Nowadays, it’s not uncommon for enterprise IT leaders to find themselves in a situation that seems like a catch-22. On one hand, they’re expected to make data-driven decisions that improve productivity and profitability in a business. On the other, they’re preoccupied with their core responsibilities such as protecting critical systems, maintaining network security, and accelerating investigations when a security event occurs.
Traditional tooling won’t keep up with modern systems. You need adaptive processes, deeper collaboration across teams, and a stronger reliance on automation. Discover the top capabilities Sumo Logic Cloud SIEM provides so you can effectively manage security at scale.
Top 10 SIEM best practices
1. A unified solution for all DevSecOps
In many organizations, cloud resources, applications, and data sources are owned by different teams. This fragmented ownership makes centralized visibility of security data difficult and weakens compliance and risk management efforts. Lack of a centralized security strategy can create security gaps and put critical data and other resources at risk. SIEM solutions are instrumental in eliminating these challenges by providing full-stack visibility, visualizing logs, metrics, and performance data to ensure reliable delivery.
2. Democratize security across the organization
Security shouldn’t live with a single team or a handful of experts. Maintaining security is everyone’s responsibility, and collaboration on security practices should be shared to the maximum extent.
With a modern SIEM platform, teams across engineering, IT, and the security operations center (SOC) can analyze data, investigate issues, and take action. This shared ownership improves collaboration, reduces response times, and strengthens overall security posture.
3. Elasticity of scale
Moving into the cloud means your IT infrastructure is going to grow; that’s why you’ve switched to the cloud in the first place, right? Your organization is growing its data exponentially with every new tool in the architecture. A scalable SIEM system must handle this growth without performance degradation.
SIEM solutions supporting multi-tenant public cloud can grow ten times without any notice or prior planning. Our solution will move at the speed of your business and will fully support you during emergencies while fully unlocking your growth potential.
4. Consolidate core security operations
Cloud SIEM provides support to all your key departments: IT ops, DevOps, SecOps, engineering, customer success, product, and data science teams. Open APIs ensure all teams can plug in and get data easily. There’s no need to worry about antiquated user limits or complicated restrictions. Our Cloud SIEM solution features real-time alerting and dashboarding to capture all issues, allowing you to make split-second decisions no matter how much data you have.
5. Seamless multi-cloud support
Multi-cloud adoption has increased, bringing complexity and noise. Legacy tools struggle to correlate data across providers, weakening threat intelligence and visibility.
SIEM platforms with built-in SIEM integration support AWS, Azure, GCP, and hybrid environments out of the box. This single pane of glass approach improves detection and simplifies security orchestration across environments.
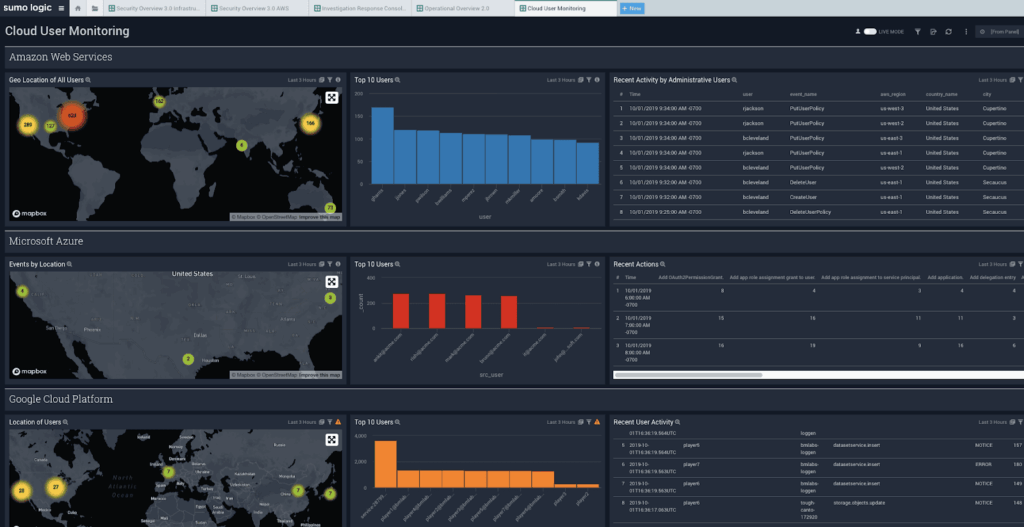
6. Leverage machine learning
SIEM solutions adopt machine learning models for outlier detection, anomaly detection, log reduction, UEBA rules, and time comparisons of states for threat detection at a large scale, including unknown and new sources. Sumo Logic can also uncover root causes from thousands of log lines using patented Log Reduce and Log Compare pattern analysis, and detect anomalous behavior with Outlier Detection.
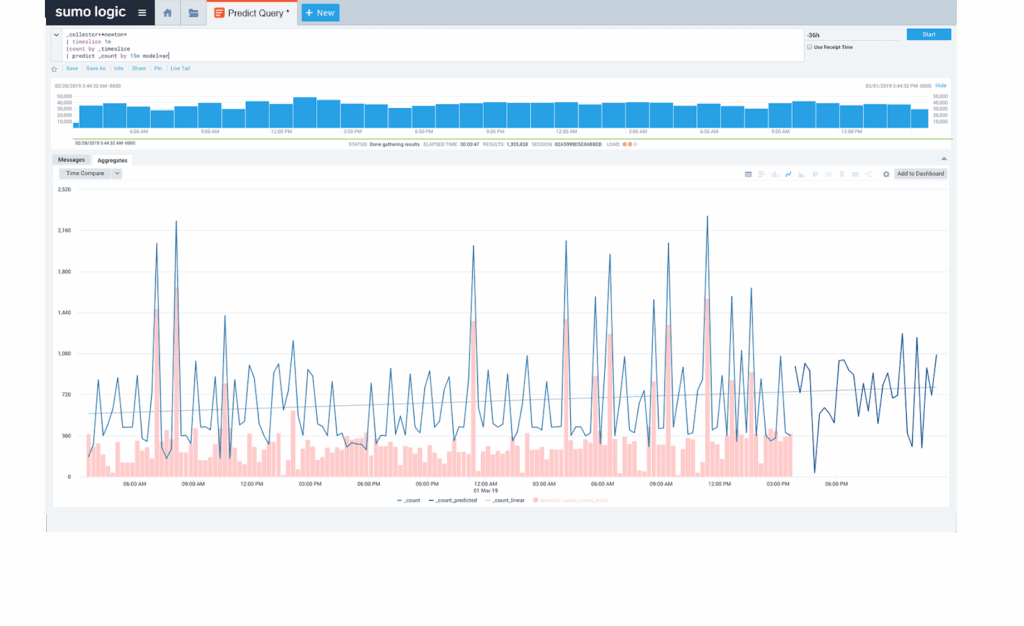
7. Use agentic AI to accelerate security operations and incident response
Sumo Logic Dojo AI is designed to reduce manual effort across detection, investigation, and response. These agents help you summarize security events, accelerate investigations, and provide context so you can better understand your environment.
By handling repetitive analysis and guiding analysts through the next steps, you achieve consistent incident response while reducing alert fatigue and improving productivity.
8. Optimize costs with cloud-scale economics
Not all data is created equal. Some data (e.g., application errors) has a limited lifespan, while other data (e.g., audit data) must be retained for much longer.
With SIEM solutions, you can easily classify data for collection, analysis and storage. Our solution features flexible pricing, which allows you to determine the retention period for each of your datasets. You can optimize costs for your use cases while preventing data from being discarded or kept unnecessarily when redundant. In addition, our model does not charge for users and provides optimal performance at all times as you scale.
9. Large-scale deployment
Cloud SIEM solutions are significantly faster to deploy than traditional SIEM solutions, which often result in failure. Learning to navigate them is also a lot easier, which is a huge benefit for any enterprise. Traditional SIEMs were usually used by up to two experts who bore a huge responsibility, and companies were fully dependent on them, which created additional risk.
With Sumo Logic, anyone within the company can learn to use it and even get certified. Creating tickets and workflows will become much easier, if not fun. Above all, our solution can support massive cloud deployments by providing real-time visibility into operational status, KPIs, usage metrics and compliance violations.
10. An ecosystem-first platform
The next-generation security operations center is all about ecosystem play. Your SIEM platform should fully support this with built-in apps, APIs, webhooks, and deep, built-in plumbing, so that it fits your architecture.
Sumo Logic’s Cloud SIEM is built on these foundations, ensuring that best practices are implemented with every customer, regardless of their level of security expertise.
SIEM alerts best practices
When it comes to alerts, there are several best practices to follow to reduce noise and improve response times.
- Determine the scope: Before creating any alerts, check your existing set of alerts to prevent redundancy.
- Compliance alignment: Globally, your organization may need to comply with various regional and federal laws. Understand which regulations require custom alerting to be created.
- Clearly define your alerts: As you create SIEM alerts, be descriptive of their purpose. This ensures that you don’t create multiple alerts for the same issues.
- Always test your alerts: Thoroughly testing your SIEM alerts is an absolute necessity to ensure they trigger consistently and correctly.
- Audit regularly: Set up a regular audit schedule to review your alerts and maintain accuracy.
SIEM implementation best practices
Successful adoption starts with strong planning. Here are some best practices for implementing SIEM in InfoSec and DevOps teams.
- Determine requirements: As you implement a SIEM system, it’s essential to establish your requirements and needs from the outset by understanding the use cases for your SIEM solution and creating objectives.
- Always “try before you buy”: Whether it’s a free trial or a small-scale pilot, you’ll want to test SIEM solutions prior to implementing them across your entire technology infrastructure.
- Create a comprehensive incident response plan: An incident response plan is a detailed list of who is responsible for what during a security breach or other event. While a SIEM can identify threats and events, you’ll still need to have a formal plan in place for how to address these situations at all levels.
SIEM logging and monitoring best practices
Below you’ll find SIEM logging and monitoring best practices. Keep in mind, as you implement your SIEM, you’ll want to include our best practices for implementation, alerting, and logging.
- Be the “tortoise” and not the “hare”: One of the most important SIEM logging and monitoring best practices is to start off slow. Begin by isolating a few different objectives, examining existing protocols, and brainstorming how you can continue logging and monitoring with your new SIEM system.
- Tune your correlation rules: SIEM works by collecting vast amounts of log data, monitoring, analyzing, and correlating it to determine whether the data should be flagged as a security alert. Tuning these correlation rules beyond preconfigured rules is an absolute must for your organization.
- Be efficient with security log data collection: When you set your SIEM to log and monitor your data, it’s important to determine early on how much data you want to collect. If you collect too much, you may collect too much “noise,” but too little data, and you could miss valuable events.
- Use the MITRE ATT&CK framework: Map your coverage using MITRE ATT&CK to find gaps and have a maturity path.
Following these SIEM logging best practices ensures long-term performance, scalability, and stronger security outcomes.
Learn more in our ultimate guide to modern SIEM.