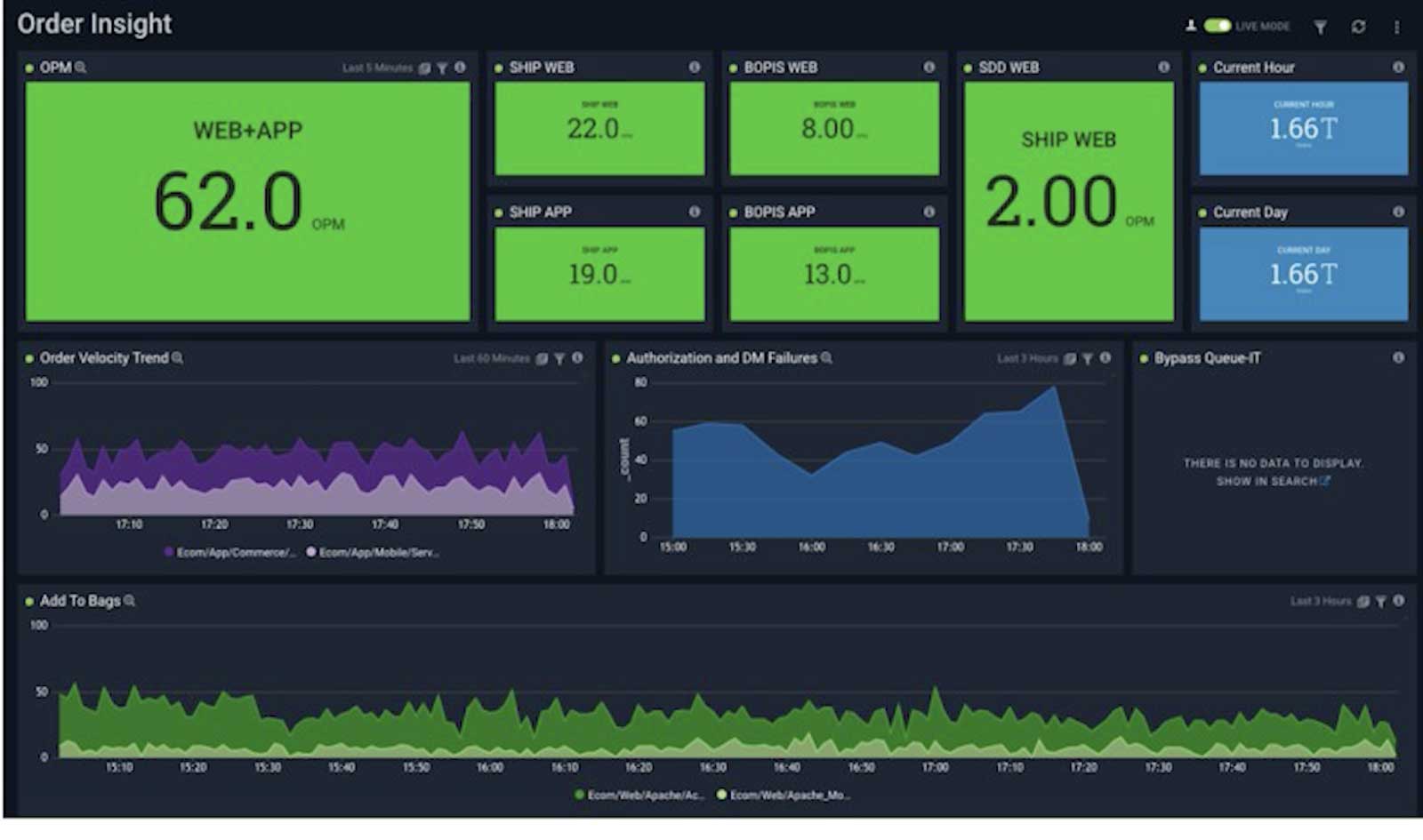
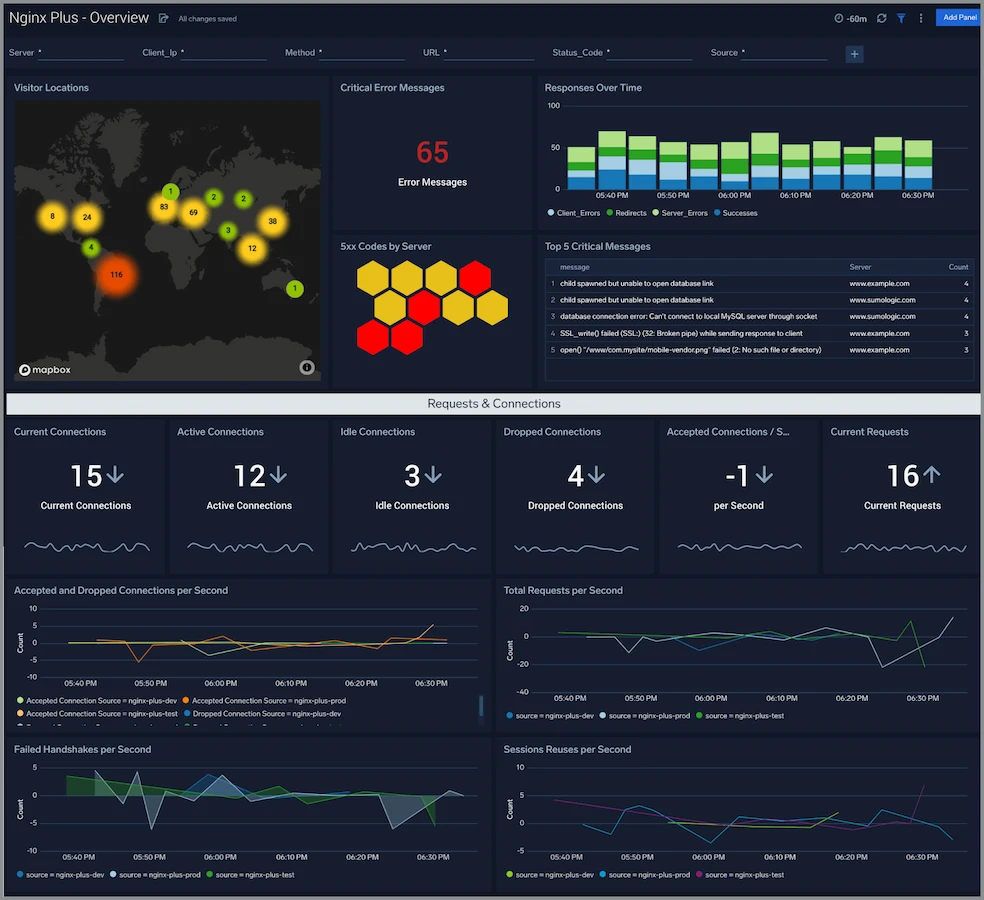
Security data lake: Collect, store, search and analyze data
Store and use unstructured and structured data in a single security data lake. Cost-effectively demonstrate compliance plus threat detection and investigation from a central, secured location.

Audit and compliance
Masters of Data Podcast

Your logs are exploding. Your team is drowning. Here’s your lifeline
Your SIEM is broken. Your attackers know it. Here’s what 500+ security leaders are doing about it

376% ROI in three years. Four-month payback. IDC just proved your CFO wrong about security spend
450+
Powerful
Integrations
Secure
by design



Additional resources

Splunk vs. Sumo Logic
Splunk’s siloed approach to log analytics and SIEM increases deployment cost and complexity. With Sumo Logic, you’ll eliminate bursting fees and scale seamlessly.

Datadog vs. Sumo Logic
Datadog can’t handle unstructured data. See why Sumo Logic’s unified approach across logs and a cloud-native SIEM set it apart.
Is tool sprawl derailing your budget?
Stop the sprawl. Consolidate your tools. Save time and money.

Five Sumo Logic hacks that’ll make you a log ninja
These 5 hacks turn hours of work into seconds of clicks. No coding. No complexity. Just results.
FAQ
Still have questions?
Yes, a company can build its own security data lake. But it is complex and resource-intensive. Building a security data lake involves setting up a flexible and scalable repository to store raw and unprocessed security-related data from various sources within the organization. Companies should consider the long-term costs and resource commitments involved in building and managing a custom security data lake compared to utilizing existing cloud-based data lake services or specialized security data lake solutions provided by vendors.
With Sumo Logic, you can keep the data you need for virtually as long as you need it, while other less important data can be retained for a shorter period, reducing your overall cost of operation. Set a data retention period and edit it at any time. The minimum retention period is one day, and the maximum retention period is 5,000 days, which easily surpasses even the most lengthy data retention requirements for even the most stringent compliance frameworks.
All data are ingested into Sumo Logic is managed in a secure and compliant manner right out of the box. More than 2,400 companies and organizations use and trust our cloud-native platform, which employs AES-256 encryption to protect data at rest and TLS for data in transit, with security controls at every application layer and a zero-trust segmentation model.
Sumo Logic maintains multiple compliance certifications—including PCI-DSS and HIPAA certifications, ISO 27001, FedRAMP Moderate Authorization, and SOC 2 Type 2 attestation. Sumo Logic also works directly with top security industry auditors and offers a paid bug bounty program with HackerOne. Plus, we also have a full-time dedicated team performing continuous and ongoing software reviews and penetration testing to keep our customers’ data safe and secure. We spend millions annually to maintain these attestations, which in turn is extended to our customers free of charge.
An external audit by a compliance auditor (also known as an external auditor or compliance officer) will conduct an audit process to assess the internal policies of a company’s compliance program and determine if its fulfilling its compliance obligations.
All data at rest within the Sumo Logic system is encrypted using strong AES 256-bit encryption. All spinning disks are encrypted at the OS level and all long-term data storage is encrypted using per-customer keys which are rotated every twenty-four hours.
When it’s time for an audit, the Sumo Logic platform increases understanding, streamlines the auditing process and ensures ongoing compliance with various security regulations and frameworks in the following ways:
- Centralize data collection, capturing a wide range of organizational data from wherever it originates, empowering organizations to monitor and learn from it.
- Make various data types available with 100% visibility and visualize them in compelling, configurable dashboards for real-time monitoring and insights.
- Find any data at any time using query language to create filters and search parameters — whether it relates to regulatory compliance or internal security controls.
- Leverage machine learning analytics to improve and streamline audit processes and expedite compliance using tools like our PCI Dashboard.
- Cost-effective data storage that maintains attestations, such as SOC2 Type II, HIPAA, PCI Service Level 1 Provider, and a FedRAMP moderate authorized offering.
- Real-time monitoring of incoming data and security controls to identify anomalies that could signal a security risk, cyber threats, vulnerability, security threat or non-compliance.
Numerous data integrations and out-of-the-box applications that properly collect and catalog all data.