It’s" class="redactor-autoparser-object">https://www.sumologic.com/blog... becoming increasingly harder to manage the volume of threats coming into enterprise networks as attackers become more sophisticated, the threat landscape expands and enterprises continue to adopt modern applications at cloud scale. This, combined with the challenge of staying up-to-date on new and evolving compliance regulations, including Payment Card Industry Data Security Standard (PCI DSS), has put more responsibility on security and operations teams to take a more proactive role in identifying and remediating potential malicious attacks to their modern day infrastructures.
One first line of defense against external threats is setting up a firewall to protect the network perimeter. Palo Alto Networks is one of the industry leaders that offers next-generation firewall capabilities to provide visibility and granular control of network activity based on application, user, and content identification.

That’s why today at the Palo Alto Networks’ Cloud Security Summit in New York, Sumo Logic is excited to announce extended support for Palo Alto Networks with two new applications for PAN-OS 8, that give administrators and security operations center (SOC) teams instant insight into their security and compliance posture with advanced visualizations, alerts and reporting.
New Sumo Logic Apps for PAN-OS 8
Sumo Logic has recently released the following apps for PAN-OS 8:
- Palo Alto Networks 8: This app analyzes log data from various kinds of logs produced by PAN-OS 8 and gives you visibility into threats detected, firewall traffic, endpoint protection and operational aspects of PAN-OS 8.
- PCI Compliance for Palo Alto Networks: This app analyzes log data from firewall traffic logs and offers dashboards to monitor firewall traffic activity for compliance with various PCI DSS 3 compliance requirements.
The following sections talk about how these apps work and help accelerate your efforts towards maintaining your security and compliance posture.
Collecting Logs from the PAN-OS 8
Palo Alto Networks provides a rich set of log messages for monitoring system, security and network traffic related events.
The apps work with the following set of logs for Palo Alto Networks V7 and V8:
- Traffic Logs
- Threat Logs
- System Logs
- Config Logs
- Correlated Events Logs
- Traps Logs (Endpoint Protection System)
To begin, configure an installed collector with a Syslog source that can receive logs and events from Palo Alto Networks 8 devices.
Once the log source is configured, the Sumo Logic app can be installed. Navigate to the Apps Catalog in your Sumo Logic instance and add the “Palo Alto Networks 8” or “PCI Compliance for Palo Alto Networks 8” app to your library after providing the sources configured in the previous step.
For more details on app configuration, please see the instructions on Sumo Logic’s DocHub for the Palo Alto Networks 8 app or the PCI Compliance for Palo Alto Networks app.
The Sumo Logic App for Palo Alto Networks 8
The following sections talk about how the new Sumo Logic app for Palo Alto Networks 8 helps across various perspectives.
The Threat Perspective
This app gives you an overview of threats identified in your infrastructure. The Palo Alto Networks 8 – Threat Overview dashboard panel helps you get a count of threats by type such as spyware, virus, vulnerability, wildfire etc.
With this dashboard, you will be able to quickly identify the most widespread threats in your environment by looking into “Threats Impacting Most Destination IPs” panel. The “Dest IPs Observing Multiple Threats” panel helps you identify the most vulnerable IP addresses that are being impacted by the most number of unique threats.
The “Src IPs Generating Multiple Threats” panel helps you identify those source IPs, which are potentially spreading the most threats in your environment.
As a general principle, whenever there is malicious activity detected on a network, it is usually the same user that either spreads or is impacted by the threat(s). The “Users Impacted by Threats” panel helps identify users impacted by threats. Your SOC team can use this information to determine a strategy for handling specific actions around common threats, destination IPs, source IPs and/or users.
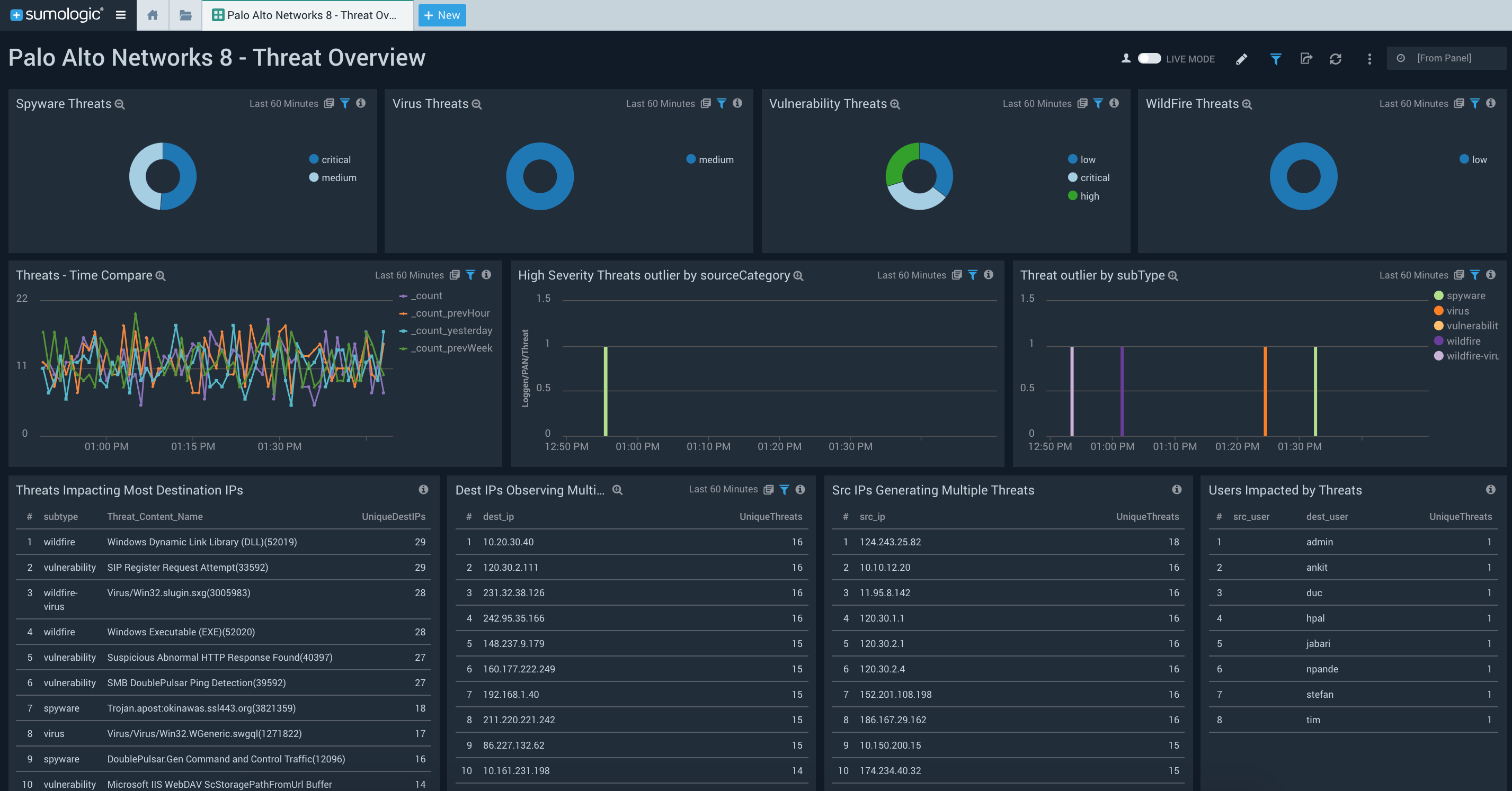
You can drill down into the specifics for any of these panels. For example, if you click on the “Spyware Threats” panel it will launch the linked dashboard Palo Alto Networks 8 – Threat Analysis, in which you will be able to understand details of each threat via various panels.
You can also use this dashboard to gain additional information around rules fired, actions taken, threats seen over time, threat feeds, app severity and threat outliers, and threat directions.
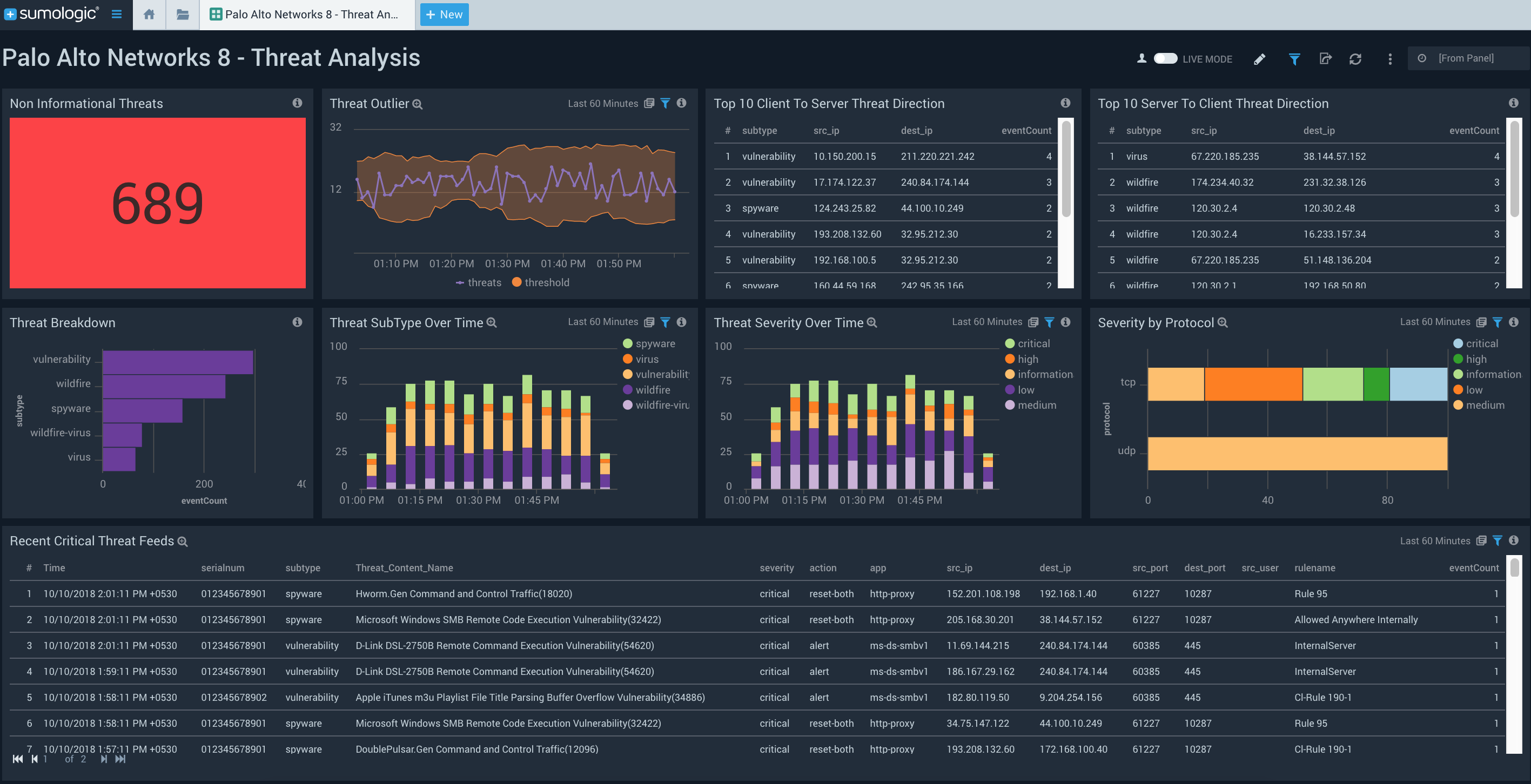
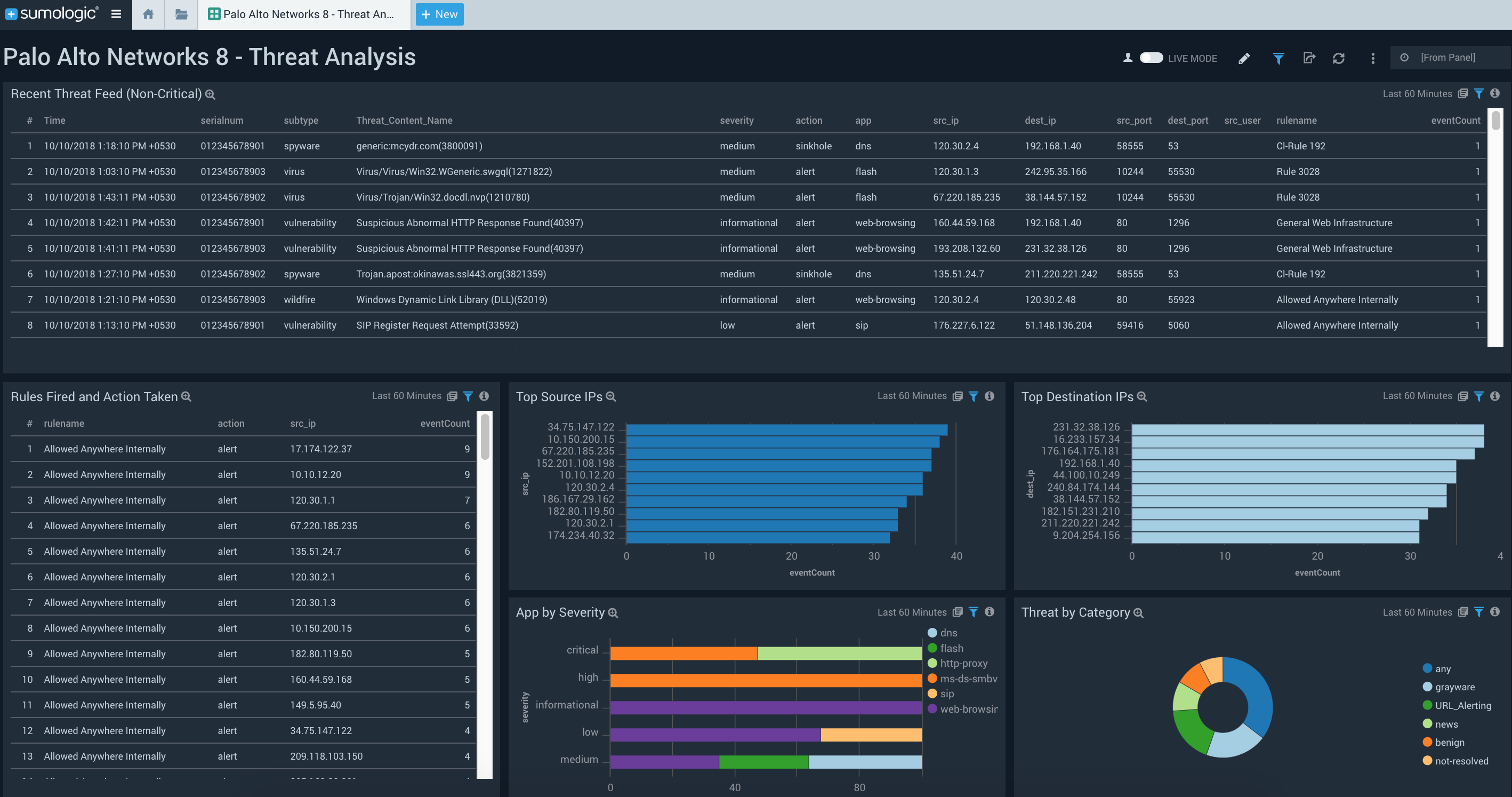
The Palo Alto Networks 8 – High Severity Threats dashboard on the other hand, helps you track, monitor and focus on important high and critical severity threats.
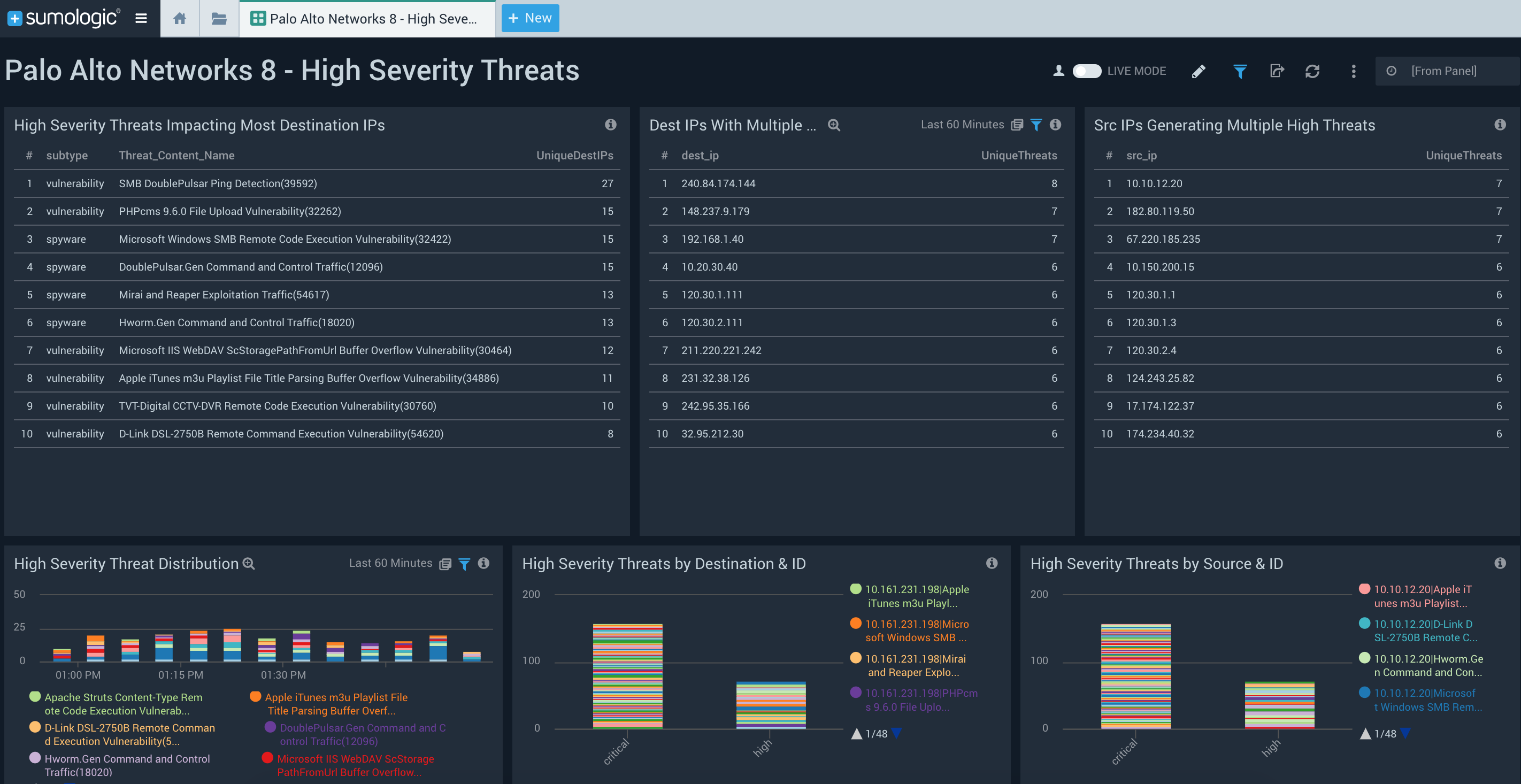
The Firewall Traffic Perspective
The Palo Alto Networks firewall will log a correlation event when the patterns and thresholds defined in a correlation object match traffic patterns on your network. The Palo Alto Networks 8 – Correlation Analysis dashboard analyzes correlation logs and helps you quickly identify hosts that are compromised based on various levels of likelihood.
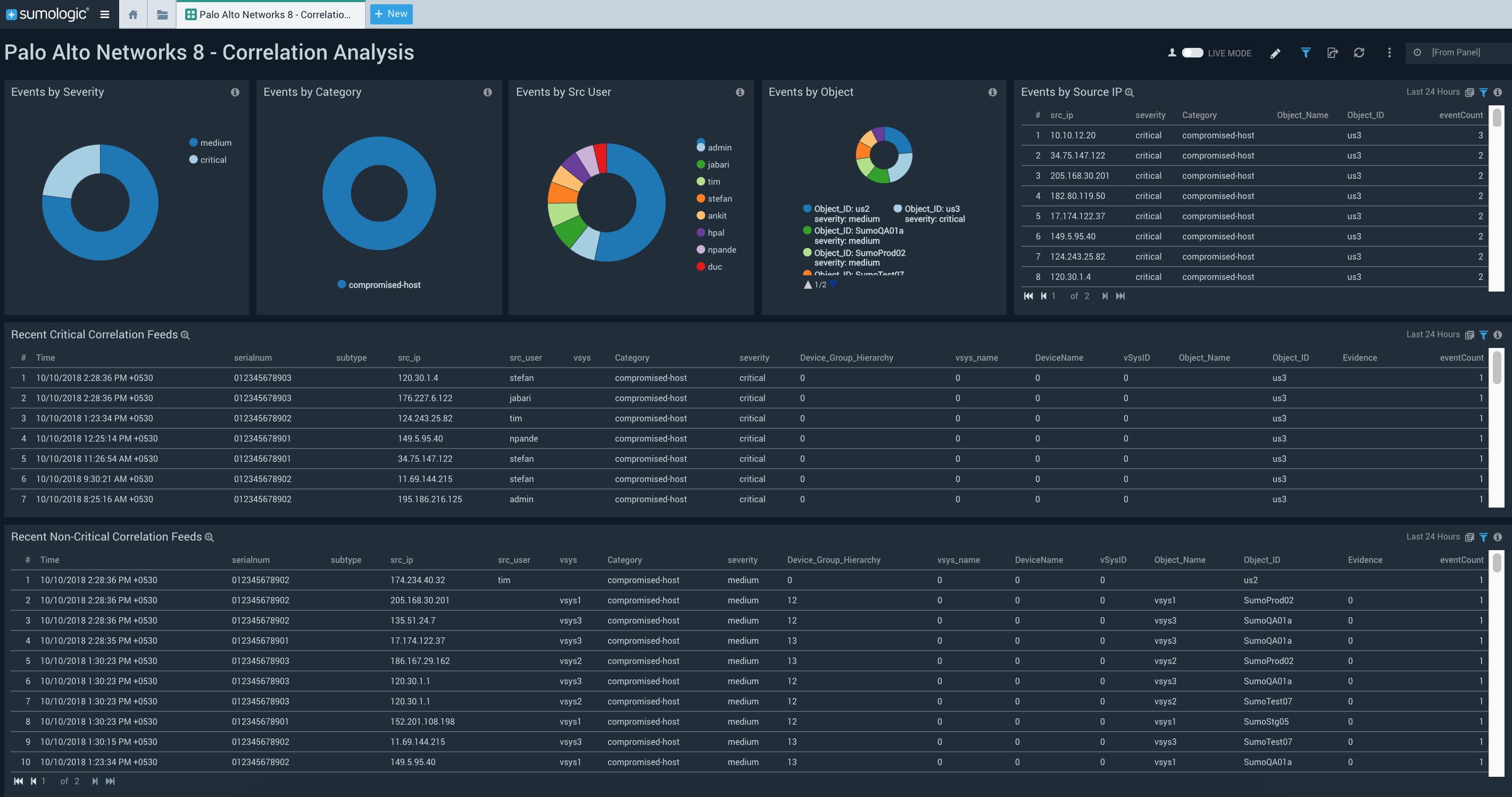
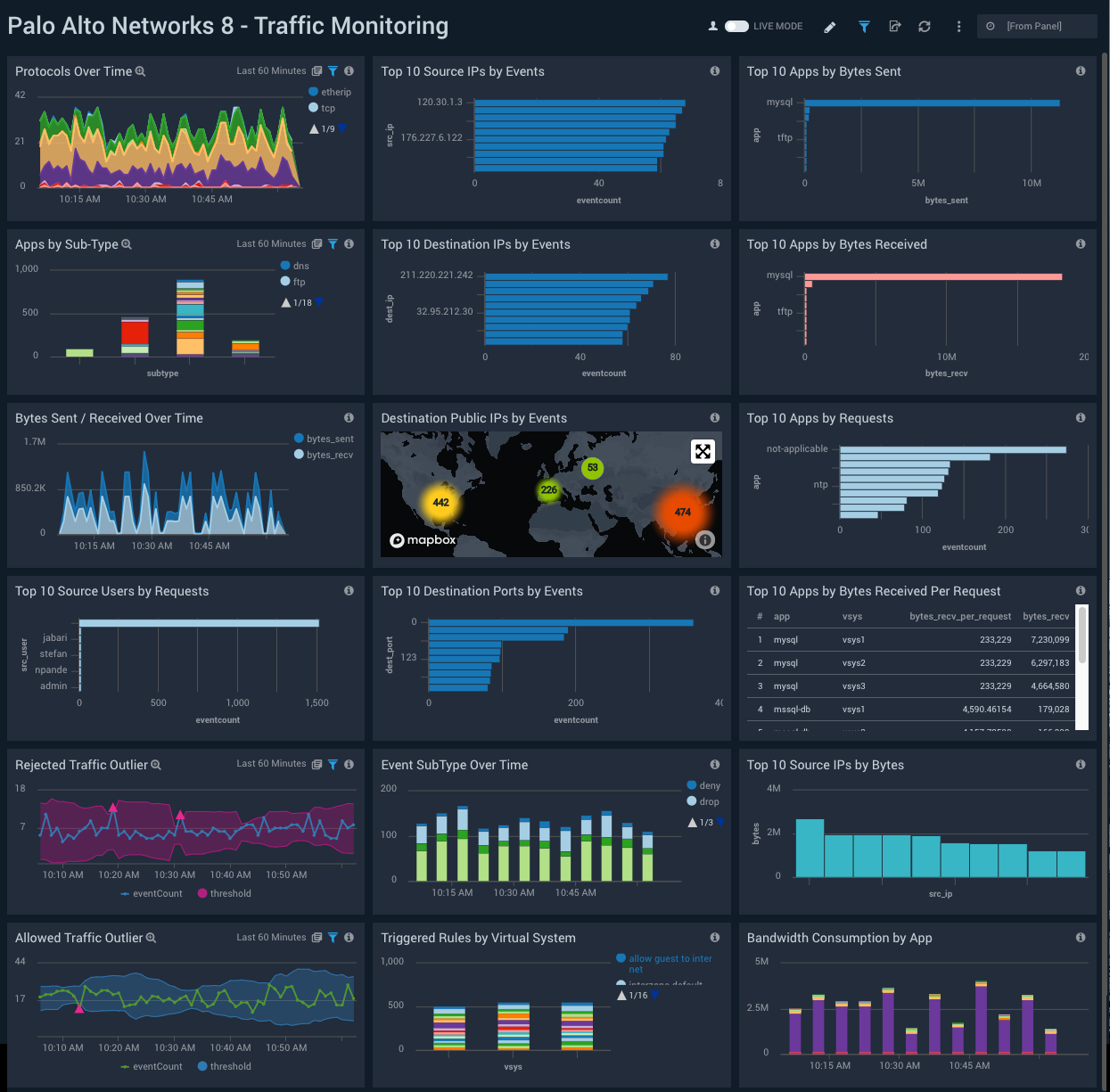
With this dashboard, you can also monitor the types of content being accessed by various apps and virtual systems as well as the bandwidth consumed by specific apps in order to take the necessary corrective actions. Using the geolocation map, you can track source and destination locations, and determine whether a location is expected and then make a decision to block it in your rules if necessary.
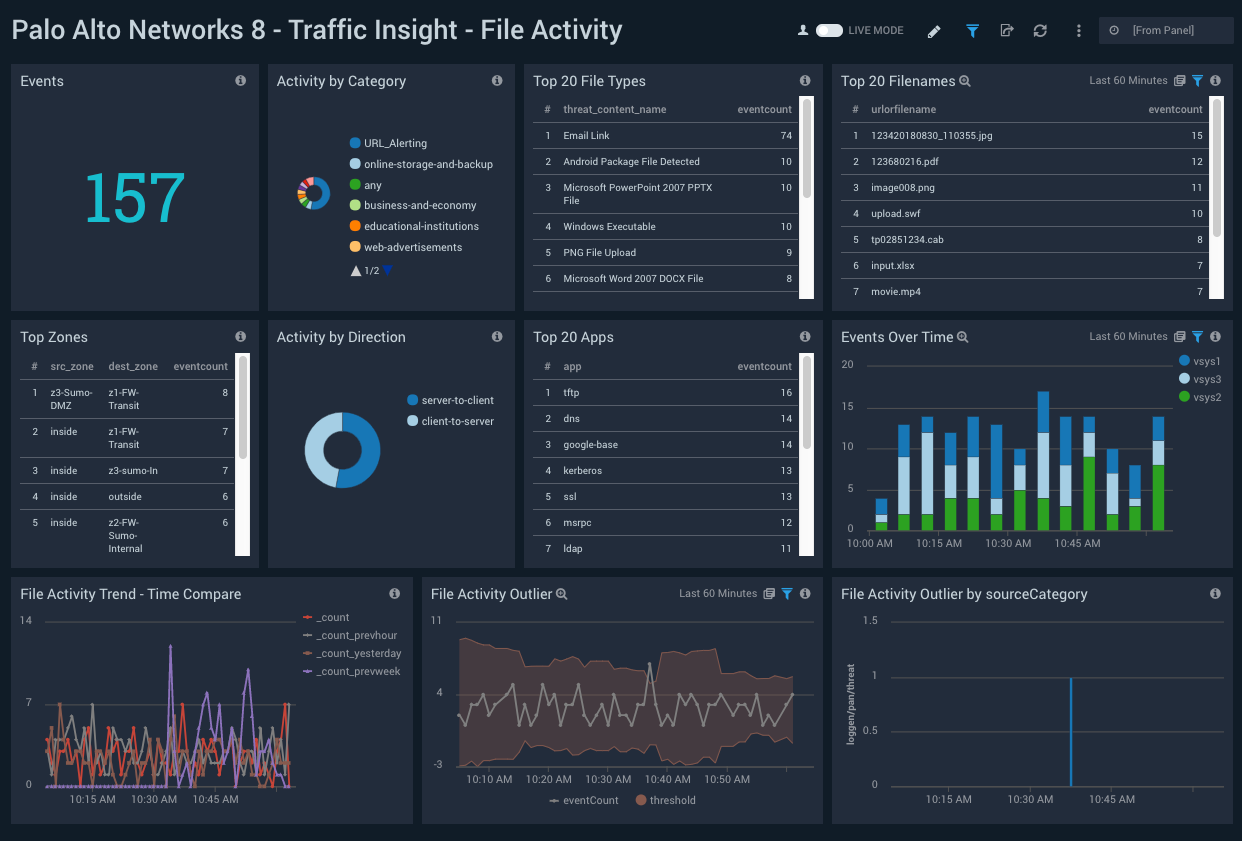
The Palo Alto Networks 8 – Traffic Insight – File Activity dashboard helps you track and monitor file uploads and downloads, suspicious file types and web browsing activities. It also provides insight into sudden changes in activities through outliers.
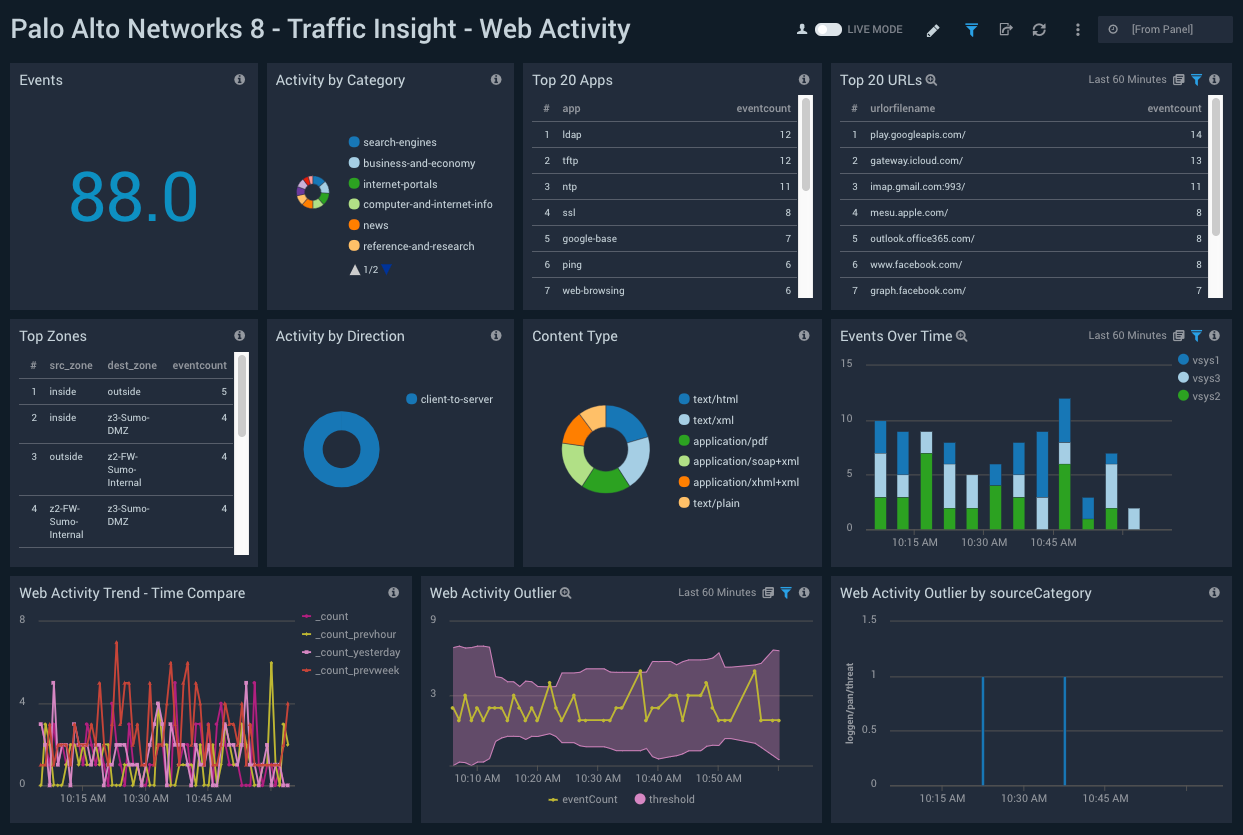
Use the Palo Alto Networks 8 – Traffic Insight – Web Activity dashboard also enables you to monitor end users’ file web browsing activities as well as track URLs and content being browsed using various panels. It also provides insight into unexpected activity through outliers and you can compare current activity trends with the previous hour, the same time yesterday, and the same time last week with the “Time Compare” panel.
The Endpoint Protection Perspective
Palo Alto Networks provides Traps, an advanced endpoint protection system. You can look into how the Traps agent and the Traps ESM server is managing endpoints in your infrastructure using the Palo Alto Networks 8 – Traps V4 Monitoring dashboard shown below.
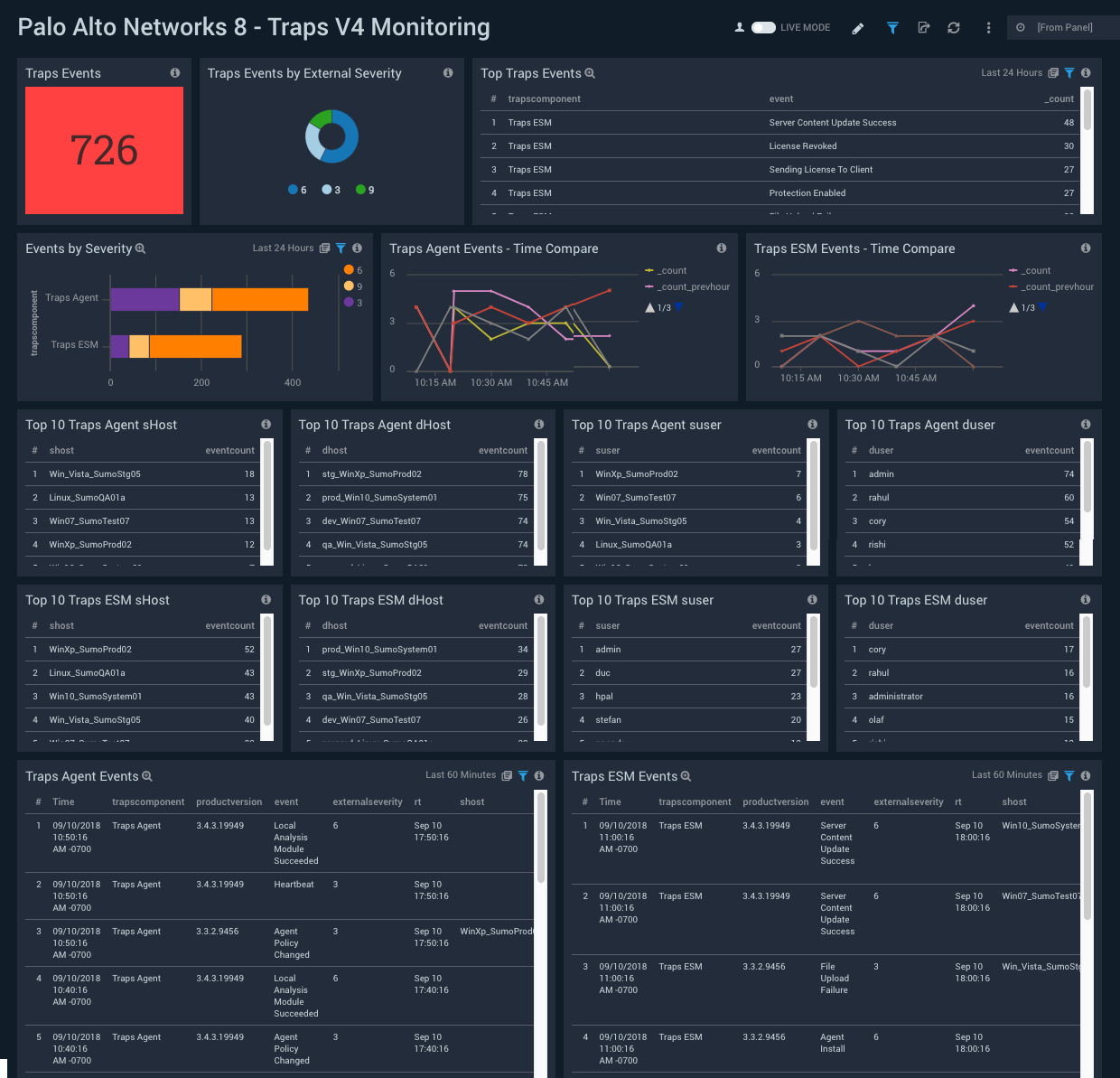
The Operations Perspective
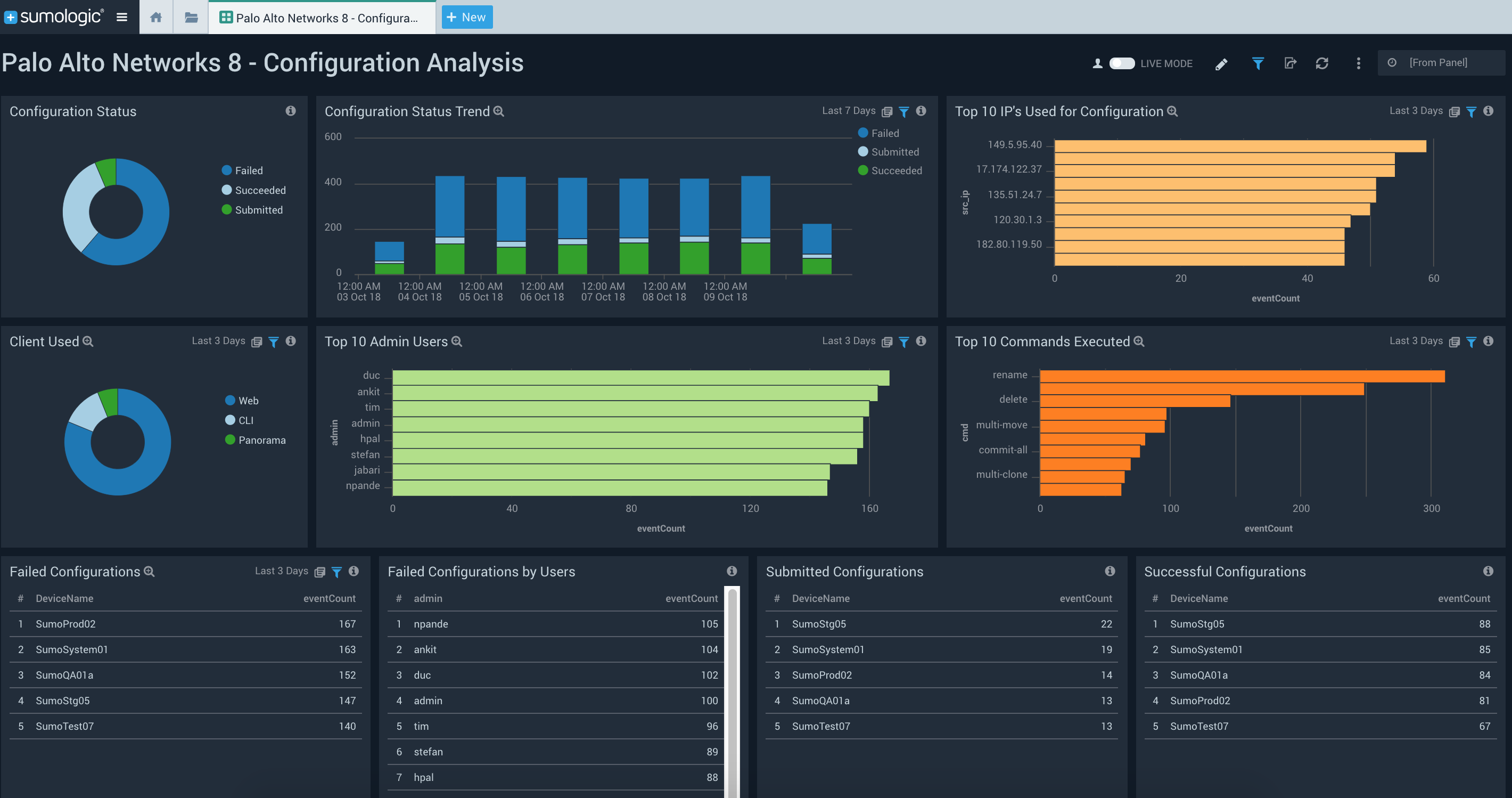
The Palo Alto Networks 8 – Configuration Analysis dashboard helps you understand firewall configuration changes. You can identify who performed a configuration change and on which system. This dashboard also helps you identify failed and successful configurations changes. If you observe a sudden change in device behavior, you can check this dashboard to investigate whether a configuration change might be to blame.
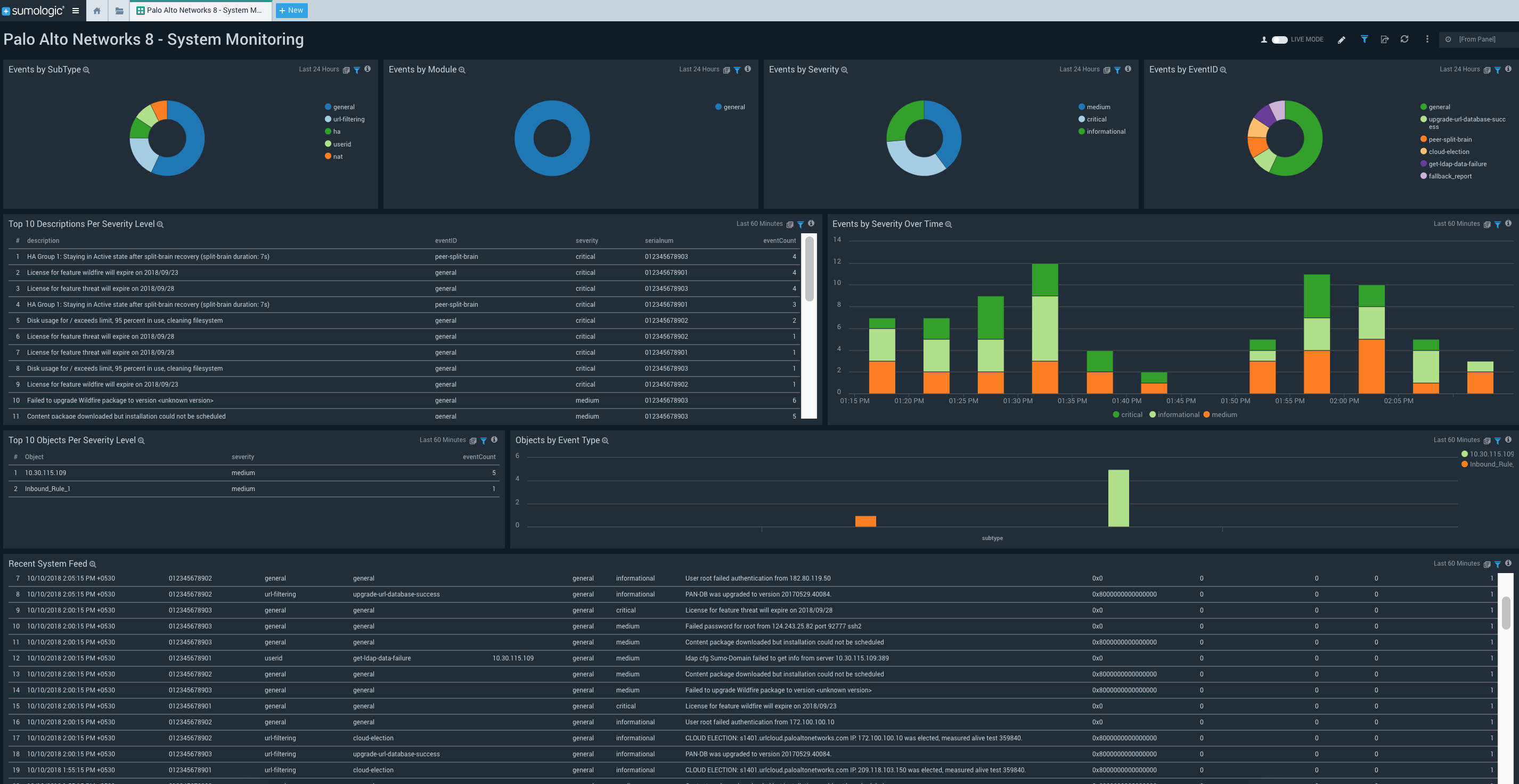
The Palo Alto Networks 8 – System Monitoring dashboard helps identify system issues like hardware failures, HA failures, link down status, dropped connections with external devices, firmware/software upgrades, password change notifications, log in/log off, administrator name or password change, any configuration change, and other minor events.
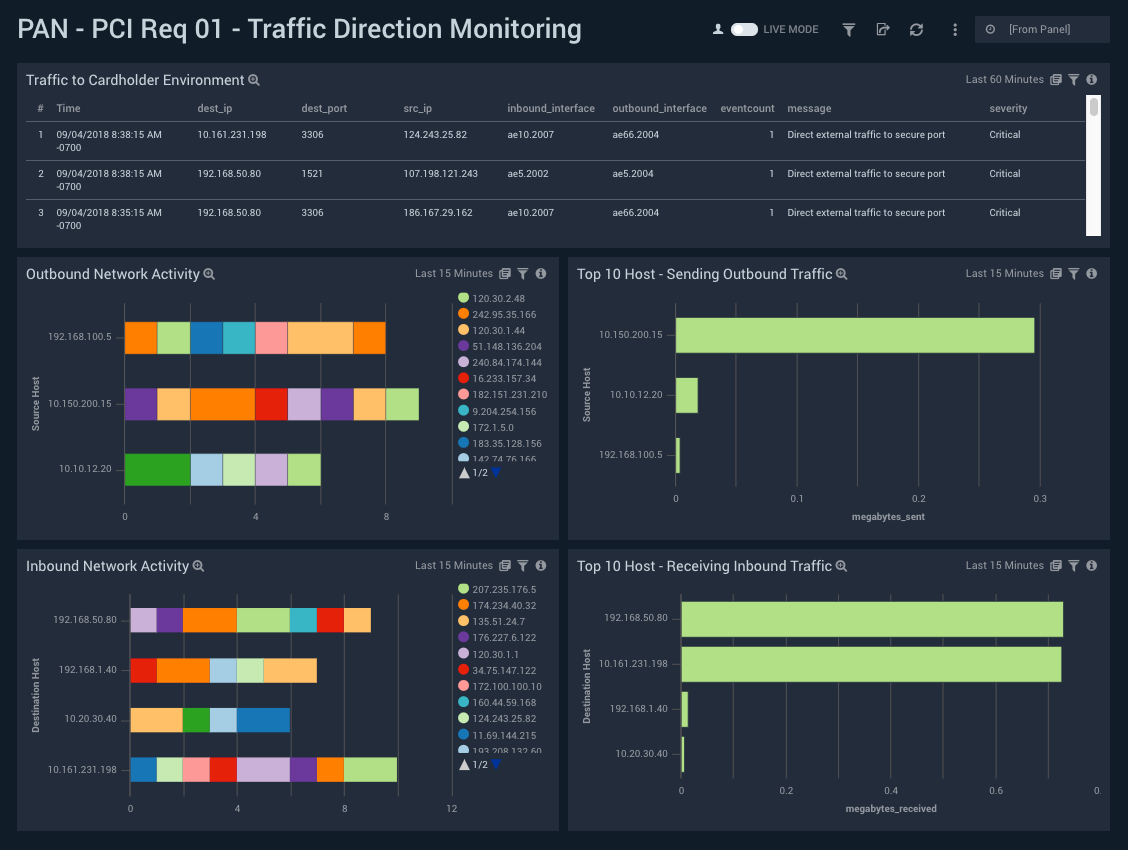
The Sumo Logic App for PCI Compliance
The Sumo Logic PCI Compliance for Palo Alto Networks simplifies PCI compliance audits by targeting compliance regulations in PCI DSS 3 requirements 01, 02 and 04, which include monitoring accepted and rejected traffic, traffic direction, data access and insecure data in transit. Four dashboards are provided with the app specific to each requirement.
Get Started Now!
The Sumo Logic App for Palo Alto Networks and PCI Compliance for Palo Alto Networks analyzes all activity seen by the PAN-OS 8 firewall and gives you advanced insight from a security and compliance perspective.
To get started check out the documentation on Sumo Logic’s DocHub for the Palo Alto Networks 8 app or the PCI Compliance for Palo Alto Networks app. If you don’t yet have a Sumo Logic account, you can sign up for a free trial today.
Additional Resources
- Learn more about Sumo Logic’s PCI Compliance dashboards in this blog.
- Watch the SnapSecChat video with Sumo Logic CSO George Gerchow on why we need to focus on “Security-as-a-Service.”
- Visit our DocHub page for specifics on how Sumo Logic helps support our customer’s PCI compliance needs beyond Palo Alto Networks 8.

