What is endpoint security?
Endpoint security is a cybersecurity strategy focused on protecting every endpoint device connected to a corporate network. An endpoint can be any connected device — including laptops, servers, workstations, IoT devices, or mobile devices — that communicates with your IT infrastructure.
Modern endpoint security solutions are designed to prevent, detect, and respond to cyber threats targeting these devices. As organizations adopt cloud services and support remote work, endpoint security has become a foundational layer of network security and overall cybersecurity strategy.
Without strong endpoint protection, attackers can exploit vulnerabilities to gain unauthorized access, steal sensitive data, or launch large-scale attacks.
Key takeaways
- Endpoint security limits cyber threats and malware to end users by implementing a series of checkpoints and protocols that devices must pass through when connecting to the network.
- There are two types of endpoint security approaches, Endpoint Protection Platform (EPP) and Endpoint Detection and Remediation (EDR).
- There are basically two ways in which endpoint security can scan, maintain, monitor, and protect your network from device-related threats. Those two models include client-server protection and SaaS models.
- Sumo Logic provides organizations with intelligent, state-of-the-art security solutions to keep their endpoints and networks safe from security threats.
How does endpoint security work?
Every endpoint device represents a potential entry point for an attack. With employees accessing systems from home networks, mobile devices, and cloud environments, the traditional security perimeter no longer exists.
Endpoint security is important because it:
- Prevents malware infections and advanced threat attacks
- Protects sensitive information from data breaches
- Reduces the risk of unauthorized access
- Enables proactive threat detection and threat hunting
- Supports zero trust security models
- Strengthens overall cybersecurity posture
A single compromised device can expose an entire organization to significant risk.
There are two ways in which endpoint security can scan, maintain, monitor, and protect your network from device-related threats. Those two models include client-server protection and SaaS models.
- Client-server model: Client-server models refer to the traditional way in which IT teams practice their endpoint security strategy. Rather than relying on a cloud to maintain the database to store threat-related information, client servers store all the data and require that all the data is maintained locally. Client-server models require that the endpoint software be installed directly onto the device. They connect the client, server, and network, allowing clients to mix and match software, hardware, and operations. While this flexibility is one of the more appealing aspects of client-server models, it’s also what makes them vulnerable to breaches in security.
- SaaS model: The SaaS model is a cloud-based, third-party host model. Rather than purchasing a physical copy of an application or endpoint software and installing it on your device, SaaS models rely on vendors to maintain and manage their endpoint security software through the cloud. This model helps free up the burden of maintaining all the data locally. Data loss prevention SaaS solutions help protect intellectual property in both the cloud applications and through endpoint devices. SaaS models remain popular for their flexibility, scalability, on-demand resources, fast implementation, easy updates, and more.
What is considered an endpoint?
An endpoint device itself is any internet-capable device that is connected to the network. These include:
- Laptops
- Computers
- Tablets
- Mobile devices
- Thin (lean) clients
- Printers
- Servers
- Workstations
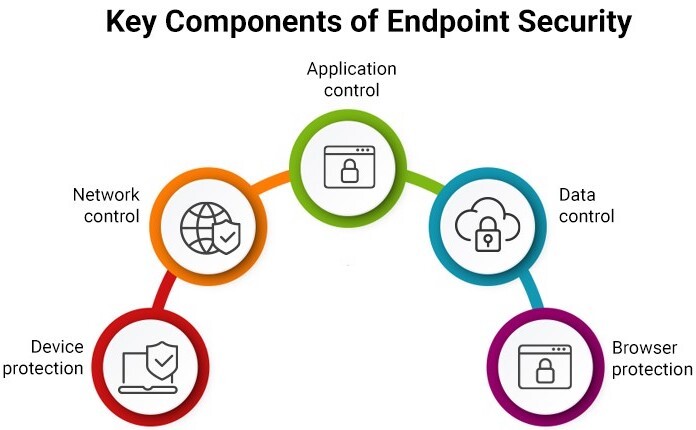
What are the components of endpoint security?
So what should you expect a robust endpoint security solution to entail? What are the various components and functionalities that you should be looking for?
- Cutting-edge antivirus, anti-spyware, and anti-malware tools that scan, detect, and remove viruses present on endpoint devices and systems
- Advanced firewalls, either client or cloud-based, that act as gateways within the IT infrastructure
- Application whistling capabilities that enable IT administrators to monitor and exercise control over which applications are permitted on network endpoints
- A robust Network Access Control system that authenticates users matches its compliance with security policies, and restrictions permission depending on the user’s current security compliance status
- Data encryption to protect emails, endpoints, and databases
- Host Intrusion Prevention Systems that monitor host devices for suspicious activity by analyzing event logs
- Proactive forensics capabilities that allow admins to identify, isolate, and remove threats
- Features that rely on machine learning and automation to provide real-time monitoring and threat detection
Sumo Logic, endpoint protection, and big data
Sumo Logic provides organizations with intelligent, state-of-the-art security solutions to keep their endpoints and networks safe from security threats. Our operational analytics platforms leverage machine learning and big data to effectively identify threats and forensically investigate security inconsistencies.
Protect all your devices with the power of Sumo Logic today.